

Rewterz Threat Advisory – CVE-2019-1620 – Cisco Data Center Network Manager Arbitrary File Upload and Remote Code Execution Vulnerability
June 27, 2019
Rewterz Threat Advisory – Oracle Solaris Multiple Third Party Components Multiple Vulnerabilities
June 27, 2019
Rewterz Threat Advisory – CVE-2019-1620 – Cisco Data Center Network Manager Arbitrary File Upload and Remote Code Execution Vulnerability
June 27, 2019
Rewterz Threat Advisory – Oracle Solaris Multiple Third Party Components Multiple Vulnerabilities
June 27, 2019Severity
Medium
Analysis Summary
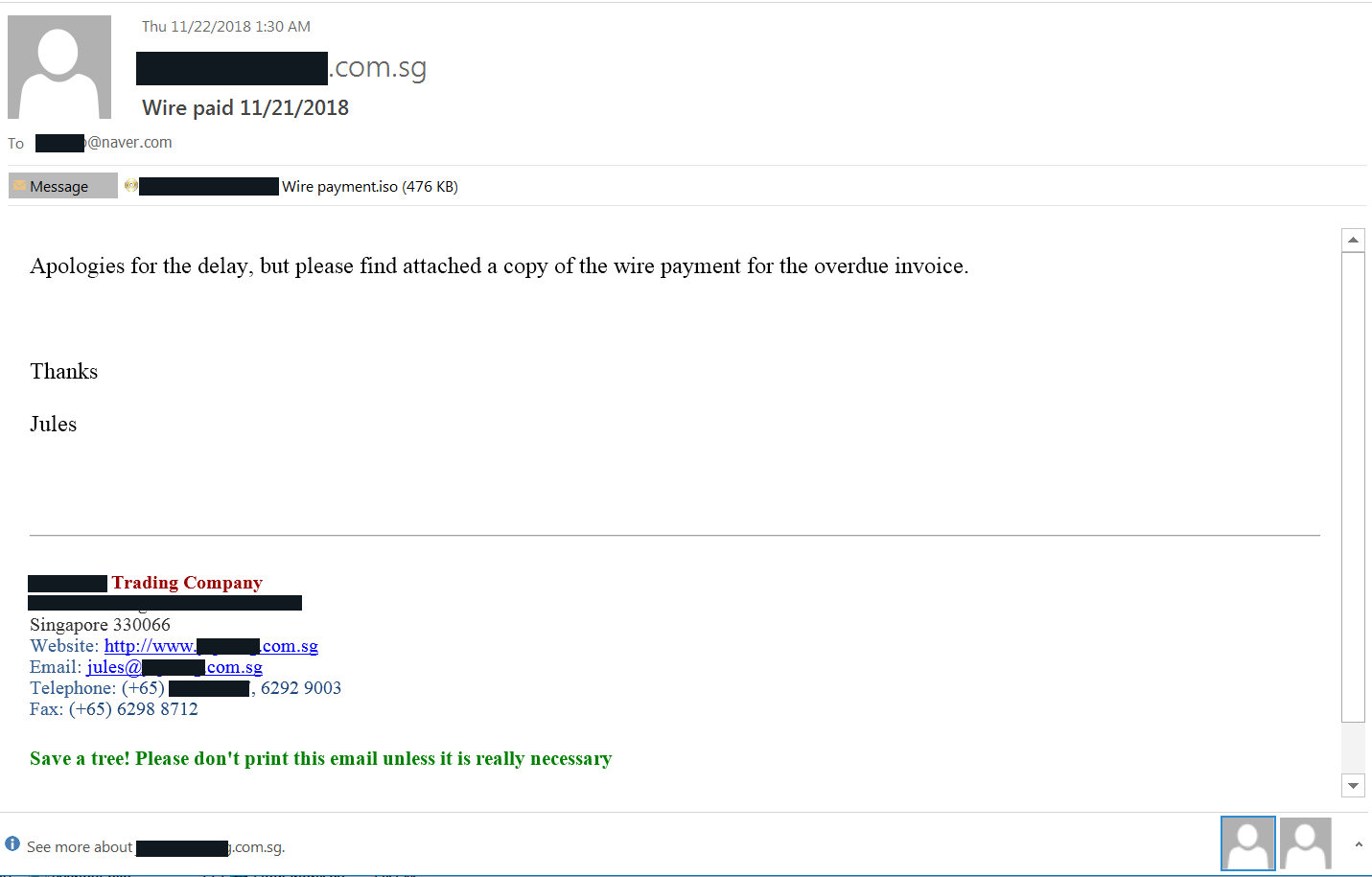
Multiple malicious campaigns were observed with concealed LokiBot and Nanocore malware inside ISO image files small enough to fit into an email attachment.
Both LokiBot and Nanocore incorporate data-stealing capabilities. They target web browsers, email clients, remote admin tools (SSH, VNC, and RDP), and clipboard data. They can also collect information about documents present on the system and monitor user keystrokes to extract more sensitive details.
10 variants of these type of campaigns, with variations in the ISO images and messages delivered to potential victims. The endeavors appear to follow the “spray and pray” principle as they did not target specific individuals or businesses.
The emails delivers LokiBot or Nanocore RATs by luring users to open the financial document in the attachment.
Impact
Exposure of sensitive information
Remediation
- Always by suspicious about emails sent by unknown senders.
- Never click on the link/ attachments sent by unknown senders.








