

Rewterz Threat Alert – PYSA Ransomware
April 8, 2020
Rewterz Threat Alert – Grandstream and DrayTek Devices Exploited to Power New Hoaxcalls DDoS Botnet
April 9, 2020
Rewterz Threat Alert – PYSA Ransomware
April 8, 2020
Rewterz Threat Alert – Grandstream and DrayTek Devices Exploited to Power New Hoaxcalls DDoS Botnet
April 9, 2020Severity
High
Analysis Summary
Cybersecurity researchers have discovered a new emerging IoT botnet threat that leverages compromised smart devices to launch ‘distributed denial-of-service’ attacks, potentially triggered on-demand through platforms offering DDoS-for-hire services. The botnet works by employing credential stuffing attacks against a variety of devices, such as routers (from Dasan Zhone, Dlink, and ASUS), video recorders, and thermal cameras, to co-opt them into the botnet. Researchers named the botnet “dark_nexus” based on a string it prints in its banner. In one of its earliest versions, it used this name in its user agent string when carrying out exploits over HTTP: “dark_NeXus_Qbot/4.0”, citing Qbot as its influence. Dark Nexus comes with some robust features like payloads are compiled for 12 different CPU architectures and dynamically delivered based on the victim’s configuration. It also uses a technique meant to ensure “supremacy” on the compromised device. Uniquely, dark_nexus uses a scoring system based on weights and thresholds to assess which processes might pose a risk. This involves maintaining a list of whitelisted process and their PIDs, and killing every other process that crosses a threshold of suspicion.
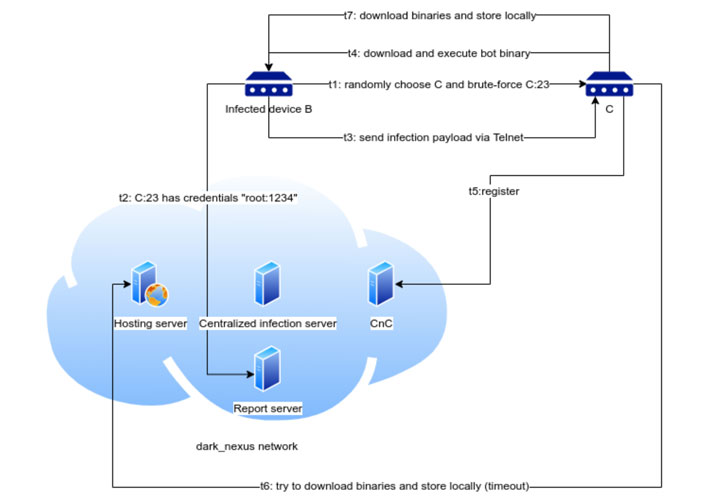
Features of the new botnet used for DDoS services:
• Uses a DDoS tactic that disguises traffic as
innocuous browser-generated traffic
• Synchronous and asynchronous Telnet scanners
used for infection and victim reporting
• Uses socks5 proxies, potentially for renting access
to the botnet
• Uses Telnet credential stuffing and exploits to
compromise a long list of router models
• Most compromised IoTs are based in Korea
• Uses debugging module to maintain proper
functionality and reliability of the device
• Code compiled for 12 different CPU architectures
and has dynamic downloader injection
• Distributed binary hosting using each victim as a
reverse proxy
• New persistence tactic by removing device restart
permissions
• Frequently updated components, with over 30
versions in 3 months
• Possibly created by greek.Helios, known botnet
author who sells DDoS services and botnet code
So far, dark_nexus comprises at least 1,372 bots, acting as a reverse proxy, spanning across various locations in China, South Korea, Thailand, Brazil, and Russia.
