

Rewterz Threat Alert – Nanocore RAT – IOCs
October 1, 2020
Rewterz Threat Alert – SLOTHFULMEDIA RAT Used to Target Organizations in Multiple Countries
October 2, 2020
Rewterz Threat Alert – Nanocore RAT – IOCs
October 1, 2020
Rewterz Threat Alert – SLOTHFULMEDIA RAT Used to Target Organizations in Multiple Countries
October 2, 2020Severity
Medium
Analysis Summary
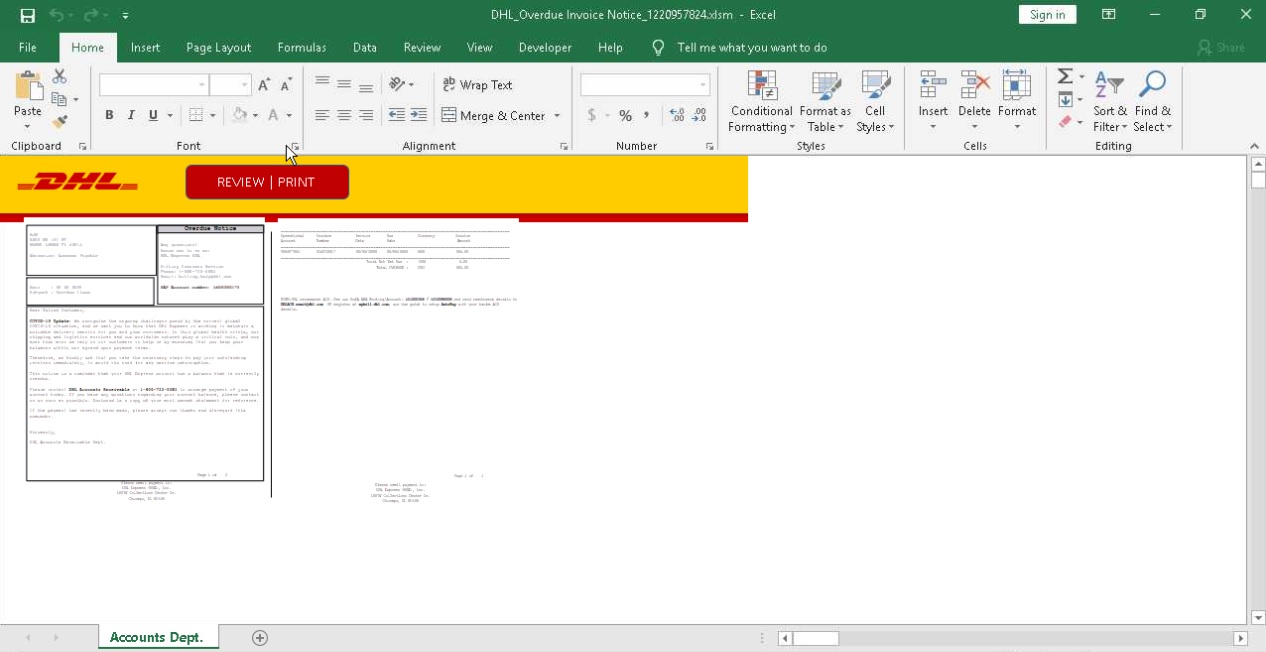
Dridex banking trojan is actively being used in cyber attacks, often spoofing brands to deliver their phishing emails with malicious attachments. The recent Dridex campaign was found spoofing FedEx whereas the current Dridex campaign spoofs DHL. The spam emails arrive with the subject “DHL Overdue Invoice Notice – 1220957824” from the spoofed email address ‘noreply@dhl[.]com’. Dridex is still using an anti-debugging technique to postpone execution and evade analysis. Dridex also no longer delivers payloads to Windows 7 operating systems. DHL International GmbH is a German courier, parcel, and express mail service which is now operating in many countries.
