

Rewterz Threat Alert – FASTCash ISO 8583-Specific Windows Malware Identified
March 26, 2019
Rewterz Threat Advisory – Red Hat update for openwsman
March 27, 2019
Rewterz Threat Alert – FASTCash ISO 8583-Specific Windows Malware Identified
March 26, 2019
Rewterz Threat Advisory – Red Hat update for openwsman
March 27, 2019Severity
High
Analysis Summary
A sophisticated, planned supply chain attack has leveraged the ASUS Live Utility Update with a backdoor which is to be believed have impacted over a million users who have downloaded the ASUS Live Update Utility on their computers.
ASUS Live Update is an utility that is pre-installed on most ASUS computers and is used to automatically update certain components such as BIOS, UEFI, drivers and applications.
Based on shared statistics, over 57,000 Kaspersky users have downloaded and installed the backdoored version of ASUS Live Update at some point in time. There were multiple versions of infected ASUS Live Update binaries distributed with every one of them targeting “unknown pool of users, which were identified by their network adapters’ MAC addresses.”
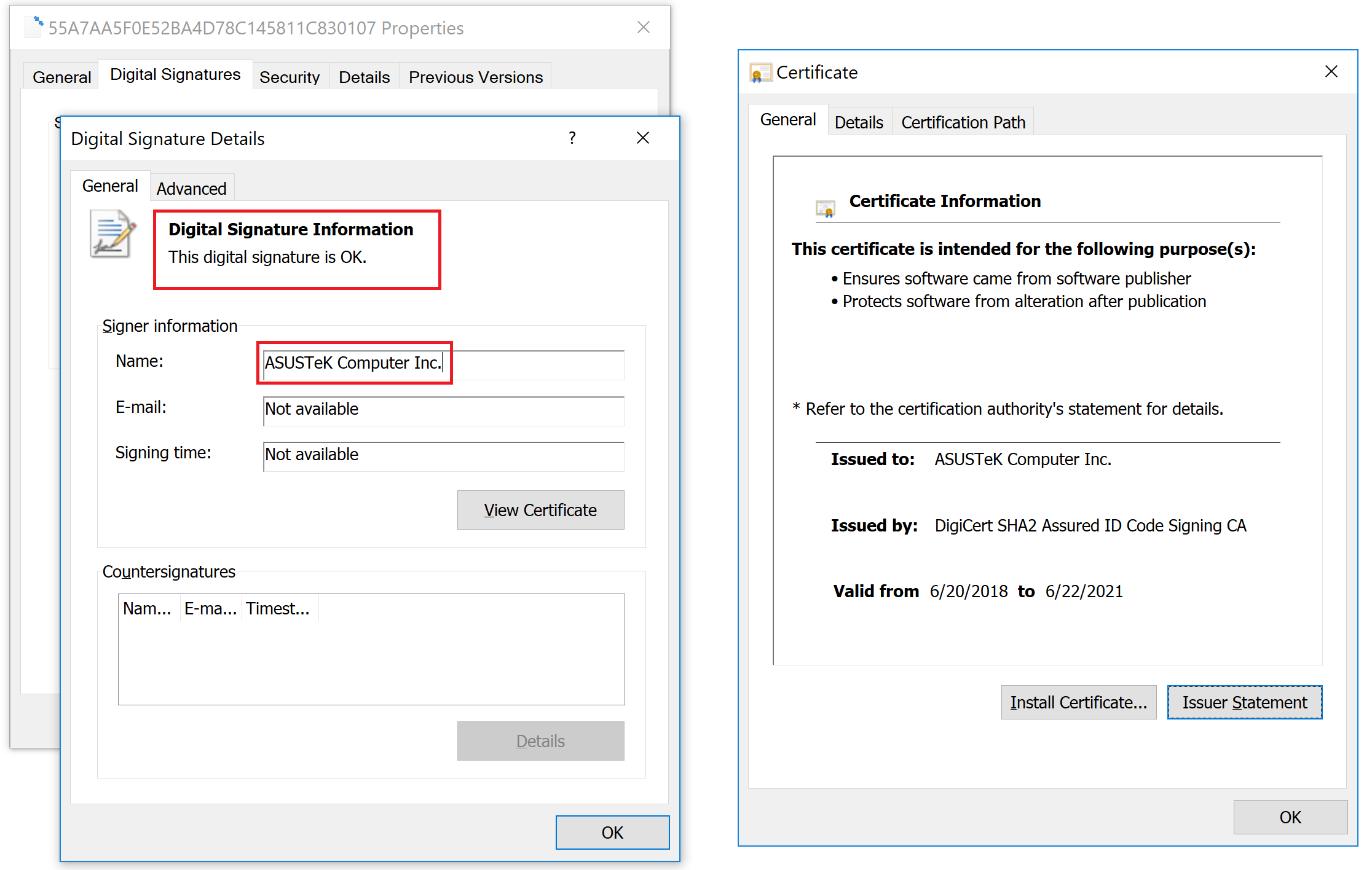