Impact
- Process Termination
- DDoS
Indicators of Compromise
SHA1
- 0028b4f8c11608fef555672e1a61cb9bdad1389d
- 022a65716f7e84a4cf036f943fa95ce15763a155
- 02d787f9a49648bc7a499815992672a195c7bc94
- 03c2ce10e35b0ae95c80a2e462be1fe31b2ea9c5
- 03dc6a47ecbeea3027eb4278b26af8825bef2d6b
- 03e780f9316c9cc853189df83c30650f32d0e476
- 058fe58e3dc6c77c19258e3a11bcd786d849363d
- 0671f6152569a646d820073b73cb1aef642a5f6c
- 069df92b74c9db557d42430d77fa0dd557a91f81
- 07d0dc0eccb7f77cccd9209c6240821d81ca386a
- 0a1817c7606d7eea7971266c4ed111036c855c4e
- 0a28e032e2626f9f730662a677033020b3de664d
- 0a88bf52a7ae160a46d6b6ded745737f3b703f6f
- 0a8bc057d9ed8c79eb9ae5fd8ca63fc1f75b2765
- 0ae6aba288ec79baafdb69ad08c19367a62100c5
- 0af068739a456de81b4fe4610c43c99dec220e45
- 0e686f05804d2d6d95c2cd9052d0789b602a0c46
- 0fa5bdea8b859cb685dffe35be1994c690dea3ba
- 0fb2775fd7eb74a82eca8d73dbdc57f7bc2fbf87
- 12efc8b92a99a3c7332226ef56b303f11680b0ce
- 133ed889e86b3b1b1589cc52f62f54e8b9399730
- 1480105172855e399a359d4a1eda5cc6cdc579bf
- 15c61aa0a32ffd80ff5da6606c947cec27c48e75
- 160f8c82426476dfa37cdfa9fcb703fa5d631d9d
- 1610bb2b66027ee4c3987886fa64e0bdb752499b
- 199f6e548ad366db2c92deb6f927be544e171aa3
- 1b7357b02198d12300182d6a1737af3637066ce6
- 1d2bf6f1f4a20f67cf9e6b316adbdbab16327f21
- 1e7a0a9b0bba806ac52a820aa7db451660bd8142
- 1ee5d79830e48bbd4ef96b3735f7dacd9b3d8100
- 1f20645abb7d943e8e32f8ffcaf944038ca90f77
- 20067b27808b2f2188f138cd02ee6c22071e334a
- 200c6be564bba578c72ff288449ddd9f4a21e2e5
SHA-256
- 342a361691a7cb68529330b4d66f44e78cab3adfd0774df1a46b6db6671e2c2d
- bc0457d7935e29aecb338756bde213cd18aa1b617b00d30c4deedd5eef9ba877
- 0c69b8d4b4fb85a6ac56a240424670016257bed3e4791185b21cd6abeda8c986
- 23cde5604f86d86239c571c104f2c3773526d9a6983baecf96f2fcd8b7941e5a
- de760e297b11773bb85deff4330a445a2ab9fe6538543e3d41a936707a4e9af4
- 2114560a1f3528c556a19f616b9c34b1fc8e07f5436c14433415f17f7b158755
- 565182c9ae294382287aecf71e394bce0d7291d62f15e0b648723879c98a7a59
- baa26609da4987c104c35d7536b05c70fda3028575014427014aed638d4c2e40
- 13750d86aebfa4df8176fb56b68ad515db024842ab2dd9a2cfa7f540f0849cc1
- c851fd9b9b5b1d70c3758bef59d6528f5230fedc0b972f20cd5bf72a129e5745
- 4bb51123933daf3e66537d74c88515952727a85f2da40b5a387dedc29afd1e11
- 9c13dea8cd761326a5c33a522e4cd03d86e63410b3dc0f6a64e76ff3d1ae097c
- a18014b4abe251051f44a224c58dc3550a6dc13c39e2bfe74cf303d838c4dbcf
- 36e7873870bcb5211f651b7f43c5f610d2fe4a884b743962f7e5e1a3a7b8772e
- 3fb6b9e1fdcaa8a3b9abb9660bbbf8bdb16661b013c898d868d1cbeb2aecca63
- c11c4f21123e3419108a04b25a1455e81af543de71fe627d98ea72581c6fdd35
- 1c081f5f726f2694e7ef4da0591cda8cbf314b7a21c2e5e67b616ff9449728e8
- 13079382ff84ee8a46c1e6d5c2e0f53b57635dbcffc69d4fa790f83991fef574
- f0595aaee8c7f8562bcfecfb6a1d7fc972e0e9802c40bc7c0375e567751dd4df
- 672716cb3b858e69e1fd403ce1d17f8934388d29d721d92ab111567518429c77
- 661ca273e17479dbfbb75c44eb211cda9c4d2ebe91cd42a3d9496b9f966baf1e
- 464e3c77eb95ee8f59a2d165c0081572d8f04a64bb4db9b195bbe0864fdc912f
- 36bb895a4fe512828cfbe3b63006d4392e48265e1c7b1b811cb55af6308f378c
- 4660c261e8f68dbd574c910df1e48941252176c434b8714375eb6201548ecb3e
- 6baaebc351f7d1104afb2f168d14896c1a377c89bf1ea650f46325e6dc6df575
- 2413caa2520cd85ce1055c37dab6cd87257618744127a67b57134b2e846e915c
- 692b8fc8657a009e523214c7dcc566168b6fd057d0c0f9e040623261a77e8dc2
- 68cf5d8641218d1042e2bdc28fbf3f7a525b1bd790db9f30f16b61c6fd879030
- 69faa19b3378946b827f3ed7cb85347b6be9ef2ba0103b4c156ed9977ed6d9cb
- ac3bd662791cfb3e3450c79a967f9988701b0e39e90021fdd4c160cf20f1971d
- 97c0d804532763b957ba0b126f1479e48feb4c915701a693025137aa2e610103
- b8911afb77d67b6b07eaedd087383e64a75c212bc7828fed73cded1027e6c0cb
- e3f015f701b4a95d7e121b8e809ee77638d469d759b49d963edc6f53170f03d3
Remediation
- Block the threat indicators at their respective controls.
- Keep all software updated to latest versions.