Impact
- Theft of sensitive information
- Financial loss
Indicators of Compromise
Domain Name
- workspace[.]kevinmccollow[.]com
- globalmmk[.]vanilija[.]eu
- vdyzel[.]ootw[.]co[.]za
- krisbadminton[.]com
- tessrobins[.]com
- salongifts[.]co[.]uk
- warriorsicehockey[.]co[.]za
- vashikaranforlostloveback[.]com
- paraglidingvn[.]com
- saintignatiouscollege[.]co[.]za
- negatu[.]com
- razoesesolucoes[.]com
- uklearningtoys[.]co[.]uk
- muscleman[.]co[.]za
- mxsouthafrica[.]com
- bonresa[.]com
- mertenslawyers[.]com[.]au
- jdsuministroseinstalaciones[.]com
- mdqassessing[.]co[.]za
- no18balloonroom[.]co[.]uk
- eddyvanijken[.]nanopoint[.]nl
- lab2[.]e-century[.]pl
- webpower[.]pdc-ind[.]com
- adm[.]snpsresidential[.]com
- rop[.]technomatica[.]ovh
- 2203610[.]projects-airnetwork[.]asia
- push[.]qnotice[.]com
- igniter[.]fobbly[.]net
- ws4polisi[.]pdc-ind[.]com
- twomissa[.]com
- seminelogistics[.]com
- rubbermounted[.]com[.]au
- zaaher[.]com
- visualhome[.]cl
- safer[.]com[.]gt
- flowpressurewashing[.]com
- therightcyclingcompany[.]com
- ramec[.]com[.]au
- raybadenergy[.]com
- tensopret[.]com
- thulilekhanyile[.]co[.]za
- nemzetiaranyintezet[.]com
- galileedream[.]hu
- poligrafiascali[.]com
MD5
- 155c990dfb8e9456d6b44f3c01a3699b
- 206803daf8a8c1459c8d597e5250b993
- 04a9ccacf4624414058ac503d2d7b60b
- 8c1c54884b90c015330ef19c0cb0a4fc
SHA-256
- 9852a64ff8dd64e99326dc917c70b9b68c1e80128260035fdae275bf5fc66972
- 58242c08ab978824f9ebbe4fb48a80dde5c7e59d0489caf73328a7eec599415c
- 30ddf8d34671494f41ef339a36a9a91d8593a297c299c16603c73e1842486284
- f045bc5d0dc4890be3163fa236c403dab3d444e92fd5ddc0356dbf3f25f829af
SHA1
- b3e46cd16f750440b8b3ac2eaec082417bd1c97d
- 5905e986acf1effcdc223f842aafc09ec77d0d73
- a2ad662de7d5a398817075031f3d78b6afd9cbf2
- e222675107a78e19648479a3a994f63fcc58f2a2
Source IP
- 69[.]16[.]193[.]166
- 193[.]90[.]12[.]122
- 146[.]164[.]126[.]197
- 157[.]245[.]103[.]132
URL
- https[:]//push[.]qnotice[.]com/g0tjfzqv[.]gif
- https[:]//2203610[.]projects-airnetwork[.]asia/a90f1ofe[.]txt
- https[:]//tensopret[.]com/cmgvr3[.]rar
- https[:]//rubbermounted[.]com[.]au/uua8c4dp[.]jpg
- https[:]//zaaher[.]com/tb6lhp2w[.]pdf
- https[:]//raybadenergy[.]com/pl4bjbk[.]rar
- https[:]//poligrafiascali[.]com/gqd0p1o[.]rar
- https[:]//thulilekhanyile[.]co[.]za/tdatkb8d[.]zip
- https[:]//rop[.]technomatica[.]ovh/qgmltk[.]zip
- https[:]//flowpressurewashing[.]com/ggc1ljvn[.]rar
- https[:]//therightcyclingcompany[.]com/nobc7tpjo[.]txt
- https[:]//igniter[.]fobbly[.]net/a50po6[.]pdf
- https[:]//lab2[.]e-century[.]pl/llzdgu8[.]pdf
- https[:]//eddyvanijken[.]nanopoint[.]nl/oipl8e[.]gif
- https[:]//safer[.]com[.]gt/nb5dagc5[.]jpg
- https[:]//2203610rwd[.]projects-airnetwork[.]asia/iihpacd[.]jpg
- https[:]//webpower[.]pdc-ind[.]com/p49tb4[.]rar
- https[:]//nemzetiaranyintezet[.]com/hookt7ndw[.]txt
- https[:]//weddingcakes[.]buffaloonlinetest[.]co[.]uk/pbke90uuk[.]txt
- https[:]//ws4polisi[.]pdc-ind[.]com/gpce8r54[.]gif
- https[:]//adm[.]snpsresidential[.]com/btskh3o[.]zip
- https[:]//seminelogistics[.]com/zsjm5zv7k[.]jpg
- https[:]//visualhome[.]cl/yphtdaej[.]zip
- https[:]//count[.]mail[.]163[.]com[.]impactmedfoundation[.]com/fn58ds[.]pdf
- https[:]//ramec[.]com[.]au/gayrmv4m2[.]txt
- https[:]//galileedream[.]hu/e82011[.]txt
- https[:]//twomissa[.]com/bdodfvr1[.]rar
Remediation
- Block the threat indicators at their respective controls.
- Do not download files attached in emails coming from untrusted sources.








