

Rewterz Threat Advisory – Multiple Embedded TCP/IP Stacks Multiple Vulnerabilities
December 9, 2020
Rewterz Threat Alert – Phishing Email Using ‘Low Storage Warning’ as Lure
December 10, 2020
Rewterz Threat Advisory – Multiple Embedded TCP/IP Stacks Multiple Vulnerabilities
December 9, 2020
Rewterz Threat Alert – Phishing Email Using ‘Low Storage Warning’ as Lure
December 10, 2020Severity
High
Analysis Summary
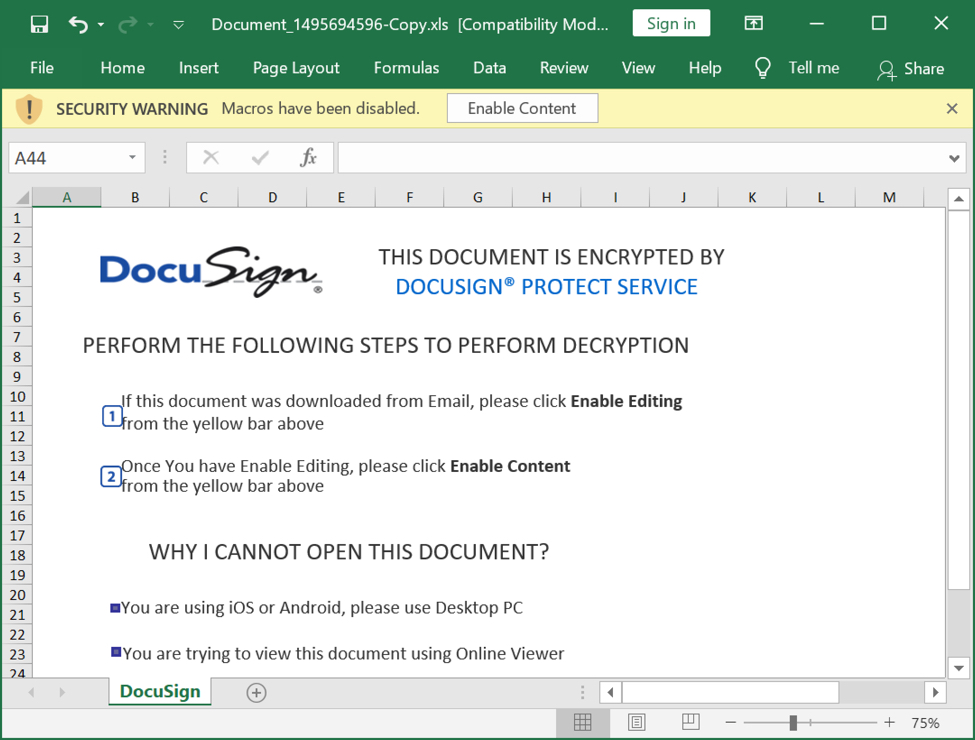
A recent QakBot malspam campaign is detected in which threat actors used fake replies to legitimate email chains along with DocuSign lures to target victims. Moreover, in late-November 2020, Qakbot underwent a version update. The campaign begins with malspam, having ZIP archive as attachments. Upon execution, an excel spreadsheet is extracted that contains embedded macros. When macros are enabled, communication with a malicious URL is established, that drops a DLL for Qakbot on target system.
