

Rewterz threat Advisory – SaltStack Vulnerability gets Ghost Blogging Platform Infected with Crypto-miner
May 4, 2020
Rewterz Threat Alert – CursedChrome Extension Turns Browser into a Hacker’s Proxy
May 4, 2020
Rewterz threat Advisory – SaltStack Vulnerability gets Ghost Blogging Platform Infected with Crypto-miner
May 4, 2020
Rewterz Threat Alert – CursedChrome Extension Turns Browser into a Hacker’s Proxy
May 4, 2020Severity
Medium
Analysis Summary
A new phishing campaign is distributing a double-punch of a LokiBot information-stealing malware along with a second payload in the form of the Jigsaw Ransomware.
By using this malware combo, the attackers first steal saved user names and passwords stored in a variety of applications and then deploy the Jigsaw Ransomware to try and get a ransom.The exact emails sent as part of this campaign have not been found, but the attachments impersonate invoices, bank transfers, orders, and business inquiries.This campaign is using Excel attachments with names such as Swift.xlsx, orders.xlsx, Invoice For Payment.xlsx, Inquiry.xlsx. Unlike many phishing attachments, the actors appear to be utilizing legitimate or carefully crafted spreadsheets that have been weaponized to seem believable, as shown below.
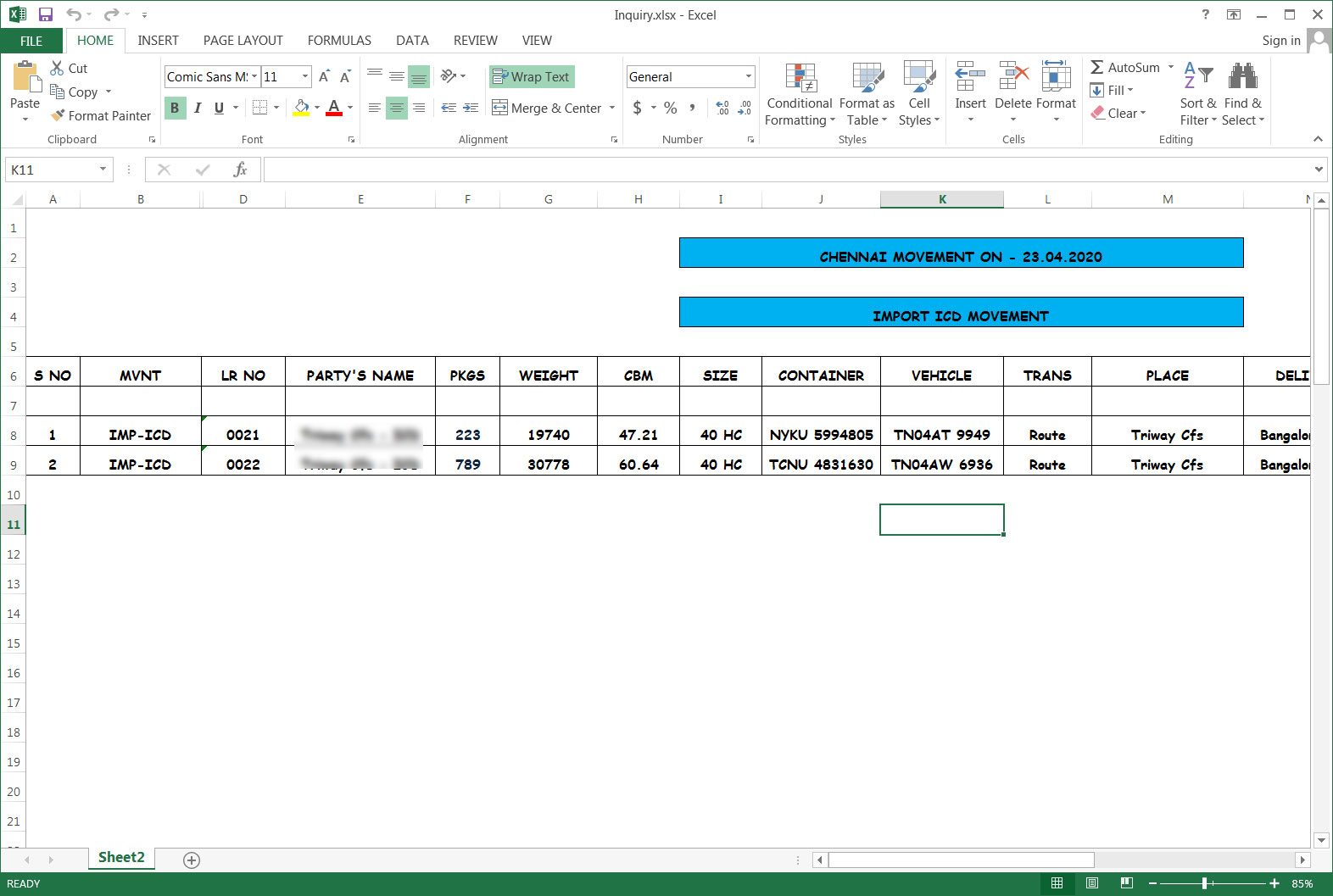
These attachments have been weaponized using LCG Kit so that they exploit an old Microsoft Office CVE-2017-11882 remote code execution vulnerability in Equation Editor. If successfully exploited, malware will be downloaded from a remote site and executed.
