

Rewterz Threat Alert – AsyncRAT – Active IOCs
February 7, 2023
Rewterz Threat Advisory – CVE-2023-23477 – IBM WebSphere Application Server Vulnerability
February 7, 2023
Rewterz Threat Alert – AsyncRAT – Active IOCs
February 7, 2023
Rewterz Threat Advisory – CVE-2023-23477 – IBM WebSphere Application Server Vulnerability
February 7, 2023Severity
High
Analysis Summary
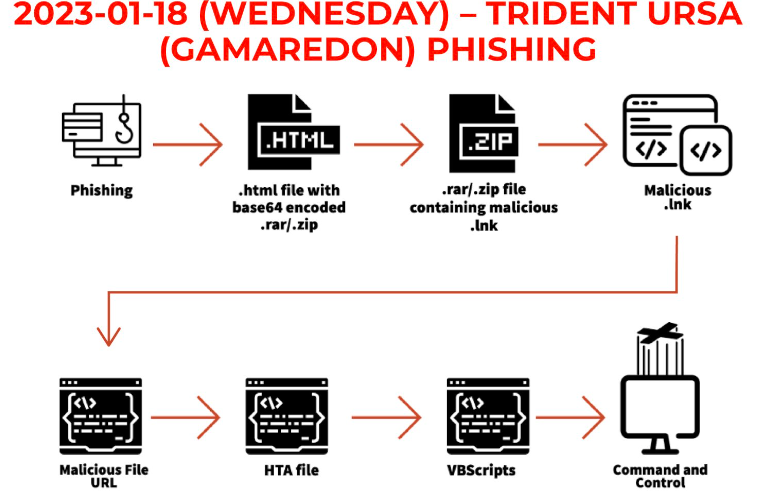
Shuckworm APT – aka Actinium, Armageddon, Primitive Bear, Gamaredon, and Trident Ursa – is a Russia-backed advanced persistent threat (APT) that has been operating since at least 2013. This cyber-espionage group is known to target government, military, and other high-value targets, primarily in Ukraine and has been linked to several advanced persistent threats (APT) campaigns. The main goal of this APT is to use the malicious document to gain control of the target machine. The exploit document uses the template injection technique to infect the victim’s computer with further malware. When the document is opened, it connects to the hacker’s server and downloads the payload file. Gamaredon’s tools are simple and designed to collect sensitive information from hacked systems and propagate it further. Its information-gathering efforts are nearly comparable to those of a second-tier APT, whose primary purpose is to collect and disseminate information with their units. The Gamaredon APT group’s recent attack leverages a decree document from the Russian Federation government as bait. In July, this APT group targets Ukrainian entities with PowerShell info-stealer malware dubbed GammaLoad.
It is important for organizations to take steps to protect themselves and to have a robust incident response plan in place. This includes implementing strong security controls, regularly monitoring networks for signs of compromise, and being aware of the group’s tactics, techniques, and procedures (TTPs) so that they can quickly detect and respond to attacks.
Impact
- Template Injection
- Sensitive Data Exposure
Indicators of Compromise
MD5
- c43c5e25b77deec6893a9454c39f0fbf
- 9099e0733e9817fec0fd8792ccd9b86c
SHA-256
- eecf508b0bd64123dd876ba5c5f99518c882e3b7ee436d3226adb3ba17bc479b
- 1f034ea47fcd8ffa60de37ab3dfb4c7ca981d5830b6927320b4fa966066e4dca
SHA-1
- d9f43aad536b11203f57e114e3a0bbb097d72d09
- 7a5eee6718d6b51c280e0588b1bdafecfec8d63c
Remediation
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Maintain Offline Backups
- Emails from unknown senders should always be treated with caution.
- Never trust or open ” links and attachments received from unknown sources/sender








