

Rewterz Threat Advisory – Multiple Apache Batik Server-Side Vulnerabilities
August 23, 2023
Rewterz Threat Advisory – ICS: Mitsubishi Electric MELSEC WS Series Vulnerability
August 23, 2023
Rewterz Threat Advisory – Multiple Apache Batik Server-Side Vulnerabilities
August 23, 2023
Rewterz Threat Advisory – ICS: Mitsubishi Electric MELSEC WS Series Vulnerability
August 23, 2023Severity
High
Analysis Summary
In a recent development on June 28th, researchers made an interesting discovery regarding Android APK analysis. They noticed that Joe Sandbox had introduced an Android APK that posed challenges for most anti-decompilation tools. This APK was designed in such a way that it could not be effectively analyzed, and was installable on Android devices operating on an OS version higher than Android 9 Pie (API 28).
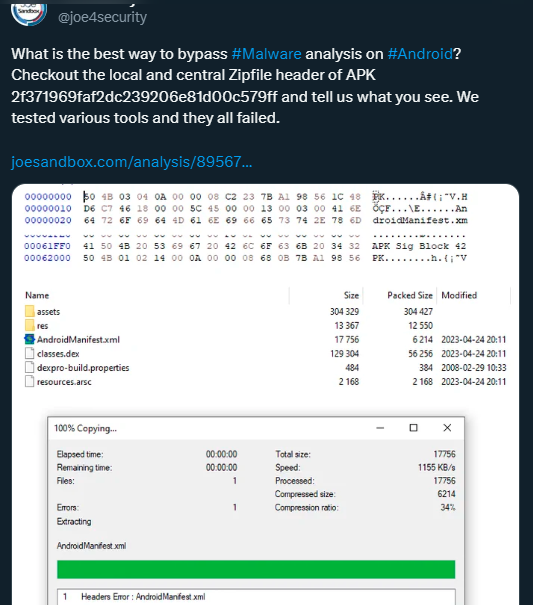
While this technique might appear novel, it’s worth noting that a similar approach was demonstrated back in 2014. Researchers had then shown how the compression algorithm employed within an APK could be manipulated to evade automatic script analysis and hinder static analysis.
“However, Android’s APK, which uses the ZIP format, supports only two compression methods. One is without any compression, i.e. the STORED method (0x0000), and the other is the DEFLATE (0x0008) compression algorithm. Depending on the Android version, the default behavior for unknown or unsupported methods differs”, the report added.
The report also elaborates on the compression methods used in Android’s APK, explaining that it supports only two primary methods: STORED and DEFLATE. The behavior of the system varies based on the Android version when encountering unknown or unsupported methods:
- For Android 4.3 and below: If the method doesn’t match DEFLATE, the system assumes the STORED method has been used.
- For versions greater than Android 4.3: If the specified method doesn’t match, the system assumes DEFLATE compression.
On versions below Android 9, applications that use unsupported or unknown compression methods are not installable, but they function correctly on versions above this.
The experts embarked on a retrohunt through public application repositories and unearthed approximately 3,300 artifacts employing these particular compression algorithms. While most of these samples were too corrupted for the operating system to load, a subset of 71 malicious samples could be properly loaded by the Android OS.
An intriguing aspect is that the researchers could not find any indication that these apps were available on the Google Play Store. This suggests a possible distribution through third-party stores or the exploitation of social engineering tactics to manipulate victims into installing them.
Moreover, they also detected additional techniques used to obfuscate the APK files and thwart analysis tools. These included strategies like employing filenames with excessive length (more than 256 bytes), incorporating malformed AndroidManifest.xml files, and introducing a Malformed String Pool.
In conclusion, this revelation sheds light on a sophisticated evasion technique that adversaries can leverage to evade analysis of their malicious APKs. The combination of using specific compression methods and employing various obfuscation tactics serves as a reminder of the evolving challenges in the realm of mobile app security and analysis.
