

Rewterz Threat Alert – Fake BleachBit Website Distributes AZORult Info Stealer
September 3, 2019
Rewterz Threat Alert – Astaroth Trojan Uses Cloudflare Workers to Bypass AV Software
September 3, 2019
Rewterz Threat Alert – Fake BleachBit Website Distributes AZORult Info Stealer
September 3, 2019
Rewterz Threat Alert – Astaroth Trojan Uses Cloudflare Workers to Bypass AV Software
September 3, 2019Severity
Medium
Analysis Summary
The operators of Nemty ransomware appear to have struck a distribution deal to target systems with outdated technology that can still be infected by exploit kits.
Exploit kits are not as commonly used since they typically thrive on vulnerabilities in Internet Explorer and Flash Player, two products that used to dominate the web a few years ago but are now with one foot out in the grave.
Nemty appeared on the radar towards the end of August, although the malware administrators made it known on cybercriminal forums long before this date.
It drew attention through its code, which in version 1.0 contains references to the Russian president and to antivirus software.
Security researcher Mol69 noticed that the file-encrypting malware is now a payload in malvertising campaigns from RIG exploit kit (EK).
In the ransom note shown after encrypting the files, Nemty provides instructions on how to pay to recover the data.
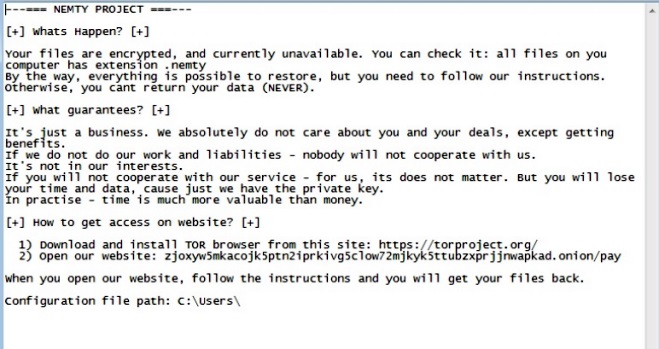
Impact
File encryption
Remediation
- Always be suspicious about emails sent by unknown senders.
- Never click on the link/ attachments sent by unknown senders.








