

Rewterz Threat Advisory – CVE-2018-0296 – Cisco ASA and FTD Bug Attacked in Wild for DoS and Information Disclosure
March 11, 2020
Rewterz Threat Advisory – OpenSMTPD Vulnerability (CVE-2020-8794) Can Lead to Root Privilege Escalation and Remote Code Execution
March 13, 2020
Rewterz Threat Advisory – CVE-2018-0296 – Cisco ASA and FTD Bug Attacked in Wild for DoS and Information Disclosure
March 11, 2020
Rewterz Threat Advisory – OpenSMTPD Vulnerability (CVE-2020-8794) Can Lead to Root Privilege Escalation and Remote Code Execution
March 13, 2020Severity
High
Analysis Summary
A new campaign now called “Operation Overtrap” is found infecting victims with its payload. Online Banking Users are being targeted Via Bottle Exploit Kit and Brand-New Cinobi Banking Trojan. The campaign mainly targets online users of various Japanese banks by stealing their banking credentials using a three-pronged attack. The campaign uses three different attack vectors to steal its victims’ banking credentials:
• By sending spam emails with a phishing link to a fake banking website
• By sending spam emails asking victims to execute a disguised malware’s executable downloaded from a linked phishing page.
• By using a custom exploit kit to deliver malware via malvertising
Below is the work flow of operation overtrap.
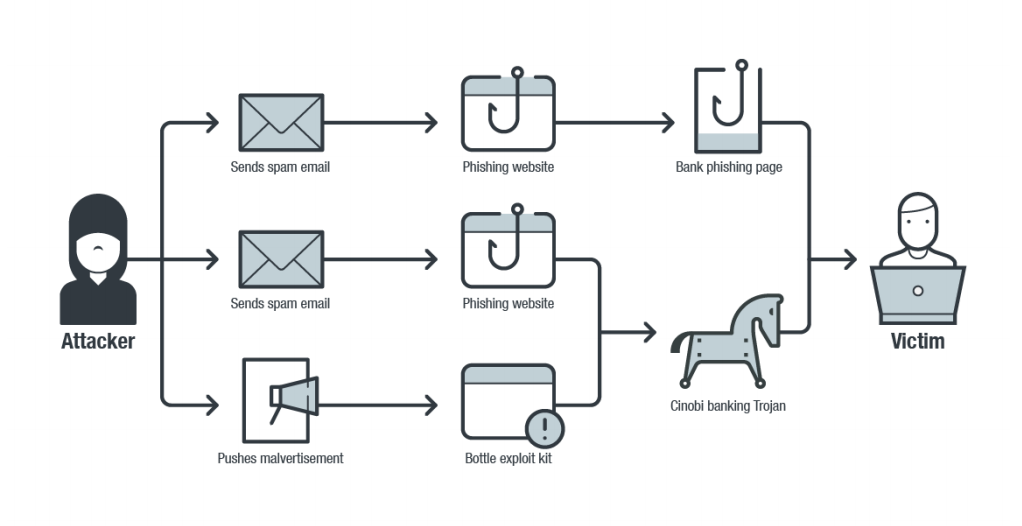
It exploits CVE-2018-15982, a Flash Player use after free vulnerability, as well as CVE-2018-8174, a VBScript remote code execution vulnerability. Victims will be infected with BottleEK’s payload if they access this particular exploit kit’s landing page with unpatched or outdated browsers.
Cinobi has two versions — the first one has a DLL library injection payload that compromises victims’ web browsers to perform form-grabbing. This Cinobi version can also modify web traffic sent to and received from targeted websites. Our investigation found that all the websites that this campaign targeted were those of Japan-based banks. Aside from form-grabbing, it also has a webinject function that allows cybercriminals the ability to modify accessed webpages. The second version has all the capabilities of the first one plus the ability to communicate with a command-and-control (C&C) server over the Tor proxy.
Impact
- Credential Theft
- Information Theft
- Manipulation of web pages
Indicators of Compromise
Domain Name
- bank-japanpostjp[.]com
- ts3cardd[.]com
- safety-amazon[.]jp
- jp-bank-japanossts[.]jp
- jp-bamk[.]jp
- security-amazon[.]jp
- japanp0st[.]jp
- bank-japanpost[.]com
- bank-japanpostpo[.]jp
- safetb-amazon[.]jp
- bank-japanposst[.]jp
- view[.]inteleksys[.]com
- cionx[.]inteleksys[.]com
- shop[.]inteleksys[.]com
- priv[.]inteleksys[.]com
MD5
- d938fa218caf1348b1a4851eb99ed6dd
- 14ee556ef1d4451857365cc0cf407ddf
- 0c206094d6e397c416c4a93773ce4645
- ee98ef74c496447847f1876741596271
- e65322b4add2e5183616ce283e99614f
- 6127fd0843ad7f5cc4488a52ef49bc11
- 76f099ad94acf28d3eb1341804855824
SHA-256
- 01bf58c650b6ba30733c14026fcff4ecfc24becdd05637a84ef2a7e86aff3fe0
- 7f505a1064ea09daba577aa553efbf3385c890ab5aac2ace6ef3e927f480fb87
- 96e91a1f656fb70339f8f4e383e7f967d25c1a414f436ddffc692518ace579ad
- 914eb64b93cbb631c710ef6cbd0f9cedf93415be421ccc6e285b288b87f3a246
- c1b67a30119107365c4a311479794e07afb631980a649749501cb9f511fb0ab4
- a9ea7e952ce38bf8bc14114325ca2a1bfed16f63798028565a669808b8b728dc
- ed7b5c16cb5c4f56b3ded279688b693ec52389cacc0b81e940b0591b7f68aa84
URL
- http[:]//sales[.]inteleksys[.]com/file/vbs[.]vbs
Remediation
- Block the threat indicators at their respective controls.
- Do not download email attachments from untrusted sources.
- Do not click on URLs attached in untrusted emails.
- Do not use outdated browsers.
- Keep all systems and software patched against all known vulnerabilities.
- Verify a website’s legitimacy before entering credentials and banking information.








