

Rewterz Threat Advisory – CVE-2024-26246 – Microsoft Edge Vulnerability
March 22, 2024
Rewterz Threat Alert – An Emerging Ducktail Infostealer – Active IOCs
March 22, 2024
Rewterz Threat Advisory – CVE-2024-26246 – Microsoft Edge Vulnerability
March 22, 2024
Rewterz Threat Alert – An Emerging Ducktail Infostealer – Active IOCs
March 22, 2024Severity
High
Analysis Summary
Turla, a Russian espionage threat actor, infected and compromised many systems of an unknown non-governmental organization (NGO) in Europe by deploying a backdoor known as TinyTurla-NG. The TTPs (Tactics, Techniques, and Procedures) employed by the threat actor are to steal sensitive data and to spread across the organizational network to operate stealthily and gather information.
The threat actor hacked the system, added an anti-virus exclusion, and established persistence by creating a malicious service as part of their initial post-compromise measure. It then used Chisel to exfiltrate data and relocate to other systems on the network by setting up additional communication channels.
TinyTurla-NG was first discovered by cybersecurity firms when it attacked a Polish NGO that supported Ukraine during the Russian invasion. The attack highly targeted small organizations located in Poland.
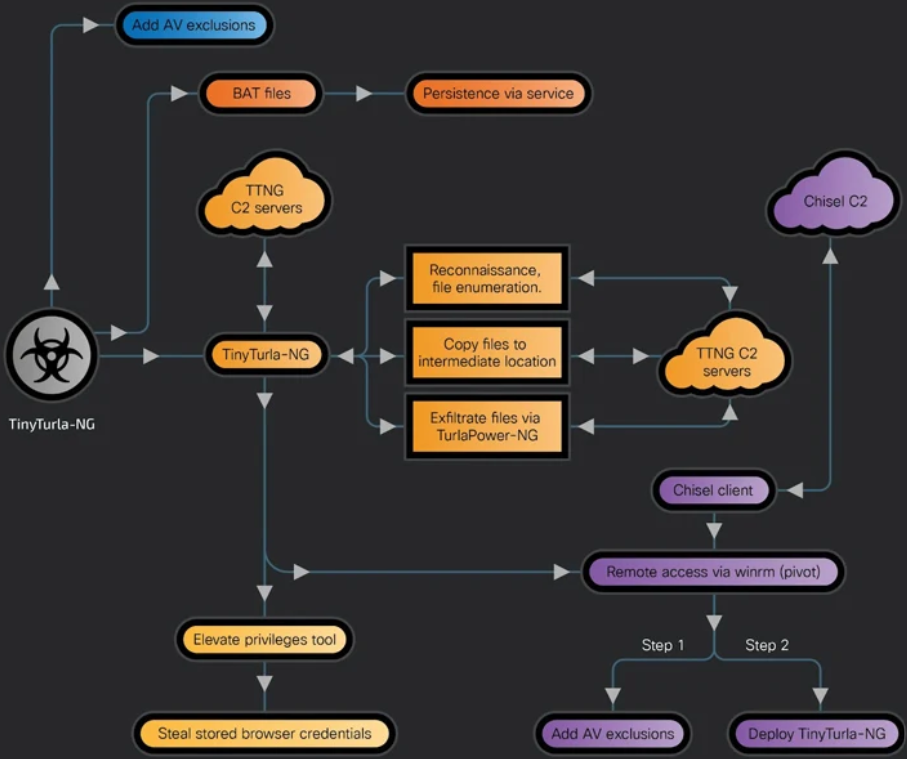
Turla gained initial access to the system by exploiting Microsoft Defender antivirus exclusion to elude detection while dropping TinyTurla-NG, which then creates a malicious ‘sdm’ service posing as a ‘System Device Manager’ service to continue the attack.
“Once the attackers have gained access to a new box, they will repeat their activities to create Microsoft Defender exclusions, drop the malware components, and create persistence,” the researchers said.
TinyTurla-NG serves as a backdoor, to carry out reconnaissance, exfiltrate data of interest to the command-and-control (C2) server, and position a custom-built version of the Chisel tunneling software. It is still unknown what intrusion pathway the threat actors used.
Impact
- Cyber Espionage
- Sensitive Data theft
- Unauthorized Access
Indicators of Compromise
MD5
- e4c356cf822cda0ca8e8161cb5bf6c39
- 0f2e9f501ca9780eff309b7022c9b01a
SHA-256
- 267071df79927abd1e57f57106924dd8a68e1c4ed74e7b69403cdcdf6e6a453b
- d6ac21a409f35a80ba9ccfe58ae1ae32883e44ecc724e4ae8289e7465ab2cf40
SHA-1
- ee350f5295fc127285791b76f2a2be98d7681a91
- e7fc80825c5b1f5d29836dde45e9314357d102a0
Domain Name
- hanagram.jpthefinetreats.com
- caduff-sa.chjeepcarlease.com
Remediation
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Conduct regular security awareness training to educate employees about phishing threats and safe email practices.
- Enable multi-factor authentication (MFA) to strengthen account security and prevent unauthorized access.
- Implement robust email filtering mechanisms to identify and block phishing emails, reducing the risk of malware delivery.
- Ensure timely updates and patches for all software to address known vulnerabilities.
- Segregate critical systems and sensitive data from the rest of the network through network segmentation to limit lateral movement.
- Deploy comprehensive endpoint protection solutions to detect and block malware and ransomware, safeguarding devices from compromise.
- Collaborate with cybersecurity organizations and law enforcement agencies to share threat intelligence and stay informed about emerging threats.
- Develop and regularly update an incident response plan to efficiently handle cyber attacks, reducing downtime and minimizing the impact of a breach.








