

Rewterz Threat Alert – Russian APT Gamaredon Using Template Injection
November 26, 2020
Rewterz Threat Alert – Egregor Ransomware Using Rclone and Cobalt Strike
November 27, 2020
Rewterz Threat Alert – Russian APT Gamaredon Using Template Injection
November 26, 2020
Rewterz Threat Alert – Egregor Ransomware Using Rclone and Cobalt Strike
November 27, 2020Severity
High
Analysis Summary
On the 100th release of Trickbot, the malware came equipped with new evasion techniques, one capability is to use of an obfuscated batch script launcher to jumpstart malicious executables. TrickBot is a malware infection commonly installed via malicious phishing emails or other malware. When installed, TrickBot will quietly run on a victim’s computer while it downloads other modules to perform different tasks. TrickBot is known to finish an attack by giving access to threat actors who deploy either the Ryuk or Conti ransomware on the compromised network.
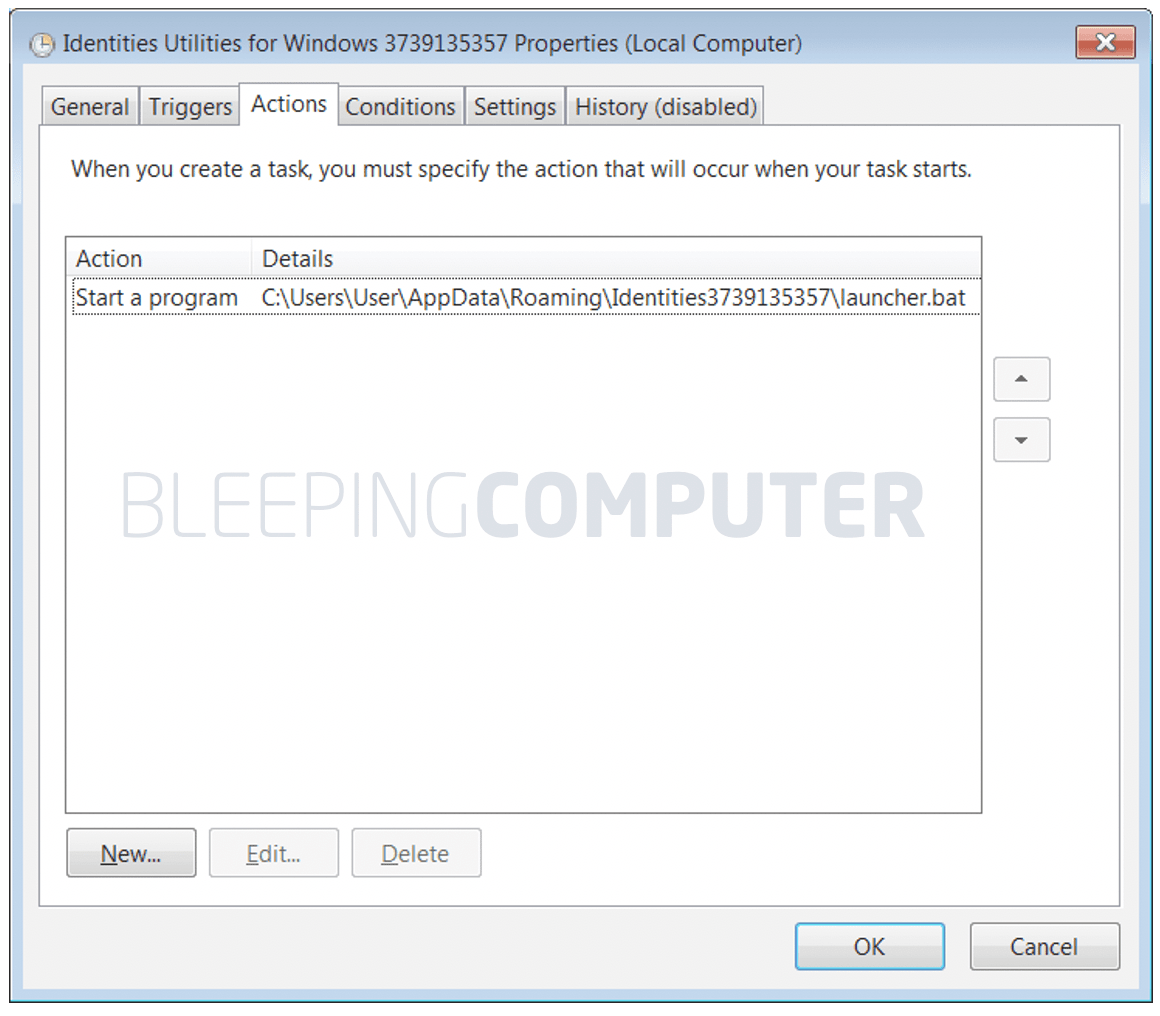
Impact
- Code execution
- File encryption
Indicators of Compromise
MD5
- 82e2de0b3b9910fd7f8f88c5c39ef352
- a5a28b55cd644c7b83b4641c4fdbf3a5
- ced54af623254201ee2112514270000a
- 006937f0817a2aa8642097d749208b29
SHA-256
- ca8ba5d63e096a04a9a2ce76dadf9d33b318235e70d6c0066f1fe36fe1f5bc8a
- 58c4bea082b2f44f0beab5356ae2bc9bc73c3f13ab0491861bc2ba24690da103
- 8215816827a07129430ed907b2168748f1f933dbf22865d6fa4da430f2e6728e
- 6300bfed92e420fd678bdfa83cde8e57b5d3ae99f84915a0e18ef5d25b6d2cba
SHA1
- 84205724dbca914858dfe5b95d2198e1f87040b3
- 772851debc5ef85a750577ebbae3cf3592c0b3ce
- 594f6011422af739b98f503da8d4bc13cc99e85e
- 1a4d62a326e955f558e81c184080c670e92acf56
Remediation
- Block all threat indicators at your respective controls.
- Search for IOCs in your enbironment.








