

Rewterz Threat Alert – Trickbot Malware- Active IOCs
April 28, 2021
Rewterz Threat Alert – Donot APT group – IOCs
April 28, 2021
Rewterz Threat Alert – Trickbot Malware- Active IOCs
April 28, 2021
Rewterz Threat Alert – Donot APT group – IOCs
April 28, 2021Severity
Medium
Analysis Summary
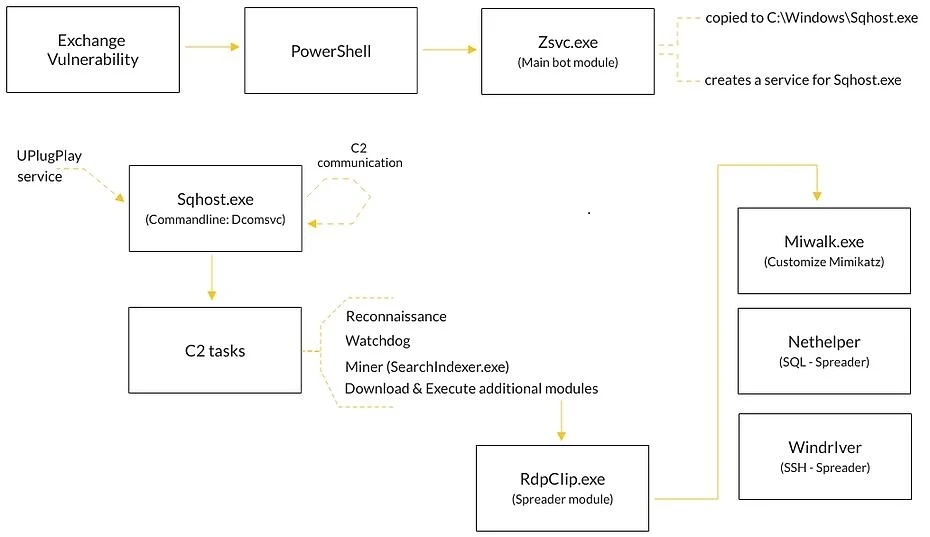
The ProxyLogon flaws in Microsoft Exchange (CVE-2021-26858 and CVE-2021-27065) are being exploited by threat actors for malware deployment or credential harvesting. Prometei targets both Linux-Unix-based systems and Windows-based systems. The above-mentioned flaws were used to deploy the china chopper web shell for persistent access to the network. A module called the “Microsoft Exchange Defender” also masquerades as a legitimate Microsoft function or product.
“Threat actors in the cybercrime community continue to adopt APT-like techniques and improve the efficiency of their operations. As observed in the recent Prometei attacks, the threat actors rode the wave of the recently discovered Microsoft Exchange vulnerabilities and exploited them in order to penetrate targeted networks. This threat poses a great risk for organizations since the attackers have absolute control over the infected machines, and if they wish so, they can steal information, infect the endpoints with other malware or even collaborate with ransomware gangs by selling access to the infected endpoints.”
Impact
- Data Breach
- Hacking
- Credential Harvesting
Remediation
- Update to the latest patches.
- Download from legitimate sources.








