

Rewterz Threat Alert – ServHelper Backdoor
July 14, 2020
Rewterz Threat Advisory – ICS: Advantech iView
July 15, 2020
Rewterz Threat Alert – ServHelper Backdoor
July 14, 2020
Rewterz Threat Advisory – ICS: Advantech iView
July 15, 2020Severity
High
Analysis Summary
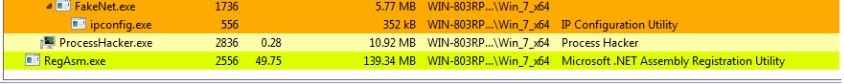
Researchers have analyzed the M00nD3V Logger, a new information stealing Trojan with wide functionality. The Trojan is marketed on hacking forums and sold using a subscription structure. Customers are distributing the payload via various methods, including spam email and compromised websites. The initial file is a .NET executable that kicks off the infection process by launching a loader. This loader unpacks and decrypts the main M00nD3V Logger payload, which runs under the RegAsm.exe process. The malware then begins initializing its configuration. First, anti-debugging checks are performed and botnet and antivirus killers are run. Persistence is established via a Registry Run key. Hardcoded credentials that will be used for exfiltration are decrypted. Lastly, privilege escalation is performed as necessary. Additionally, the BouncyCastle crypto package is downloaded and loaded into memory. In terms of data collection, M00nD3V Logger is capable of gathering passwords from 42 applications (email clients, browsers, FTP clients, and more) and capturing keystrokes, clipboard data, and webcam pictures. The gathered data is then encrypted with the BouncyCastle crypto package and can be exfiltrated via SMTP, FTP, or proxy. The credentials and destination addresses for these methods are set during the configuration initialization process.
Impact
- Information theft
- Exposure of sensitive data
Indicators of Compromise
MD5
bf8801bcd5a196744ccd0f863f84df71
SHA-256
c23b33ddb4e0cfa52b9242648f5cb7a6ee916b4ba1e6f547d8d5ef543dccbb9d
SHA1
bffcc8dd81006a641818d125e691b5b6157c8619
Remediation
- Block all threat indicators at your respective controls.
- Search for IOCs in your environment.








