

Rewterz Threat Alert – RATicate – Information-Stealing Malware
May 19, 2020
Rewterz Threat Advisory – CVE-2019-15083 – Zoho ManageEngine ServiceDesk Plus Vulnerability
May 19, 2020
Rewterz Threat Alert – RATicate – Information-Stealing Malware
May 19, 2020
Rewterz Threat Advisory – CVE-2019-15083 – Zoho ManageEngine ServiceDesk Plus Vulnerability
May 19, 2020Severity
Medium
Analysis Summary
Microsoft Teams is being used as a lure in a phishing campaign discovered by researchers that is taking advantage of an increased remote workforce. The body of the phishing email is almost identical to a legitimate Microsoft Teams notification email. The subject line is different and, significantly, the sender is not a Microsoft email address. The link in the body of the email points to a campaign-archive.com URL. This page provides a secondary link to supposedly view an unread Microsoft Teams message. Victims who click this link are redirected to a copy of the Microsoft login page. After entering credentials into the fake form and hitting submit, victims are further redirected to the legitimate Office website. At this point, the entered credentials were likely exfiltrated to the threat actors.
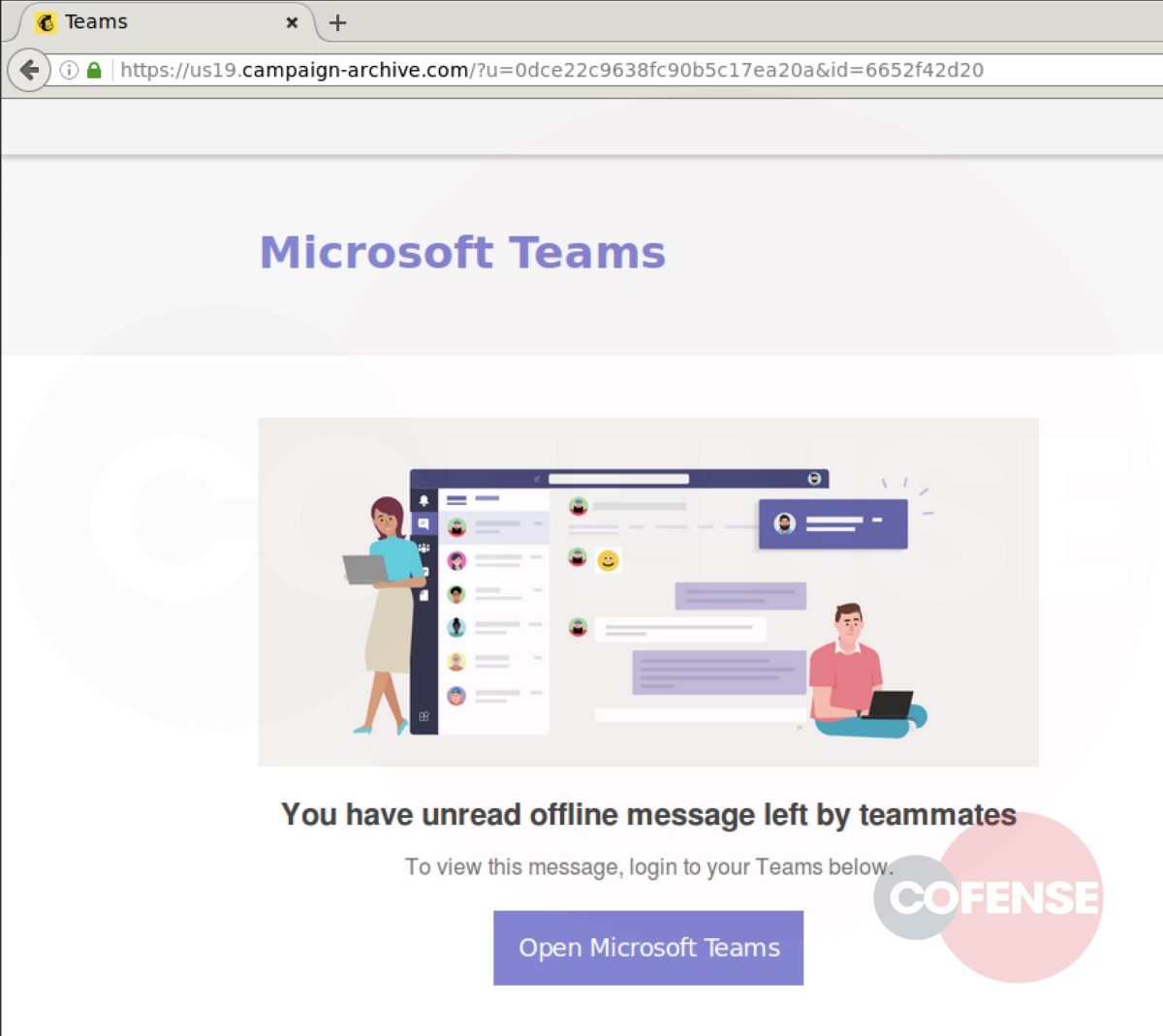
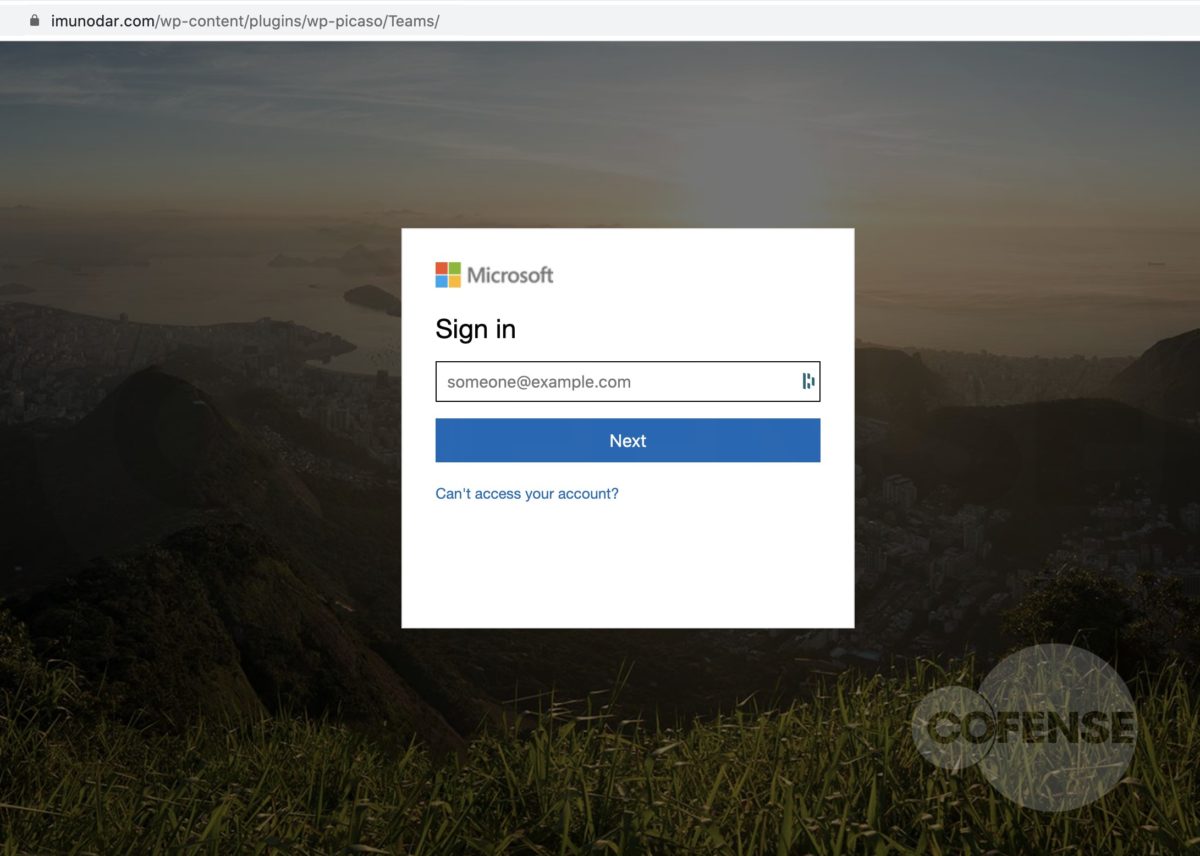
Impact
- Credential theft
- Exposure of sensitive data
Indicators of Compromise
IP
104[.]118[.]190[.]227
URL
- hXXps[:]//us19[.]campaign-archive[.]com/?u=0dce22c9638fc90b5c17ea20a&id=6652f42d20
- hXXps[:]//imunodar[.]com/wp-content/plugins/wp-picaso/Teams/
Remediation
- Block all threat indicators at your respective controls.
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/attachments sent by unknown senders.








