

Rewterz Threat Advisory – Chrome 78 Released With DoH Trial, Tab Hover Cards, and More Patches
October 23, 2019
Rewterz Threat Alert – Lazarus APT Group Drops Malicious PowerShell Scripts – IoCs
October 23, 2019
Rewterz Threat Advisory – Chrome 78 Released With DoH Trial, Tab Hover Cards, and More Patches
October 23, 2019
Rewterz Threat Alert – Lazarus APT Group Drops Malicious PowerShell Scripts – IoCs
October 23, 2019Severity
Medium
Analysis Summary
Web cache poisoning attacks have been discovered that could be used to deny users access to resources delivered through a content delivery network (CDN). Named Cache-Poisoned Denial of Service (CPDoS), the new method has several variations and works by sending an HTTP request with a malformed header. CDNs have the property of reducing the traffic footprint on origin servers using their services by caching resources that are requested frequently by clients. CPDoS works at the level of the intermediate cache system of a CDN, which receives and stores an error page caused by a malformed HTTP request header and works as follows.
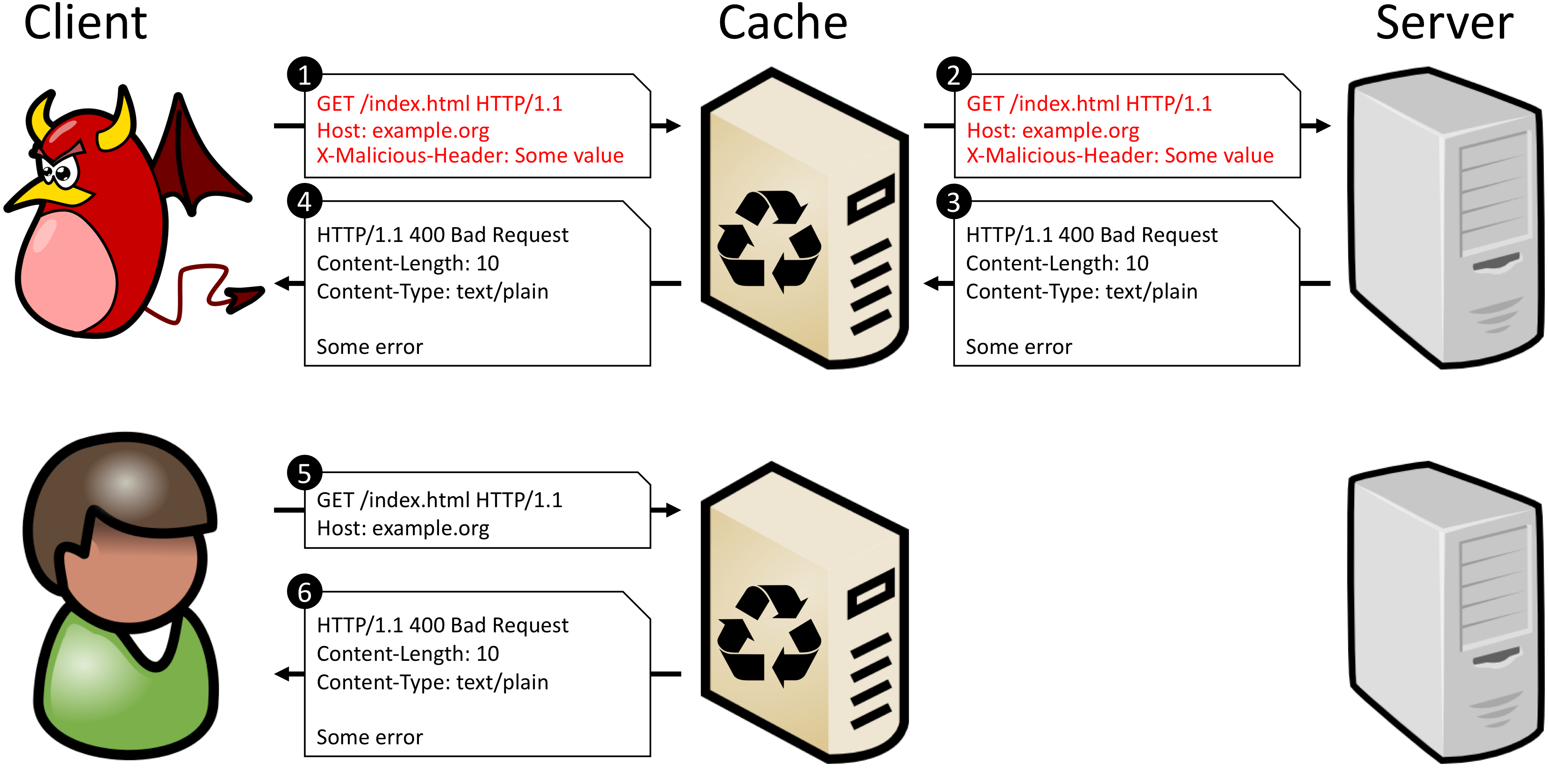
There are three variations of the CPDoS attack:
- HTTP Header Oversize (HHO)
With the HHO type of CPDoS attack, a threat actor takes advantage of the size limit intermediary systems and web servers set for an HTTP request header.
