

Rewterz Threat Alert – Agent Tesla Malware – Active IOCs
June 23, 2023
Rewterz Threat Alert – STOP (DJVU) Ransomware – Active IOCs
June 26, 2023
Rewterz Threat Alert – Agent Tesla Malware – Active IOCs
June 23, 2023
Rewterz Threat Alert – STOP (DJVU) Ransomware – Active IOCs
June 26, 2023Severity
High
Analysis Summary
Researchers recently analyzed a malware sample used in an attack on the Pakistan government, suspected to be the work of the SideWinder advanced persistence threat (APT) group. SideWinder, also known as APT-C-17 and T-APT-04, operates from a South Asian nation-state and focuses on cyber espionage against Asian countries, particularly China and Pakistan. The group has been active since at least 2012 and primarily targets Pakistani government and military organizations.
In this specific attack campaign, the threat actors employed targeted spear-phishing emails to target government organizations. The emails contained a PDF attachment named “Adv-16-2023,” posing as a security advisory issued by the Pakistani Cabinet Division. Upon opening the file, the victim was prompted to download a password-protected RAR file. This compressed file contained a malicious LNK file disguised as a PDF file. Upon opening the LNK file, the attacker used mshta.exe to download and execute the something.hta file.
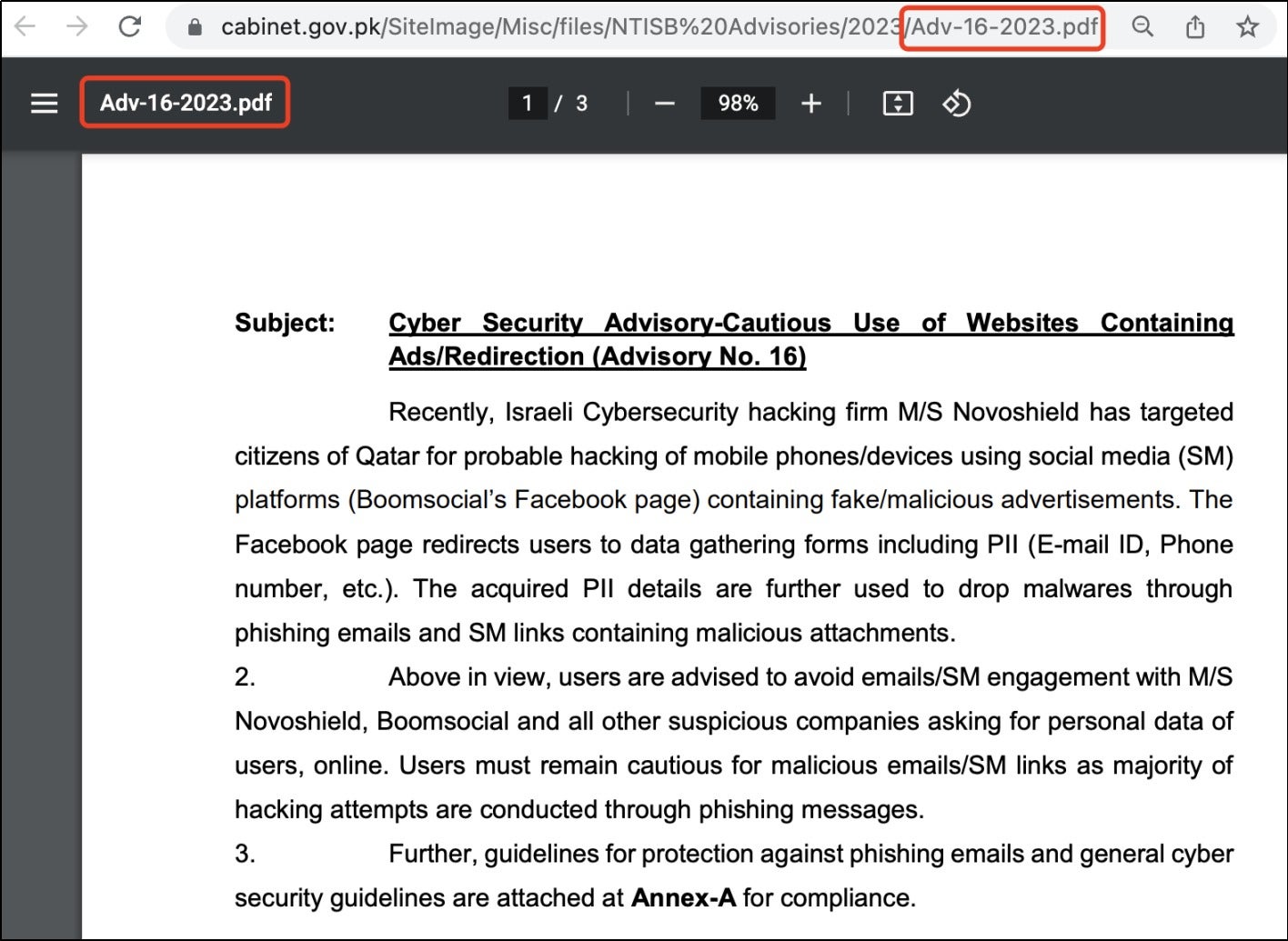
The downloaded HTA file utilized VBScript to download additional components used in the attack. One component was version.dll, which was placed in the local OneDrive directory. The attacker exploited DLL side-loading to hijack the local OneDrive program and its update program, allowing them to deploy Cobalt Strike, a remote control program often used in penetration testing, to take control of the compromised machine.
