

Rewterz Threat Alert – APT SideWinder Group – Active IOCs
September 30, 2022
Rewterz Threat Alert – Sophisticated Covert Attack Campaign Targeting Military Contractors – Active IOCs
September 30, 2022
Rewterz Threat Alert – APT SideWinder Group – Active IOCs
September 30, 2022
Rewterz Threat Alert – Sophisticated Covert Attack Campaign Targeting Military Contractors – Active IOCs
September 30, 2022Severity
High
Analysis Summary
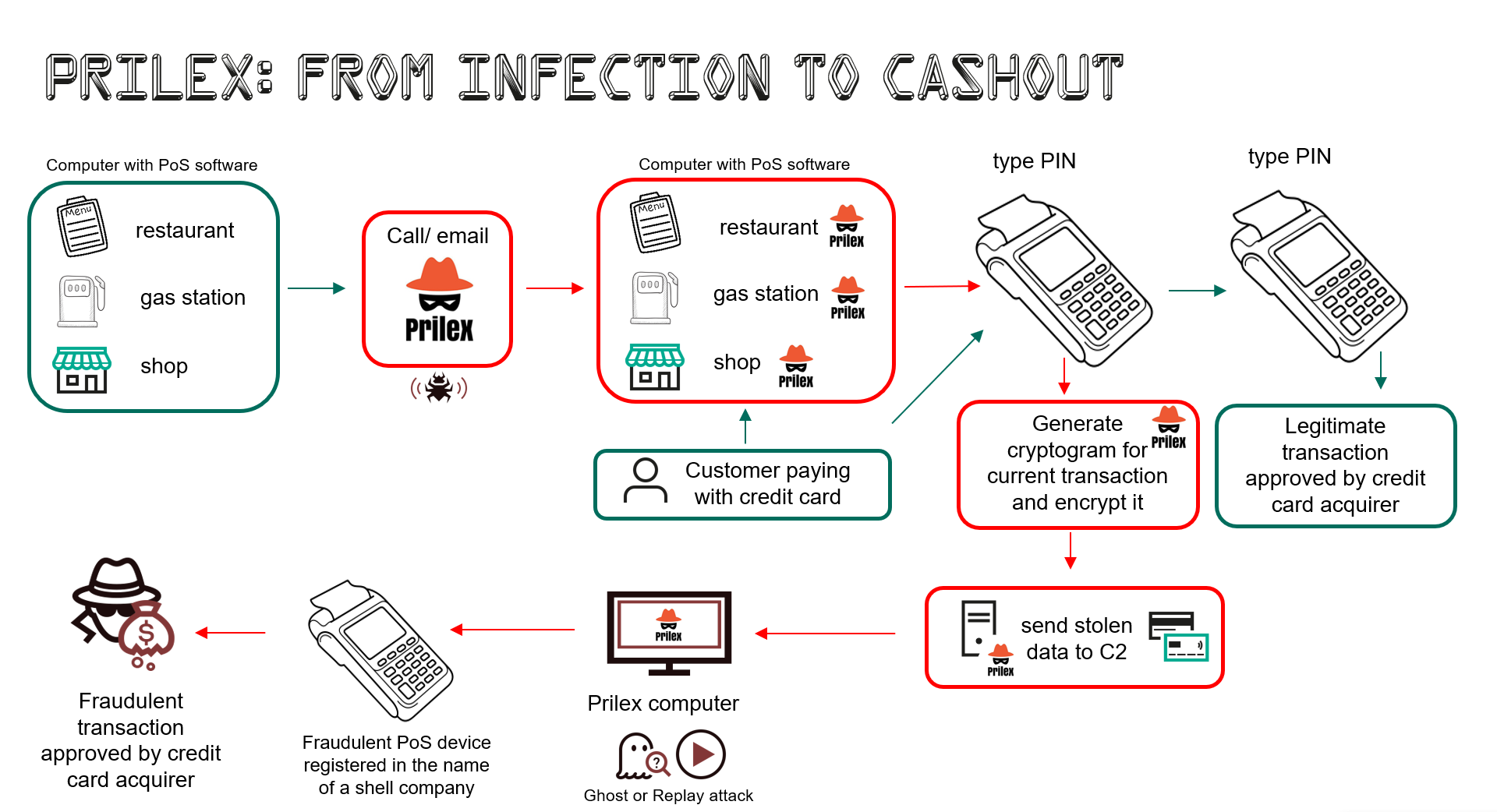
Prilex, a Brazilian threat actor, has emerged with advanced and sophisticated malware designed to steal money through fraudulent transactions. These threat actors have evolved from ATM-focused malware into modular point-of-sale malware.
The gang was responsible for one of the biggest ATM hacks in the nation, cloning more than 28,000 credit cards that were used in these ATMs prior to the huge theft and infecting and jackpotting of over 1,000 machines.