The reason that they remained undetected for such a long time is that that the trojanized updaters were signed with legitimate certificates (eg: “ASUSTeK Computer Inc.”). The malicious updaters were hosted on the official liveupdate01s.asus[.]com and liveupdate01.asus[.]com ASUS update servers.
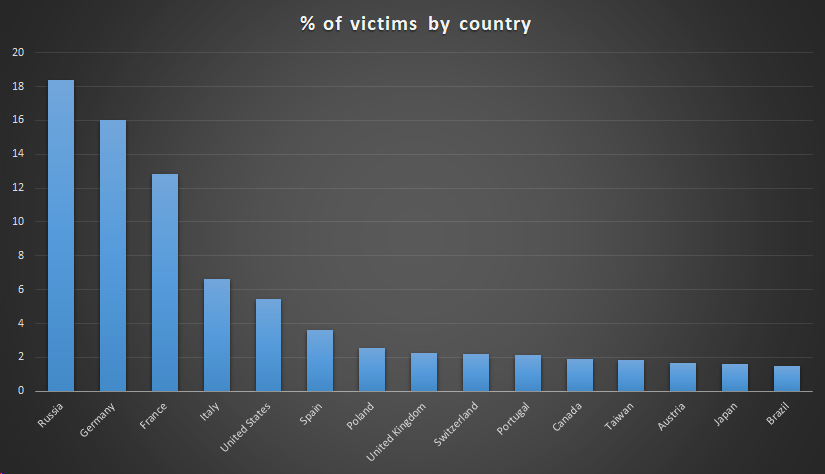
Victim distribution by country for the compromised ASUS Live Updater is as follow.
Impact
Infection of backdoor Trojan.
Indicators of Compromise
| IP(s) / Hostname(s) | 141.105.71[.]116 |
| URLs | simplexoj[.]com https://liveupdate01s[.]asus[.]com/pub/ASUS/nb/Apps_for_Win8/LiveUpdate/Liveupdate_Test_VER362[.]zip https://liveupdate01s[.]asus[.]com/pub/ASUS/nb/Apps_for_Win8/LiveUpdate/Liveupdate_Test_VER360[.]zip https://liveupdate01s[.]asus[.]com/pub/ASUS/nb/Apps_for_Win8/LiveUpdate/Liveupdate_Test_VER359[.]zip http://liveupdate01[.]asus[.]com/pub/ASUS/nb/Apps_for_Win8/LiveUpdate/Liveupdate_Test_VER365[.]zip http://asushotfix[.]com/ homeabcd[.]com asushotfix[.]com |
| Malware Hash (MD5/SHA1/SH256) | aa15eb28292321b586c27d8401703494 bebb16193e4b80f4bc053e4fa818aa4e2832885392469cd5b8ace5cec7e4ca19 |
Affected Vendors
ASUS
Remediation
KasperSky lab has created a tool which can check that if your computer has been the selected target of this attack.
Link to the tool.








