

Rewterz Threat Alert – Agent Tesla Malware – Active IOCs
August 28, 2023
Rewterz Threat Alert – ModiLoader aka DBatLoader – Active IOCs
August 28, 2023
Rewterz Threat Alert – Agent Tesla Malware – Active IOCs
August 28, 2023
Rewterz Threat Alert – ModiLoader aka DBatLoader – Active IOCs
August 28, 2023Severity
High
Analysis Summary
In June 2022, Lockbit v3, also known as Lockbit Black, emerged as a ransomware variant. However, by September 2022, the builder for this version was leaked online, enabling anyone to generate customized iterations of the ransomware. Two Twitter users, namely @protonleaks and @ali_qushji, shared the necessary files to create different versions of Lockbit Black. Researchers analyzed the leaked files and observed subtle differences in the builder.exe binary, with one version dated September 9, 2022, and the other compiled on September 13, 2022.
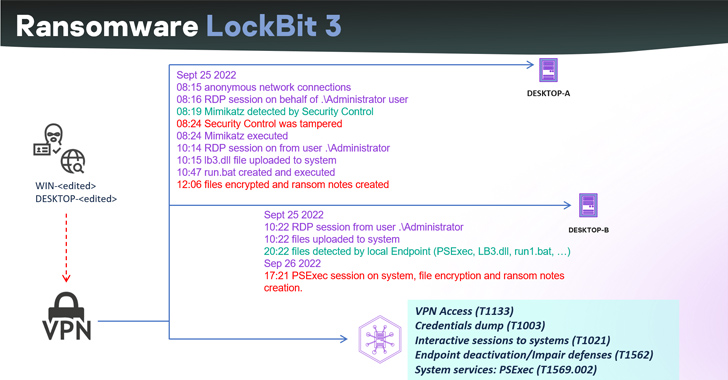
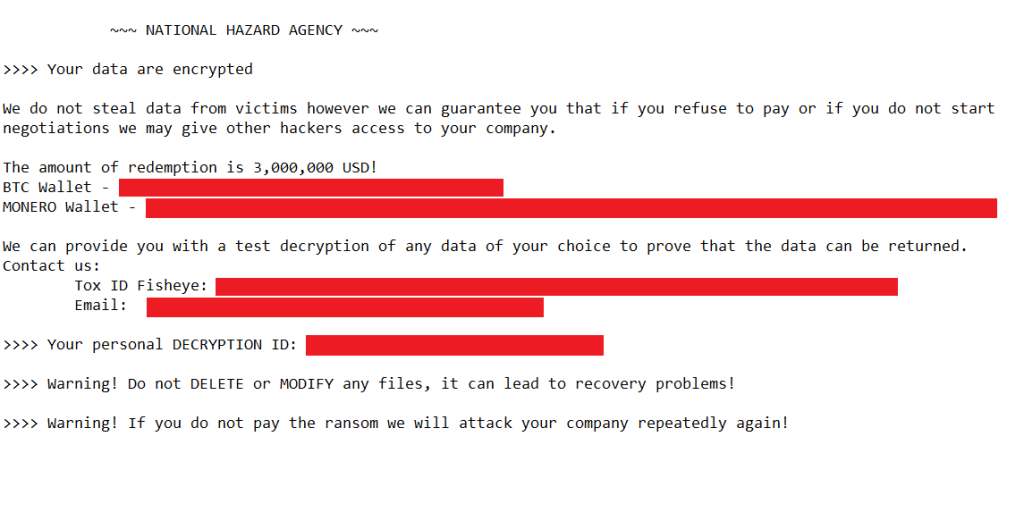
Soon after the builder leaked, researchers encountered an instance of the Lockbit 3 ransomware during an incident response. This variant of Lockbit 3 featured a distinct ransom note with a headline linked to an unfamiliar group called “NATIONAL HAZARD AGENCY.” The ransom note specified the ransom amount for obtaining decryption keys and provided instructions for communication through a Tox service and email. This contrasted with the original Lockbit group’s approach, which relies on its negotiation platform.
Several other threat actors, including Bl00dy and Buhti, also adopted this variant in their attacks. The analysis involved examining 396 distinct samples, primarily created by the leaked builders (312 samples). Additionally, the researchers identified samples generated by other unidentified builders in June and July 2022.
Many of the identified parameters aligned with the default configuration of the builder, although minor alterations were present in some samples. This suggests that these variations might have been hastily developed for urgent requirements or potentially by less motivated threat actors.
The majority of the samples encrypted local disks and network shares while avoiding hidden folders and omitting the system shutdown option. Interestingly, network deployment via PSEXEC was configured in 90% of the samples, and deployment by GPO was set up in 72% of cases. A limited number of samples enabled communication to command-and-control (C2) servers.
Researcher’s findings also revealed a significant point related to the use of leaked builders by actors other than the original Lockbit group. Approximately 77 samples lacked any reference to the “Lockbit” string in their ransom notes. This unexpected finding, along with modified ransom notes that omitted the Lockbit reference or included different contact information (email/URL), indicated the likelihood of the builder being misused by entities other than the authentic Lockbit group.
Impact
- File Encryption
- Sensitive Information Theft
Remediation
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Maintain Offline Backups – In a ransomware attack, the adversary will often delete or encrypt backups if they have access to them. That’s why it’s important to keep offline (preferably off-site), encrypted backups of data and test them regularly.
- Never trust or open links and attachments received from unknown sources/senders.
- Enable antivirus and anti-malware software and update signature definitions in a timely manner. Using multi-layered protection is necessary to secure vulnerable assets
- Keep operating systems, applications, and security software up to date with the latest patches.
- Apply security updates promptly to mitigate vulnerabilities that ransomware might exploit.
- Train employees on recognizing phishing emails and social engineering tactics.
- Encourage a culture of security awareness to prevent users from inadvertently downloading or executing malicious files.
- Deploy endpoint security solutions that include anti-malware, anti-ransomware, and behavior-based detection.
- Implement network segmentation to isolate critical systems and data from potential ransomware spread.
- Restrict lateral movement of threats within the network.
- Enforce the principle of least privilege to limit users’ access to only the resources they need.
- Regularly review and update access controls to prevent unauthorized access to critical data.
- Maintain regular backups of critical data and systems offline or in a secure location.
- Test backup restoration procedures to ensure data can be recovered in case of an attack.
- Deploy email filtering solutions to block phishing emails and malicious attachments.
- Use intrusion detection and prevention systems to monitor network traffic for signs of suspicious activities.
- Develop a comprehensive incident response plan that outlines steps to take in case of a ransomware attack.








