

Rewterz Threat Alert – Threat Actors From Brazil’s Prilex Group Resurfaced With Sophisticated Point-of-Sale (PoS) Malware
September 30, 2022
Rewterz Threat Alert – Phobos Ransomware – Active IOCs
September 30, 2022
Rewterz Threat Alert – Threat Actors From Brazil’s Prilex Group Resurfaced With Sophisticated Point-of-Sale (PoS) Malware
September 30, 2022
Rewterz Threat Alert – Phobos Ransomware – Active IOCs
September 30, 2022Severity
High
Analysis Summary
A recent cyberattack campaign that may have been motivated by cyber espionage targeted many military and weapons contractor businesses using spear-phishing emails to start a multi-stage infection process meant to deliver an unidentified payload on infected workstations.
In recent months, this covert effort has targeted many European weapons firms, including a potential supplier to the US F-35 Lightning II fighter aircraft programs.
Researchers claim that the attack began in late summer 2022, with at least two prominent military contractor firms as its primary targets.
A phishing email with a ZIP archive attachment that contains a shortcut file posing as a PDF document on “Company & Benefits” is the first step in its infection chain. This file is then used to retrieve a stager, an initial binary that is used to download the required malware, from a remote server.
When the user executes the .lnk file, a robust chain of stagers will start to run. Each stager is written in PowerShell and is tightly obfuscated. Eight different stages or layers were observed in all, each with a variety of tactics.
The last section of code downloads, decrypts, and executes a remote payload called “header.png” from the URL “terma[.]app/s/static/img/header.png”.
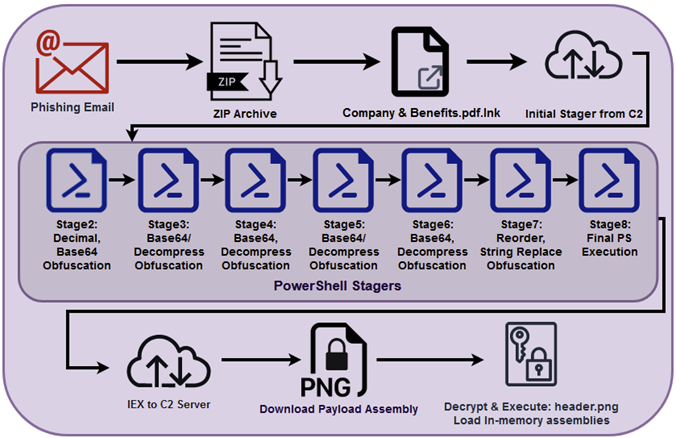
“While we were able to download and analyze the header.png file, we were not able to decode it as we believe the campaign was completed and our theory is that the file was replaced in order to prevent further analysis. Our attempts to decode the payload would only produce garbage data.”
The use of obfuscated code to prevent examination, as well as scanning for the existence of debugging tools and stopping the execution if the system language is set to Chinese or Russian, are important aspects of its method of operation.
“If the system’s language is set to “*zh*” (Chinese) or to “*ru*” (Russian), then the code will simply exit and the computer will shut down.”
The malware is also programmed to check the physical memory, and if it is less than 4GB, it will silently shut down the machine it is now running on. The malicious script will start deactivating detection engines starting with PowerShell Script Block Logging if all the checks are passed.
When all of these checks pass, the PowerShell stager continues by turning off logging, adding Windows Defender exclusions for LNK, RAR, and EXE files, and establishing persistence through changes to the Windows Registry or a scheduled job.
They concluded the report with
Overall, it is clear that this attack was relatively sophisticated with the malicious threat actor paying specific attention to opsec. There were a lot of relatively recent attack techniques at play, some of which were unfamiliar and required additional analysis such as leveraging the PowerShell Get-Alias commandlet to perform an invoke expression.
Impact
- Payload Deployment
Indicators of Compromise
Domain Name
- terma[.]dev
- terma[.]app
- terma[.]vip
- terma[.]wiki
- terma[.]pics
- terma[.]lol
- terma[.]ink
- cobham-satcom[.]onrender[.]com
Remediation
- Researchers also share the recommendations and mitigations:
- Avoid downloading lnk files or unexpected email attachments from unreliable sources.
- Use block logging in PowerShell scripts to assist with detections
- Improve log coverage by deploying extra process-level logging, such as Sysmon. Furthermore, sysmon installed on the host will prevent the next stage payload from being executed.
- Pay close attention to any efforts to shut off your security monitoring software, such as SIEM.
- Passwords – Ensure that general security policies are employed including: implementing strong passwords, correct configurations, and proper administration security policies.
- Admin Access – limit access to administrative accounts and portals to only relevant personnel and make sure they are not publicly accessible.
- WAF – Web defacement must be stopped at the web application level. Therefore, set up a Web Application Firewall with rules to block suspicious and malicious requests.
- Patch – Patch and upgrade any platforms and software timely and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Secure Coding – Along with network and system hardening, code hardening should be implemented within the organization so that their websites and software are secure. Use testing tools to detect any vulnerabilities in the deployed codes.
- 2FA – Enable two-factor authentication.
- Antivirus – Enable antivirus and anti-malware software and update signature definitions in a timely manner. Using a multi-layered protection is necessary to secure vulnerable assets
- Security Best Practices – Do not open emails and attachments from unknown or suspicious sources.
- Block all threat indicators at your respective controls.
- Search for Indicator of compromise (IOCs) in your environment utilizing your respective security controls








