

Rewterz Threat Alert – Emotet Distribution in Password-Protected Zip-Files
September 22, 2020
Rewterz Threat Advisory – CVE-2020-12811 – FortiManager and FortiAnalyzer cross-site scripting
September 22, 2020
Rewterz Threat Alert – Emotet Distribution in Password-Protected Zip-Files
September 22, 2020
Rewterz Threat Advisory – CVE-2020-12811 – FortiManager and FortiAnalyzer cross-site scripting
September 22, 2020Severity
Medium
Analysis Summary
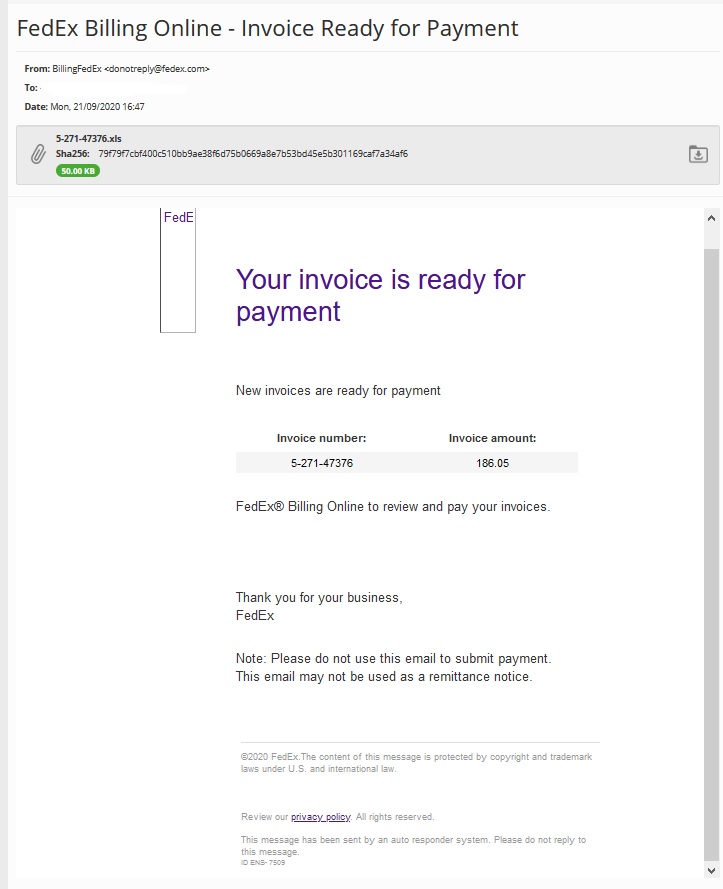
This Dridex campaign spoofs FedEx. FedEx Corporation, short for Federal Express, is an American multinational delivery services company headquartered in Memphis, Tennessee. The spam emails arrive with the subject “FedEx Billing Online – Invoice Ready for Payment” from the spoofed email address ‘donotreply@fedex[.]com’. Dridex is still using an anti-debugging technique to postpone execution and evade analysis. Dridex also no longer delivers payloads to Windows 7 operating systems. It appears English-speaking countries and Italy are currently the primary targets of this campaign.
Impact
- Theft of sensitive information
- Financial loss
Indicators of Compromise
Domain Name
- retrodays[.]pt
- starsignsdates[.]com
- stepco[.]ro
- mazimimarlik[.]com
- laptopsservicecenter[.]in
Email Subject
- FedEx Billing Online – Invoice Ready for Payment
Hostname
- mail[.]168vitheyrealestate[.]com
- lamesuspendue[.]swayb[.]com
- skybeetravels[.]cheapflightso[.]co[.]uk
- cdn[.]applimmo[.]com
- update[.]cabinetulieru[.]ro
MD5
- 8ba9311dd06f6f9e88110e4b18a8206c
- 9bce97f19e31a1e3b783ac32d2c726fa
- 33227543c947be9bd3164acf020b3d3c
- 3df66d4122cd8692da6422fd16d0c1a4
- 6cbb4d461e744cb036b732c72066a041
- da89cf3606cd723551524a0f64ba76de
- cb27c5769a861eb71b317636172569bf
- 3e2c17ac397a0edfc3262a6e87e3fdea
SHA-256
- 982a3c6dda59afa109d2f596ad59ba1330d0c45aa7b6068e7c5c5e15d8fca878
- 2d7c7b9472f1f4bb2f678822f16e8575971574ba763bd9e98fdb7d8b2a8f5d2e
- 79f79f7cbf400c510bb9ae38f6d75b0669a8e7b53bd45e5b301169caf7a34af6
- 3259221b5378b9c9a983ae265527662c0c7856f6664a9a734754f549ee4d7a33
- 55067d633bef8350b5de24e3e9f153fc4a6765af0af168fb444a6329c701b10a
- 5b4337f9ae1d91113c91abd0da39794d8aa216b149562440de541ca99618840d
- 8a7cc23e3b7af9ebd2d1dd3791bb62bd1da1efd3d2c480fa51483552520abd0a
- eb3c152be59903d29cf02100ed2f9edea183a37882a68ae5655bcbc9004775d8
SHA1
- b4ec3851352653b4a73536ce5b1f810427266cb4
- 77b24c8ba771792da6aec76f4ec248f0ecb235c3
- 48b9bf7516c29bd896307e294f32d10b1aa879d1
- 281211783851fcc2323ac8d1fa66a09789289bb7
- e16f8033923ab6d3e5ab80088836fd3d86e46ef4
- 8b6b1dd793811066522e4a1b86858dee09a37faf
- 0b4e19d486addaad69b8273632d9bcf2f3ccf631
- badefe11fc6a9c351a5a570742cc7a2fb385235e
Source IP
- 109[.]169[.]24[.]37
- 51[.]75[.]24[.]85
URL
- https[:]//mail[.]168vitheyrealestate[.]com/k5hkyj0[.]zip
- https[:]//cdn[.]applimmo[.]com/wxmn5b[.]pdf
- https[:]//retrodays[.]pt/lhtzu8p[.]zip
- https[:]//starsignsdates[.]com/hurxlu8[.]pdf
- https[:]//stepco[.]ro/wij87mvg[.]txt
- https[:]//skybeetravels[.]cheapflightso[.]co[.]uk/py198k[.]pdf
- https[:]//mazimimarlik[.]com/ow1oorywn[.]pdf
- https[:]//laptopsservicecenter[.]in/s3k9ebe2[.]pdf
- https[:]//lamesuspendue[.]swayb[.]com/pxxnmie14[.]zip
- https[:]//update[.]cabinetulieru[.]ro/thhqpn[.]txt
- http[:]//cdn[.]applimmo[.]com/wxmn5b[.]pdf
Remediation
- Block the threat indicators at their respective controls.
- Do not download files attached in emails coming from untrusted sources.








