

Rewterz Threat Advisory -CVE-2019-13945 – ICS: Siemens S7-1200 CPU
November 15, 2019
Rewterz Threat Alert – Android Malware – IMobile-VERIFY Leverages Financially Motivated Cyber Attacks
November 15, 2019
Rewterz Threat Advisory -CVE-2019-13945 – ICS: Siemens S7-1200 CPU
November 15, 2019
Rewterz Threat Alert – Android Malware – IMobile-VERIFY Leverages Financially Motivated Cyber Attacks
November 15, 2019Severity
High
Analysis Summary
TA2101 is found targeting German companies and organizations to deliver and install backdoor malware. This actor is distributing Maze ransomware through Microsoft Word attachments, which when opened execute a Microsoft Office macro that, in turn, executes a PowerShell script, which downloads and installs the Maze ransomware payload onto the victim’s system.
The lure appears to be a notification of law enforcement activities (“aggiornamento: attivita di contrasto all’evasione”) and states that the recipient should open and read the enclosed document in order to avoid further tax assessment and penalties.
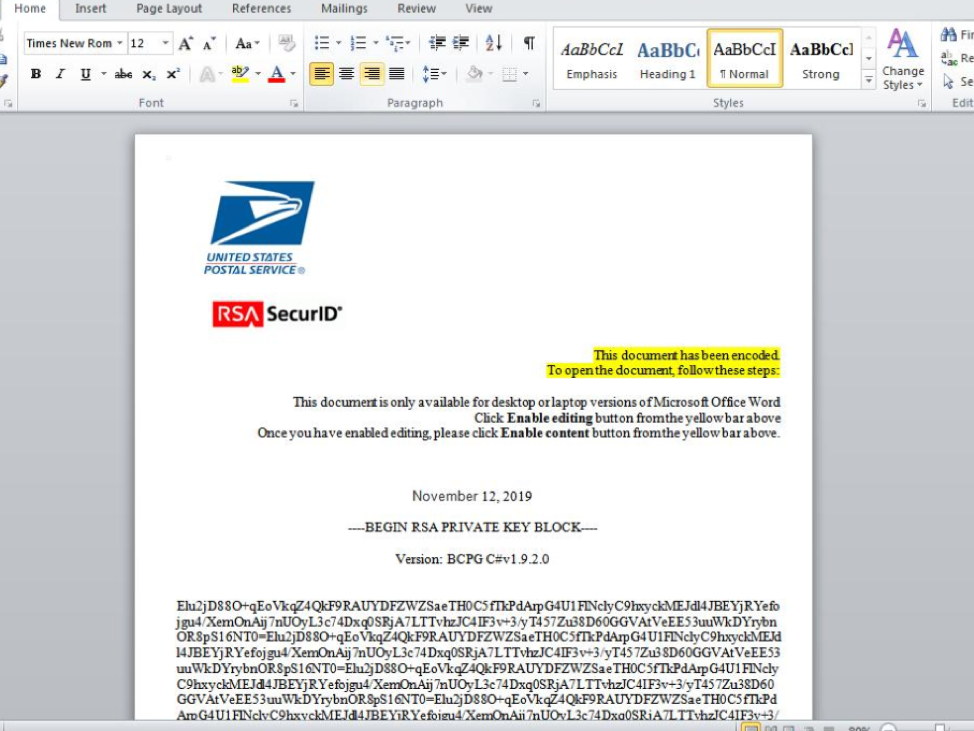
The emails, as part of a low-volume campaign across multiple verticals, were targeted primarily at manufacturing companies, businesses and IT service companies and used an infection chain of Microsoft Office macros into a PowerShell script, which ultimately downloads and installs Maze ransomware. Opening the Microsoft Word Document and enabling macros installs Maze ransomware on the user’s system, encrypting all of their files, and saves a ransom note resembling the following in TXT format in every directory.
