

Rewterz Threat Advisory – CVE-2020-10633 – ICS: HMS Networks eWON Flexy and Cosy Cross-site Scripting Vulnerability
April 8, 2020
Rewterz Threat Alert – Pekraut-RAT
April 8, 2020
Rewterz Threat Advisory – CVE-2020-10633 – ICS: HMS Networks eWON Flexy and Cosy Cross-site Scripting Vulnerability
April 8, 2020
Rewterz Threat Alert – Pekraut-RAT
April 8, 2020Severity
Medium
Analysis Summary
A malicious executable, researchers identified a new German RAT, “Pekraut.” The first sample was packed using ConfuserEx and, like a secondary unpacked sample they discovered, used Dotfuscator for obfuscation. The RAT is installed under a system process named, “svchost.exe “, and persistence is established using both the Winlogon Shell Registry key and a shortcut file in the startup folder masquerading as an Internet Explorer Update. The process to uninstall will clean up these artifacts by restoring the default Registry value and deleting the shortcut. Furthermore, the exact installation behavior, such as the filenames and installation path, can be adjusted using different flags. Once installed, the malware performs a UAC bypass using the ComputerDefaults.exe method. Communication with its C2 server is performed via a socket connection and leverages a port-forwarding service to hide the attacker’s IP address. Text data is encrypted using AES encryption while other data types are compressed using zlib.
Pekraut is feature-rich and allows for 27 different commands to be accepted from the C2 server, including a help command that provides a description for the commands in German. Commands include those for file, process, and registry operations, gathering system information, performing reconnaissance, and more.
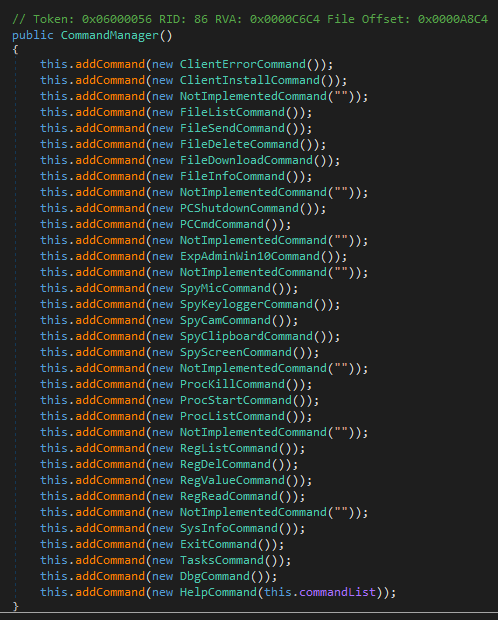
Impact
- Information theft
- Exposure of sensitive data
Indicators of Compromise
MD5
- b990c53433916c4ab56257227e780ba3
- d7745c4a7e90a9a1b22fc12d41f5e2e1
- 0f0dac17b360244a91f55d1cc0362c88
- 3c28c999d54ca33f75706a27219f0167
SHA-256
- 2dab95abe3460e34954527e88223662a03512938a9a28ab57e7f0a8ec298f367
- 4a89c3676dd86531c1fefb4e76d49cc31dc07a1a68c149dd08967e6fd7f6135a
- 9dfffcbfb6537dc051b60f630ed1cd3f768bb0024a8e998752ab9ef6f4c30c65
- cbc500b76995d36c76d04061c58ceaf93a1880af32be494e5ac1e099663ed0fd
SHA1
- a3557eac7cc20cd284ff1fed49e04ebb5b15c734
- 348c7262e61db4ff20b76dd835029bdb42efdad0
- 2f9b0396a0b8c8a84266893fd449192bba4d9de9
- bab62dafe69a526c9cd9de314c835897441b2e1e
Remediation
- Block all threat indicators at your respective controls.
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/attachments sent by unknown senders.
- Search for IOC’s in your existing environment.








