

Rewterz Threat Alert – New Exploits for Unsecure SAP Systems
May 6, 2019
Rewterz Threat Advisory – CVE-2019-1867 Cisco Elastic Services Controller REST API Authentication Bypass Vulnerability
May 8, 2019
Rewterz Threat Alert – New Exploits for Unsecure SAP Systems
May 6, 2019
Rewterz Threat Advisory – CVE-2019-1867 Cisco Elastic Services Controller REST API Authentication Bypass Vulnerability
May 8, 2019Severity
High
Analysis Summary
A new ransomware campaign dubbed MegaCortex has been observed targeting business networks corporate networks worldwide. Once a network is penetrated, the attackers infect the entire network by distributing the ransomware using Windows domain controllers. Since it is fairly a new ransomware, currently not much is known about their encryption algorithms, exactly how attackers gain access to the network and how the ransom payments are being acknowledged by the attackers.
Initial infection is speculated to start from the Emotet exploit kit. MegaCortex uses both a manual and automated process starting with Meterpreter reverse shell scripts. From there, PowerShell scripts, batch files and remotely executed commands are utilized to execute the final stage malware on specific machines. Once activated, the malware encrypts files on the machine with an undetermined encryption algorithm.
The ransomware note looks like this:
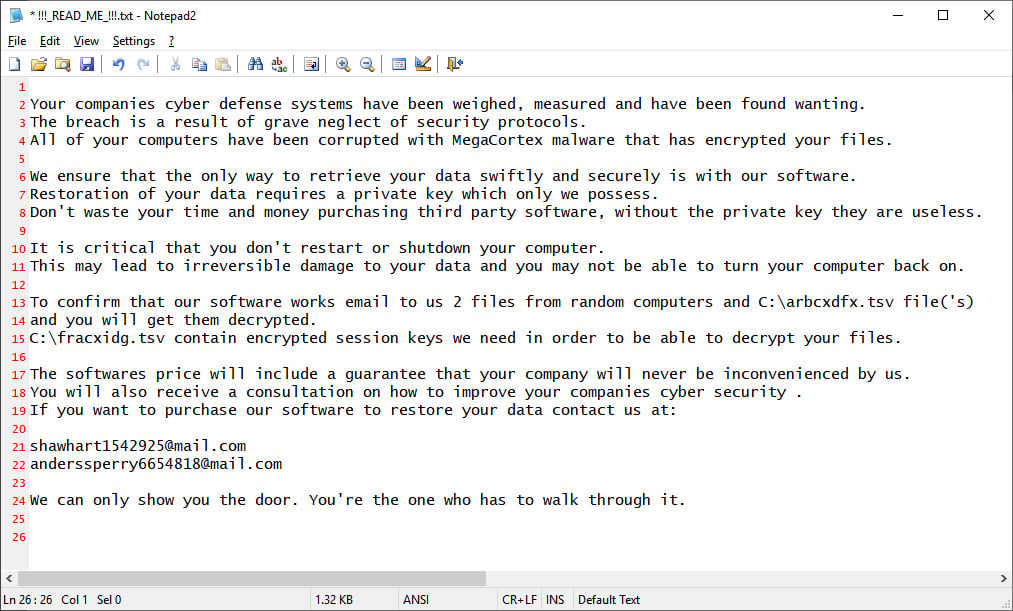
Impact
Loss of sensitive information
Indicators of Compromise
IP(s) / Hostname(s)
89[.]105[.]198[.]28
Email Address
- shawhart1542925@mail.com
- anderssperry6654818@mail.com
Malware Hash (MD5/SHA1/SH256)
478dc5a5f934c62a9246f7d1fc275868f568bc07
Remediation
- Block threat indicators at your respective controls.
- Always have reliable backup of your files.
- MegaCortex ransomware is not being spread via spam, it can be installed via trojans so users must ensure to identify spam and not to open any attachments without confirming.