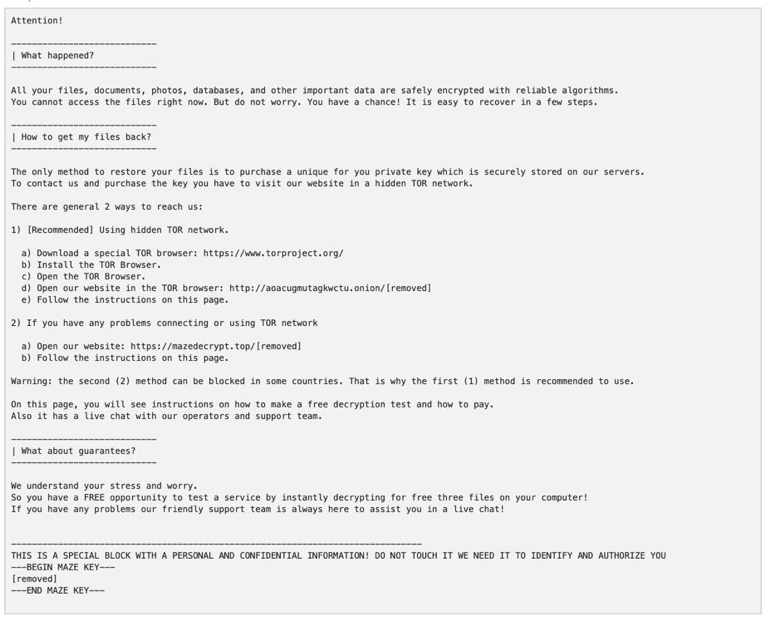
Impact
- Financial loss
- Files Encryption
Indicators of Compromise
Domain Name
agenziaentrate[.]icu
From Email
- antowortensienicht@bzst-infomieren[.]icu
- info@agenziaentrate[.]icu
- antwortensienicht@bzstinform[.]icu
MD5
- 80043a5b285da88fb63d469243655751
- 53d5bdc6bd7904b44078cf80e239d42b
- ad30987a53b1b0264d806805ce1a2561
- 1ffecd461b3d4b65e44faff8537f68d6
- c09af442e8c808c953f4fa461956a30f
- ee26e33725b14850b1776a67bd8f2d0a
- 2fbd10975ee65845a18af6b7488a5236
SH256
- 44991186a56b0d86581f2b9cc915e3af426a322d5c4f43a984e6ea38b81b7bed
- cfd8e3a47036c4eeeb318117c0c23e126aea95d1774dae37d5b6c3de02bdfc2a
- 9f2139cc7c3fad7f133c26015ed3310981de26d7f1481355806f430f9c97e639
- 5f1e512d9ab9b915b1fc925f546ed559cbfa49df53229e2f954a1416cf6f5ee4
- 97043f23defd510607ff43201bb03b9916a23bd71b5bdf97db357e5026732506
- d617fd4b2d0824e1a7eb9693c6ec6e71447d501d24653a8e99face12136491a8
- 7e3ab96d2628e0a9970802b47d0356dc9b99994d7f98492d4e70a5384891695a
URL
- hxxp[:]//198.50.168.67/wordpack[.]tmp
- hxxp[:]//conbase.top/sys[.]bat
- hxxp[:]//104.168.198[.]208/wordupd.tmp
- hxxp[:]//104.168.215[.]54/wordupd.tmp
- hxxp[:]//104.168.174[.]32/wordupd_3.0.1.tmp
- hxxp[:]//192.119.68[.]225/wordupd1.tmp
- hxxp[:]//108.174.199[.]10/wordupd3.tmp
- hxxp[:]//54.39.233[.]175/wupd19823.tmp
- hxxp[:]//54.39.233[.]131/word1.tmp
- hxxp[:]//104.168.198[.]230/wordupd.tmp
Remediation
- Block the threat indicators at their respective controls.
- Do not download files attached in untrusted emails.
- Do not enable macros for untrusted files.








