Severity
High
Analysis Summary
A recent cyber espionage campaign linked to threat actors with ties to Belarus and Russia, known as Winter Vivern (aka TA473, UAC0114, TAG-70), has been targeting over 80 organizations primarily located in Georgia, Poland, and Ukraine by exploiting vulnerabilities in Roundcube webmail servers to potentially steal sensitive information.
These flaws allow the attackers to inject malicious JavaScript payloads to grant them unauthorized access and the ability to exfiltrate user credentials to a hidden command-and-control (C2) server. Spanning from early to mid-October 2023, this campaign raises serious concerns not only due to its technical finesse but also due to its targeted nature and potential motives. Government and military entities in the targeted regions alongside Iranian embassies in Russia and the Netherlands and the Georgian embassy in Sweden all found themselves in the crosshairs of this espionage operation. Researchers believe that the attackers aimed to gather intelligence on various aspects including European political and military activities.
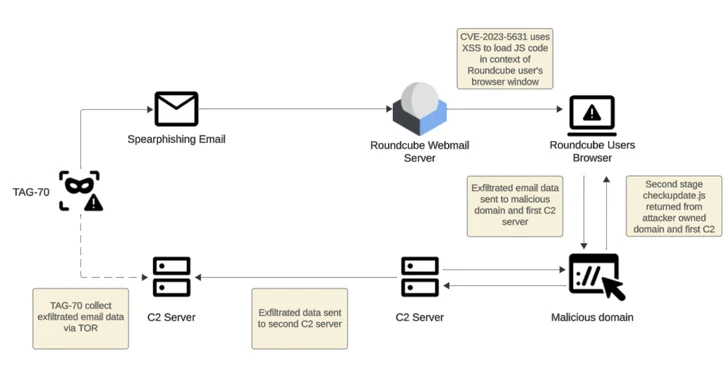
What makes this campaign particularly alarming is the level of sophistication employed by TAG-70. They cleverly combined social engineering techniques with their technical exploits, enabling them to bypass the defenses of even well-guarded organizations. This highlights the ever-evolving tactics of cyber espionage actors, requiring organizations to constantly adapt and strengthen their security postures. The use of XSS vulnerabilities further amplifies the need for vigilance. Web applications like Roundcube, despite their popularity, remain susceptible to such attacks. Patching vulnerabilities promptly and implementing stricter email security measures including strong passwords and multi-factor authentication are crucial steps in mitigating these risks.
Organizations in the targeted regions in particular should be on high alert by remaining aware of social engineering tactics and phishing attempts, along with ongoing monitoring and security awareness training for employees can significantly bolster their defenses. The Winter Vivern campaign serves as a stark reminder of the ever-present threat of cyber espionage. By understanding the methods and motivations behind such attacks, organizations can better equip themselves to stay ahead of the curve and protect their sensitive data from falling into the wrong hands.
Impact
- Cyber Espionage
- Sensitive Information Theft
Indicators of Compromise
Domain Name
- hitsbitsx.com
- ocsp-reloads.com
- recsecas.com
MD5
- acb9415b25b3b834ad9d44aa1e6b3c6c
SHA-256
- ea22b3e9ecdfd06fae74483deb9ef0245aefdc72f99120ae6525c0eaf37de32e
SHA-1
- 3d2281befc99f3fa359e90757bd13fdae760c712
Remediation
- Upgrade to the latest version of Roundcube, available from their website.
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Never trust or open links and attachments received from unknown sources/senders.
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Patch and upgrade any platforms and software timely and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Raising awareness among users about the risks associated with downloading apps from unknown or untrusted sources is crucial. Users should be educated about the importance of verifying app permissions and conducting background research on developers before installing apps.
- Implement reputable mobile security solutions on devices that can help detect and block malicious apps. Mobile antivirus and anti-malware software can provide an additional layer of protection against potential threats.
- Maintain regular and secure backups of critical data, ensuring that data can be restored in case of a cyberattack.
- Employ network monitoring and intrusion detection systems to detect and respond to suspicious activities in real time.
- Enforce the principle of least privilege, granting users only the minimum access required to perform their tasks.

