

Rewterz Threat Advisory – CVE-2023-20185 – Cisco ACI Multi-Site CloudSec Vulnerability
July 6, 2023
Rewterz Threat Advisory – CVE-2023-35935 – Node.js @fastify/oauth2 Vulnerability
July 6, 2023
Rewterz Threat Advisory – CVE-2023-20185 – Cisco ACI Multi-Site CloudSec Vulnerability
July 6, 2023
Rewterz Threat Advisory – CVE-2023-35935 – Node.js @fastify/oauth2 Vulnerability
July 6, 2023Severity
High
Analysis Summary
RedEnergy is a newly discovered cyber threat known as a “Stealer-as-a-Ransomware” that has been specifically deployed in targeted attacks against energy utilities, oil, gas, telecom, and machinery sectors. This sophisticated malware enables the attackers to extract sensitive information from different web browsers and possesses the ability to function as ransomware.
In the analysis, researchers highlights that the RedEnergy malware employs a deceptive campaign known as “FAKEUPDATES” to trick victims into updating their web browsers. Once inside the system, the malware stealthily extracts sensitive information and proceeds to encrypt the compromised files. The threat actors behind RedEnergy have been using reputable LinkedIn pages to target victims, including a machinery manufacturing company in the Philippines and multiple organizations in Brazil.
The attack chain of RedEnergy involves multiple stages. It begins with users clicking on links to visit the targeted company’s website through their LinkedIn profiles. These users are then redirected to a rogue website that instructs them to install what appears to be a legitimate browser update. However, the downloaded file, known as RedStealer, is actually a malicious executable.
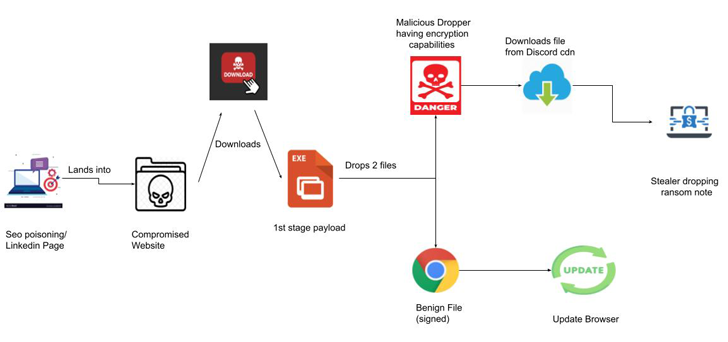
One notable aspect of this threat campaign is the use of a deceptive download domain called “www[.]igrejaatos2[.]org.” This domain disguises itself as a ChatGpt site to lure victims into downloading a fake offline version of ChatGpt. However, the victims unknowingly obtain the same malicious executable mentioned earlier when they download the purported ChatGpt zip file.

The RedEnergy malware sample analyzed by researchers is written in .NET and possesses advanced evasion techniques and anti-analysis features. It communicates with its command and control servers using HTTPS, ensuring encrypted communication. To maintain persistence, the malware stores files in the Windows startup directory and creates an entry within the start menu.
Researchers also observed suspicious activity involving File Transfer Protocol (FTP), suggesting that threat actors may have used this protocol for data exfiltration. In the final stage of the attack, the malware utilizes ransomware modules to encrypt the user’s data, appending the “.FACKOFF!” extension to encrypted files and deleting backups. A ransom note is dropped, demanding payment in exchange for decrypting the files.
The analysis concludes by emphasizing the evolving and highly sophisticated nature of cyber threats targeting various industries. It underscores the critical importance of implementing robust security measures, promoting user awareness, and ensuring prompt incident response to effectively mitigate the impact of such attacks. By remaining vigilant and implementing comprehensive cybersecurity strategies, businesses can better protect themselves against these malicious campaigns and safeguard their valuable data.
“It is crucial for individuals and organizations to exercise utmost caution when accessing websites, especially those linked from LinkedIn profiles. Vigilance in verifying the authenticity of browser updates and being wary of unexpected file downloads is paramount to protect against such malicious campaigns.”, the researchers added.
Impact
- Sensitive Information Theft
- File Encryption
- Financial Loss
Indicators of Compromise
Domain Name
2no.co
MD5
- fb7883d3fd9347debf98122442c2a33e
- cb533957f70b4a7ebb4e8b896b7b656c
- 642dbe8b752b0dc735e9422d903e0e97
SHA-256
- 94df97f56ad0b323684f14b54ab8858af8e9c0a442ce31e07c342fbbb41de5cc
- 2522e04f7abcd7c32d2c73aa0e66d97d0d121e86aefc7e715dd013e8e27a73f3
- 2f489f6462ba4887dee89aa32aad464d5933dc3f4913ec55456e13b28fc3c01f
SHA-1
- 0a93dc2350161bd426113e957dc9eba053c6424f
- 8dc548ad87effd3d448f2ef9c313d7cd2c02875f
- df40a22f138548f4af363766eec48a4ea8b11faf
Remediation
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Maintain Offline Backups – In a ransomware attack, the adversary will often delete or encrypt backups if they have access to them. That’s why it’s important to keep offline (preferably off-site), encrypted backups of data and test them regularly.
- Conduct regular backups of your important data and ensure that these backups are stored offline or in a separate network. This will help protect your data from being compromised by ransomware attacks.
- Deploy advanced threat detection and monitoring solutions to identify potential ransomware activity in real-time. Monitor network traffic, system logs, and behavior anomalies to detect and respond to ransomware incidents promptly.
- Educate users, especially system administrators and IT professionals, about the risks of downloading software from unofficial sources or clicking on suspicious ads. Encourage them to verify the authenticity of websites before downloading any files.
- Enable antivirus and anti-malware software and update signature definitions in a timely manner. Using multi-layered protection is necessary to secure vulnerable assets
- If a device on the network has been infected with ransomware, immediately disconnect it from the network to prevent the malware from spreading to other devices. This will help contain the attack and limit further damage.
- Employ web filtering solutions that can identify and block malicious ads or websites. These solutions can prevent users from accessing malicious sites and clicking on potentially harmful links.
- Deploy a centralized logging system to collect and analyze logs from various network devices and systems. This will enable real-time monitoring of network traffic, user activities, and system logs to promptly detect any unusual or suspicious behavior.
- Develop a robust incident response plan that outlines the necessary steps and procedures to be followed in the event of a breach. This plan should provide clear guidance on containing and mitigating the incident. Additionally, establish effective communication channels to promptly inform relevant stakeholders, including employees, customers, and regulatory bodies, about any breaches that occur and the measures being taken to address them.