If the cache system accepts a request header size larger than what is defined for the origin server, the attacker can craft a request with an oversized request key or with multiple headers.
- HTTP Meta Character (HMC)
HTTP Meta Character (HMC), the second variation of the CPDoS attack is similar to HHO but leverages a harmful meta character. These are any “control characters such as the break/carriage return (‘\n)’, line feed (‘\r’) or bell (‘\a’).” Again, the cache system does its job and forwards the request as it is received from the client. As it reaches the origin server, it may be classified as malicious and generates an error message that gets cached and presented to the client instead of the requested resource.
- HTTP Method Override (HMO)
The method override attack (HMO), a third variation of the CPDoS, profits from intermediary systems (e.g. proxies, load balancers, caches, firewalls) supporting only the GET and POST HTTP request methods.
This translates into blocking other HTTP requests methods. A web framework that provides instructions for the web app to replace the supported HTTP method in the header allows bypassing the security policy and delivers a different one, such as DELETE.The consequence is that the error message is cached and served for subsequent valid GET requests for the /index.html resource.
The table below shows which combination of web caching systems and HTTP implementation is affected by this class of denial of service.
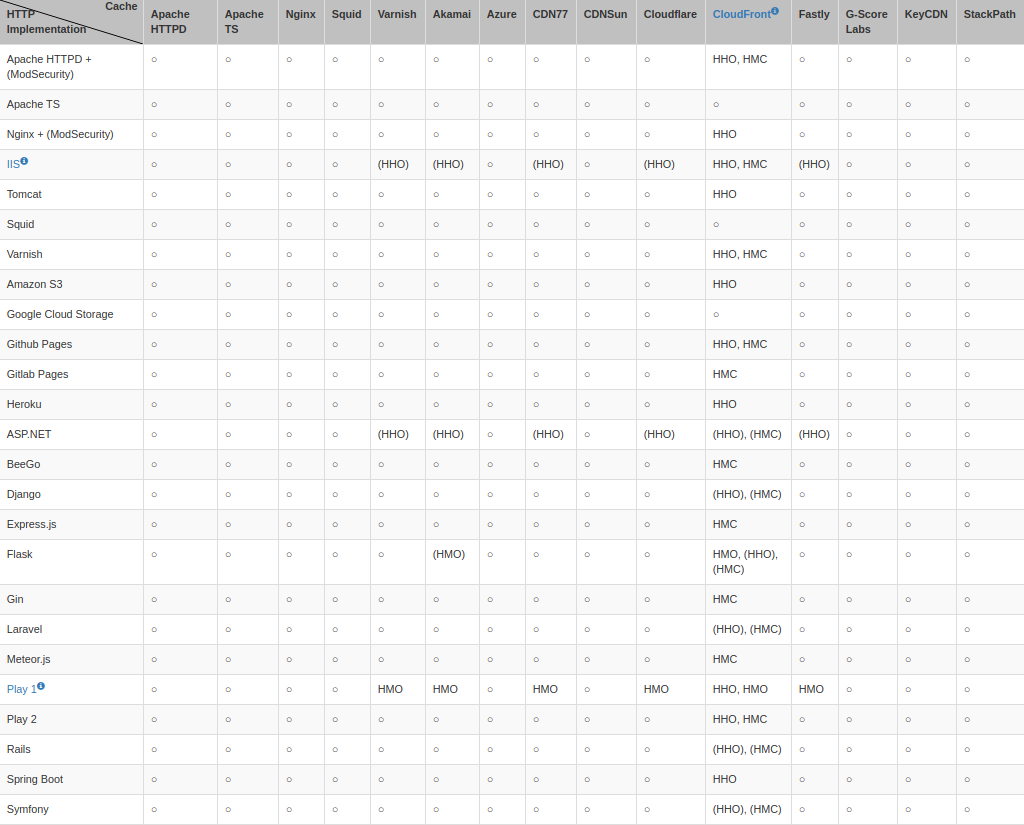
Amazon’s security team acknowledged the weaknesses in CloudFront and stopped caching error pages with the status code ‘400 Bad Request’ by default
Microsoft updated IIS Server with a fix and published details about the vulnerability (CVE-2019-0941) in June. Play Framework also patched their product against the HMO method in versions 1.5.3 and 1.4.6. Researchers have not heard back from most of the other vendors.
Impact
- Disabling of Web Resources and Websites
- Cache-Poisoned Denial of Service
- Availability Compromise
Remediation
- Follow the HTTP standard and cache only the error pages ‘404 Not Found’, ‘405 Method Not Allowed’, ‘410 Gone’ and ‘501 Not Implemented’.
- Do not use inappropriate status codes for errors. For instance, the ‘400 Bad Request’ is used for declaring an oversized header whereas the correct one is ‘431 Request Header Fields Too Large’ and it is not cached by any system analyzed by the researchers.
- Another mitigation against HHO and HHM CPDoS variations is to exclude error pages from being cached altogether.
- Protective measures also include setting up a Web Application Firewall (WAF) in front of the cache to catch malicious content trying to reach the origin server.