LokiBot has the ability to steal saved login credentials from a variety of browsers, FTP, mail, and terminal programs and then sends it back to the command and control server to be collected by the attacker. In addition, this LokiBot variant has been configured to download and install a Jigsaw Ransomware variant that uses a Salvadore Dali mask from the popular Money Heist show as its background. Earlier in 2016, the Jigsaw ransomware used Billy the puppet from the movie Saw as its background.
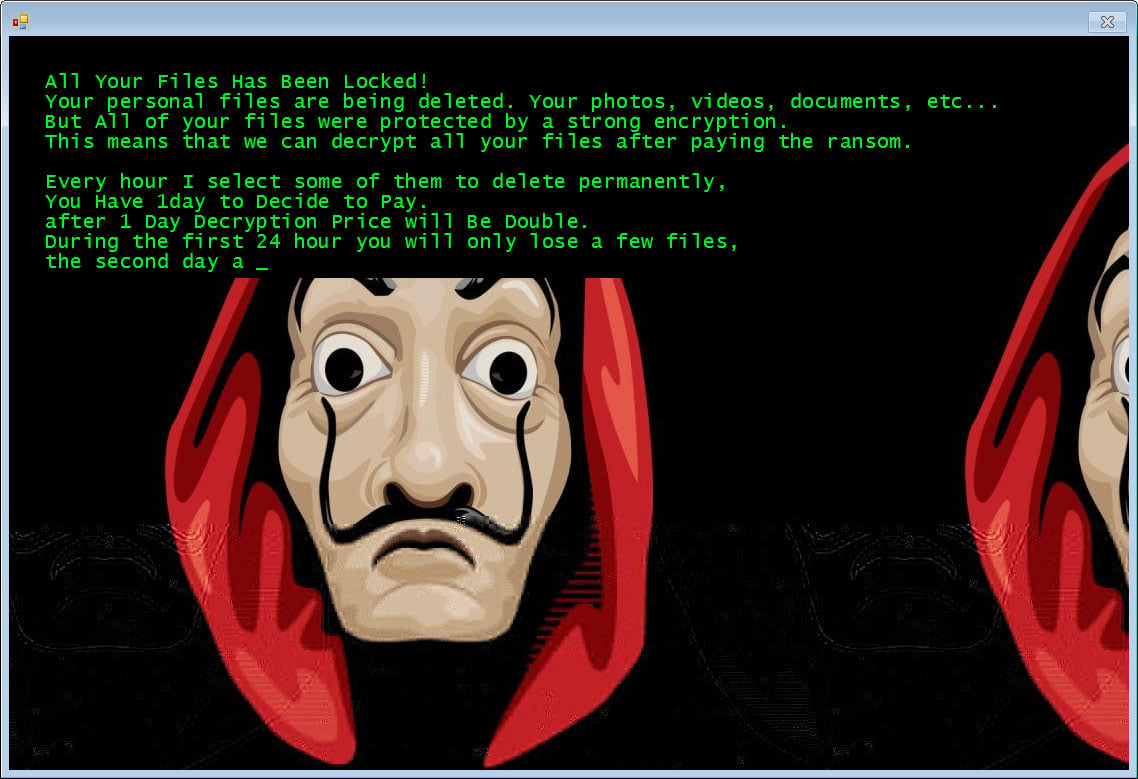
This Jigsaw Ransomware variant will encrypt a victim’s files and append the .zemblax extension to encrypted file’s names.The bad news is that the Jigsaw Ransomware will periodically delete your files until you pay. File deletion has also been witnessed in past campaigns of 2016.
Impact
- Credential Theft
- Information Theft
- Files Encryption
- Data deletion
Indicators of Compromise
Filename
- Swift[.]xlsx
- orders[.]xlsx
- Invoice For Payment[.]xlsx
- Inquiry[.]xlsx
Remediation
- Scan for IoCs and if found, block the sender’s email address.
- Keep functional backups of all important data.
- Make sure to use the latest security updates for your installed Office applications.
- If you become infected, be sure to terminate the drpbx.exe process using Task Manager so that the Jigsaw Ransomware will be shut down and can not delete your files.
- If infected, consult a security expert to recover your files, as files encrypted by Jigsaw can be recovered.








