

Rewterz Threat Alert – KingMiner Cryptocurrency Mining Malware
November 28, 2019
Rewterz Threat Alert – Dexphot Malware Hijacked 80K+ Windows Computers to Mine Cryptocurrency
November 29, 2019
Rewterz Threat Alert – KingMiner Cryptocurrency Mining Malware
November 28, 2019
Rewterz Threat Alert – Dexphot Malware Hijacked 80K+ Windows Computers to Mine Cryptocurrency
November 29, 2019Severity
High
Analysis Summary
Active distribution campaigns are running for the newly created DeathRansom ransomware. Initially, the ransomware failed to properly encrypt victims’ files, but now it’s successfully encrypting files on target systems with a constant surge in its distribution.
When DeathRansom is launched it will attempt to clear shadow volume copies. It will then encrypt all files on the victim’s computer other than those found whose full pathnames contain the following strings:
programdata
$recycle.bin
program files
windows
all users
appdata
read_me.txt
autoexec.bat
desktop.ini
autorun.inf
ntuser.dat
iconcache.db
bootsect.bak
boot.ini
ntuser.dat.log
thumbs.db
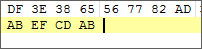
This functional variant does not append an extension to the name of encrypted files. The only way to identify that the file is encrypted by DeathRansom is by the ABEFCDAB file marker appended to the end of encrypted files.
In every folder that a file is encrypted, the ransomware will create a ransom note named read_me.txt that contains a unique “LOCK-ID” for the victim and an email address to contact the ransomware developer or affiliate.
One strange thing that was noticed is that numerous victims who have been infected by DeathRansom were also infected by the STOP Ransomware. As STOP is only distributed through adware bundles and cracks, it is possible the DeathRansom may be distributed in a similar manner.
Impact
- Files Encryption
- Loss of data
Indicators of Compromise
MD5
- d9fef3c67805829cd94b1a35b4ec6ae1
- b6491dcadee919a26e508b3341d0f940
- a35596ed0bfb34de4e512a3225f8300a
- 886ee5834ae019a5c8bce4326b88cfb7
- 38f52fac57482d77b960faff79f44474
- c50ab1df254c185506ab892dc5c8e24b
- 9a65f7be424658a64f8c1112d4d75d7a
- 8ea78e5a123c13c3bda144d0fcf430c0
- f9363e88fde74b43bd7da4528369d7e5
- 4ba2e1d4cf7a86753f9f8174b3bc74c8
SHA-256
- 87d745aa921f201bccb4dd6a6f5af9f0d9c9312114f46779c8980b6f8193f099
- da47aa3b75c85091c708366a8d8534789887b6cc42f42794b0652e280d56a405
- 7c2dbad516d18d2c1c21ecc5792bc232f7b34dadc1bc19e967190d79174131d1
- fedb4c3b0e080fb86796189ccc77f99b04adb105d322bddd3abfca2d5c5d43c8
- 0cf124b2afc3010b72abdc2ad8d4114ff1423cce74776634db4ef6aaa08af915
- ab828f0e0555f88e3005387cb523f221a1933bbd7db4f05902a1e5cc289e7ba4
- 5ac169ed286f20cbb4a18a078f0a090b5771a5155120ffca8bd7f875b38ae8a6
- 13d263fb19d866bb929f45677a9dcbb683df5e1fa2e1b856fde905629366c5e1
- 2b9c53b965c3621f1fa20e0ee9854115747047d136529b41872a10a511603df8
- 66ee3840a9722d3912b73e477d1a11fd0e5468769ba17e5e71873fd519e76def
SHA1
- 80f7907a532c3ca733e4677a1f33f526b216c7c9
- cdf613eb63e007ecb046d5456957016666c3a0e8
- d25e71e5c9dca131b372d9ec7fe9a2eb6adf8221
- 65b5f8cc7b0b6315fe934578f9cad4faf7da41f2
- 81ab3744cefe56a7f4fb3ac49700064fa3f9e183
- aeb09e894736cbb41e934f83cca0247fe89d8a19
- 6ed53078e815301ac7b0c20cdf6c8036f7b393db
- 742128fab2ad05f8f52a4c6f43b39a25fcc161a6
- c28603e1f40933f655f400348018d58b5e709b54
- e61fbe95e09a3ce51b9b2fb836d1018eeef2905a
Remediation
- Block the threat indicators at their respective controls.
- Strictly avoid clicking on random ads found on the internet.
- Do not follow links given in untrusted emails and do not download untrusted email attachments.