Impact
- Information Theft
- Evasion of Analysis
Indicators of Compromise
MD5
- 3dcdba556324fea865dc4d25e76c5144
- 73020a7b5b23911172c1ef3d0f9073ee
- 6cacc5fa594bf93ab8e96914ec2f56af
- ae4a091285eb663b682ef611a4556dae
- a892ea08948335211a588b6988882ef1
- 76a3531a3fc52eaa34161971d1ac94eb
- 6aaacf7b7cc3b340c9876ad17a115ccb
- e6432ad9812aabd0a165cdbae3c9fd9d
- 89d924cecea5abbfd8e95d94ea03a355
- 07f777992d646227d35bb5b9100e56da
- 535a56f01fbe16a3b0cff4a5026e481d
- 050f9eafd4e663c5903d4d102d0263e7
- c8a31cfbe4e7f863d4e837fc0048d543
- 112e0b971d7061ece0495288adf19397
SHA-256
- 8a81ae6b6e9d57e5a8488ff0e1531fd86434ea93dd3bc6d2d5b03be96b5f90fe
- 3ddd867f47ab3b822690fdf56e2159ee5315b0990a4a5758f032373139fcb1a9
- 0278ecf7616cdf0970a755027ea95ba6295f34e778d741c52c4fe9cae5c541b1
- 9a34f00048c729359c006f3e486cc0f1ba373a5eb01ee6c62de4baef6ed4af8c
- 1cf4dd2a7f4102d208c54cf7ee7f5df9af3393ce3f87379040af28868de4829d
- b9af1bf509480059449f9166e048003c8f03f8d64ea8a6fb517b866512a0b755
- ebe384dfe8d4f8d23faa1ed07a40c72e0d6eff848ed963b0536e5264a875bd92
- a77f3cfac151fc7fa263febcec64bde20d8f176dcd8da512bb668e01b9ca2602
- b8200525622b1fab3245a076018aea18a613f4b64e9ae4969ed49c875c87bc3e
- 27279b62d681b7ebe46e0f7bae75e1c6e64e52819f72a33b0a8dcbd80363cdf0
- 1cab0e8d2c1a8665bf293b4046663ab9fda7158883b19087e7c4fa56fd01acf3
- 00c23ff1949927c7517b0876d7e64e186be28f853fec09662e3abda1da60876a
- ab390ed662e29cba27e6da2f1ecef53cb31959170e763fdd88b2f5f5bb3db6bd
- 37cdf1d157b4084c463b079cf80b581b3a8d1e0f9ed1fb51ef6753f31d44bb8e
SHA-1
- 09992f196bca6625d497c5a5e46ef1e617ae6643
- 30327e8a44ab206244896a3d4b434073214216b5
- c0e7c1e9020c0b61afc33f8d5000ade0abe1c003
- 359f2ef319168f9e7ef3dfd3a29a74f57d4955df
- fffebc8571ee7f7e9bc3cd4a7ee5d8335adf8e2d
- 4105b9b7d368409786e8a9fe8e4fea16f25faffb
- 4606c1a6744fb77e65834bcdcf1a8dc1d6e2cae6
- bb59d7831e86708e9bed2b05ad4f94a47b65a717
- 7553fe94736400759a1ff47711b9fb5bc1d7ace4
- 0f64f30d6086eb98ba9cb6c355c8e94d38799245
- 09eefbb91187a5c4c71bdcb24764e9e07d621027
- d2c6d985e5699d52dbcb204050789a4f451a681a
- 65d93e97a9727678e477356c1990492fb7447aad
- 128d444812e5c77b2e739bc2928dc07a50ad04ae
URL
http://shone.endeavour31.alpansa.ru/DESKTOP-3VASB0N/falcon/family.n64
Remediation
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Patch and upgrade any platforms and software timely and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Encourage users to only download and install apps from trusted sources, such as the official Google Play Store. Sideloading apps from third-party sources increases the risk of installing malicious applications.
- Educate users about the dangers of clicking on links or downloading apps from unknown sources sent via email, text messages, or social media. Phishing attacks can trick users into installing malicious apps.
- Users should review app permissions before installation. If an app requests unnecessary or excessive permissions, it might be suspicious.
- Install reputable mobile security apps that offer real-time threat detection and malware protection. These apps can help identify and block malicious apps before they are installed.
- Regularly scan your device for malware using security apps. This helps identify any potentially malicious apps that might have been inadvertently installed.
- Security software providers should continually update their tools to detect and mitigate new and sophisticated evasion techniques.
- App stores should enforce strict guidelines for app submissions to ensure that only legitimate and secure apps are made available to users.
- Encourage users to report suspicious apps to app stores or security researchers. This helps identify and remove malicious apps from circulation.