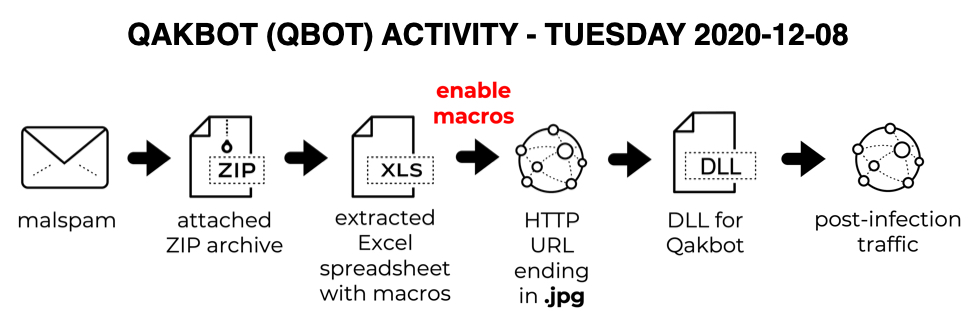
Later, post-infection traffic on a vulnerable Windows host with Qakbot malware can be seen. Even with the version update, these spreadsheets distributing Qakbot have the same template we’ve seen for the past several months. Qakbot has been active for several years, and it continues to evolve. The latest version update has some significant changes, but infection traffic on vulnerable Windows hosts remains similar to what we’ve seen before with Qakbot. The Qbot botnet is using a new template for the distribution of their malware that uses a fake Windows Defender Antivirus theme to trick you into enabling Excel macros. Otherwise known as QakBot or QuakBot, Qbot is a Windows malware that steals bank credentials, Windows domain credentials, and provides remote access to threat actors who install ransomware. Victims usually become infected with Qbot through another malware infection or via phishing campaigns using various lures, including fake invoices, payment and banking information, scanned documents, or invoices.
Impact
- Credential Theft
- Unauthorized Access
- Theft of banking information
- Unauthorized Code Execution
- Information theft
Indicators of Compromise
Domain Name
- supyouryoga[.]com
MD5
- eab3ae82721b551be63502b18ecf3825
- 651725c61d1aee1946d7b748d0ec5afa
- 25beaeae50c5344cca2302b0d6f16205
- 80d75d32c5a459e6b8e2eb47b23fd59c
- e758a4b1340fd50274edefd581cd8c52
- 9e980272bfd728084e6661b05f442541
- 7e233554c276988f2bde5c6d52ee180e
- 98b64d70fa142b05724dc57c2f8090c7
- a5496911ff231fa1b5e8447588e621db
SHA-256
- e14f6ab34e3506d6985816af85935932fb6faf8bad9d2c7dd96d6011d7c21a33
- adad807fa22f398e0a40396ed65d0827f9f14baf7e1281b713dfb17e2683d743
- 94d759f43bcc647f7233e19ddc160a6b43458dcde6d2ea4274c8c06b2890def2
- 5060806228d3f2c1afd09566d0d2fa6b2e56f844cd044c4c4e6e7ade9fef3a22
- 4e2f37d4228e78faa1f34121ee934f58e1a9862ad6f183edf4c24e08cda20363
- 66036cf566386c159e49191125497c77c13c75778492519000b9f61a4afdedad
- 2ccc14f2bab2e9eb1d7228e225afda558fd4b52ed670303a912ace1984b35b06
- 0a3a6163a5e8e372fa96efbef3feb793463f4e39bd2c4d6ea03afce045f90636
- 8f58b499a44ce785b2fec5255d6cd6bbaca52f2991635aec7b7b29c96787fb6f
SHA1
- 1659464cc4364cbad38e1aa36e12931e68e77d6b
- 85b35fdbcda8a15fc3fda26874d5dcdbafeee995
- ed39d9ce2f58de74bba5fca366bff9886698ad94
- fd61aae477cb65bc5f4f7d3be242734793667d63
- 945f507232ddbe940e09ac69a4e8592aa55590ed
- 1b2434d3f1148f1900ff026122e49c3f8092f819
- a515688ce5655db73a164bf471d5c92e75a4e0a7
- dd5bc2d0e0a1459705132fa54c561916f541f0ab
- 3f473e4252a9bbad4e62270c7383409ea015ed2c
Source IP
- 62[.]38[.]114[.]12
- 54[.]36[.]108[.]120
- 197[.]45[.]110[.]165
URL
- http[:]//supyouryoga[.]com/svgqcnjto/590906[.]jpg
Remediation
- Block the threat indicators at their respective controls.
- Do not download files attached in untrusted emails.
- Do not enable macros for untrusted files.