According to the report,
“The Prilex group has shown a high level of knowledge about credit and debit card transactions, and how software used for payment processing works. This enables the attackers to keep updating their tools in order to find a way to circumvent the authorization policies, allowing them to perform their attacks.”
Over the years, Prilex’s strategy has changed to exploit point-of-sale (PoS) software procedures in order to intercept and modify communications with electronic devices like PIN pads, which are used to enable payments using debit or credit cards.
The operators are also skilled at carrying out EMV replay attacks, which include capturing and replaying traffic from a legal EMV-based chip card transaction to a payment processor such as Mastercard, but with the transaction, fields updated to contain stolen card data.
Prilex is not distributed through email spam campaigns. To deploy the malware, a highly focused attack with a social engineering component is required to infect a machine that has PoS software installed.

“A target business may receive a call from a ‘technician’ claiming that the business has to upgrade its PoS software.” The imposter technician may physically visit the target or request that the victims install AnyDesk. As a result, the ‘technician’ may remotely install the infection.
However, research has demonstrated that in new versions, such attacks are being supplanted by methods that utilize cryptograms generated by the victim’s card during the in-store payment procedure.
The approach, known as GHOST transactions, involves a stealer component that intercepts all communications between the PoS software and the PIN pad used for card reading during the transaction in order to retrieve card information. After transmitting to a command-and-control (C2) server. This allows the threat actor to execute transactions by impersonating a PoS device (the device is registered in the name of a fictitious company). Now, whenever a transaction is made EMV chip cards use a cryptogram to secure cardholder data, lowering the probability of counterfeit transactions
The GHOST attack asks for new EMV cryptograms that are used to carry out fraudulent transactions. Compared to previous versions, which got around these security measures to obtain the cryptogram and conduct a replay attack using the gathered “signature.”
The prior versions of Prilex evaded these security measures by monitoring the current transaction to get the cryptogram and execute a replay attack using the gathered “signature.” whereas GHOST attacks ask for fresh EMV cryptograms that are used to carry out fraudulent transactions.
“The Prilex PoS malware evolved out of a simple memory scraper into very advanced and complex malware, dealing directly with the PIN pad hardware protocol instead of using higher level APIs, doing real-time patching in target software, hooking operating system libraries, messing with replies, communications and ports, and switching from a replay-based attack to generate cryptograms for its GHOST transactions even from credit cards protected with CHIP and PIN technology.”
Researchers strongly suggest that PoS software developers implement self-protection techniques in their modules,
The techniques include a Software Development kit whose purpose is to keep malicious code from interfering with the transactions controlled by those modules.
Impact
- Fraudulent Transactions
- Card Information Theft
- Sensitive Information Theft
Remediation
- PoS software developers implement self-protection techniques in their modules
- The techniques include a Software Development kit whose purpose is to keep malicious code from interfering with the transactions controlled by those modules.
- Follow the VMware’s published guidance for protecting vSphere environments from similar threats.
- Passwords – Ensure that general security policies are employed including: implementing strong passwords, correct configurations, and proper administration security policies.
- Admin Access – limit access to administrative accounts and portals to only relevant personnel and make sure they are not publicly accessible.
- WAF – Web defacement must be stopped at the web application level. Therefore, set up a Web Application Firewall with rules to block suspicious and malicious requests.
- Patch – Patch and upgrade any platforms and software timely and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Secure Coding – Along with network and system hardening, code hardening should be implemented within the organization so that their websites and software are secure. Use testing tools to detect any vulnerabilities in the deployed codes.
- 2FA – Enable two-factor authentication.
- Antivirus – Enable antivirus and anti-malware software and update signature definitions in a timely manner. Using a multi-layered protection is necessary to secure vulnerable assets
- Security Best Practices – Do not open emails and attachments from unknown or suspicious sources.