The version.dll file was stored in the path %LOCALAPPDATA%\Microsoft\OneDrive\ and required both the 64-bit versions of OneDrive.exe and OneDriveStandaloneUpdater.exe to load. Certain functions within these files were invoked to decrypt and execute subsequent payloads. The shellcode executed reflective loading to dynamically load and execute the Cobalt Strike beacon, establishing a connection with the attacker’s command-and-control server.
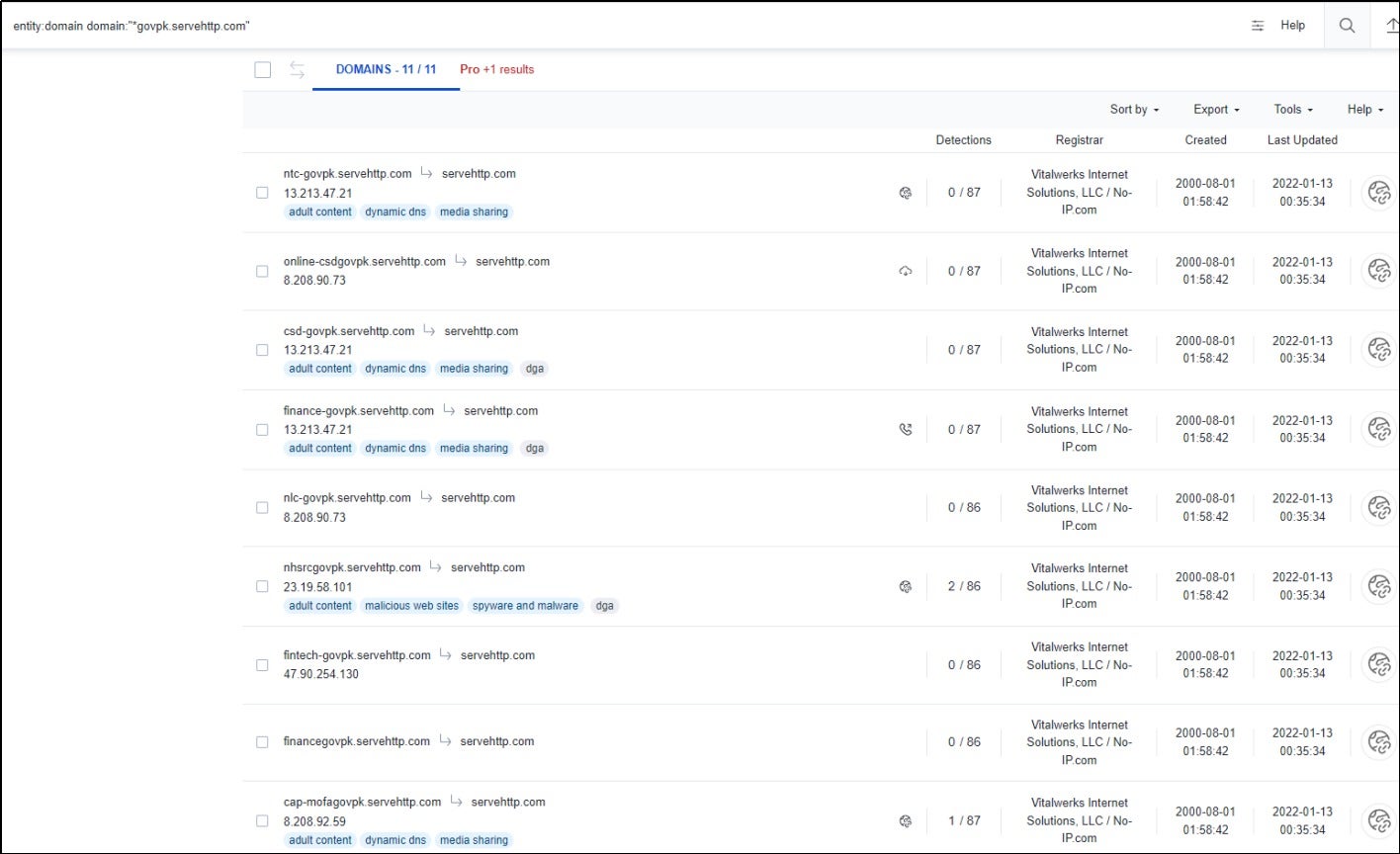
According to researchers, the attack also involved domain names such as finance-govpk.servehttp[.]com and csd-govpk.servehttp[.]com, which were associated with phishing documents used in the attack. These domain names were consistent with the naming format attributed to SideWinder, and the C2 server implemented access controls that allowed file downloads only from IP addresses in targeted regions, such as Pakistan.
The SideWinder APT group frequently relies on spear-phishing attacks against specific targets, primarily government and military organizations, to steal sensitive information. Organizations in these sectors should enhance their network infrastructure protection and remain vigilant. The attack demonstrated the use of Cobalt Strike, highlights the need for security vendors to strengthen their detection capabilities to detect such techniques.
Given the Sidewinder APT group’s persistent targeting of government and military organizations and their utilization of sophisticated attack techniques, it is important for these sectors to enhance their network infrastructure protection and remain vigilant against such threats. Security vendors also need to strengthen their detection capabilities to detect and mitigate attacks employing similar tactics and techniques.
Impact
- Information Theft and Espionage
Indicators of Compromise
Domain Name
- csd-govpk.servehttp.com
- financeptcl-govpk.servehttp.com
- sdmx-financegovpk.servehttp.com
- cap-mofagovpk.servehttp.com
- financegovpk.servehttp.com
- fintech-govpk.servehttp.com
- nhsrcgovpk.servehttp.com
- nlc-govpk.servehttp.com
- online-csdgovpk.servehttp.com
- finance-govpk.servehttp.com
IP
35.175.135.236
MD5
- d2bebe3912a5700d76635af29f098cfb
SHA-256
- 135efe01516830bed632b746171c14650f4b0ceb943ea4a6ce91c0fdcb9876c4
SHA-1
- c7d6792ba6ff084096645f6ccbd095bec3c1ccfa
URL
- https://ntc-govpk.servehttp.com/something.htahttps://ntc-govpk.servehttp.com/Advisory-16-2023.rar
Remediation
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls
- Emails from unknown senders should always be treated with caution.
- Never trust or open links and attachments received from unknown sources/senders.
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Patch and upgrade any platforms and software timely and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Enable antivirus and anti-malware software and update signature definitions in a timely manner. Using multi-layered protection is necessary to secure vulnerable assets
- Enforce strong password policies across the organization. Encourage the use of complex passwords and enable multi-factor authentication (MFA) wherever possible to add an extra layer of security.
- Deploy reliable endpoint protection solutions that include antivirus, anti-malware, and host-based intrusion prevention systems (HIPS) to detect and block malicious activities.
- Utilize web filtering and content inspection tools to block access to malicious websites and prevent users from downloading malicious files.
- Deploy IDPS solutions to detect and block suspicious network traffic and intrusions.
- Conduct regular vulnerability assessments and penetration testing to identify weaknesses in the network infrastructure and address them before they are exploited by attackers.
- Continuously monitor network traffic and security logs for any signs of suspicious activities. Stay updated on the latest threat intelligence to understand the tactics, techniques, and procedures (TTPs) employed by the Sidewinder APT group and other threat actors.








