

Rewterz Threat Alert – CVE-2019-13522 – EZAutomation EZ PLC Editor Code Execution Vulnerability
September 4, 2019
Rewterz Threat Alert – Cerberus – A Banking Trojan Targeting Banking Apps – IoCs
September 4, 2019
Rewterz Threat Alert – CVE-2019-13522 – EZAutomation EZ PLC Editor Code Execution Vulnerability
September 4, 2019
Rewterz Threat Alert – Cerberus – A Banking Trojan Targeting Banking Apps – IoCs
September 4, 2019Severity
Medium
Analysis Summary
A recent malspam campaign was detected distributing Remcos RAT through email attachments. There were about 300 sending email addresses which were all probably spoofed, and they all ended with @t-online[.]de. The word documents attached in the email have the name resume.doc and they are password protected, using the password 123. The email typically looks like this:

These Word documents have macros which are enabled when the users enter the given password.
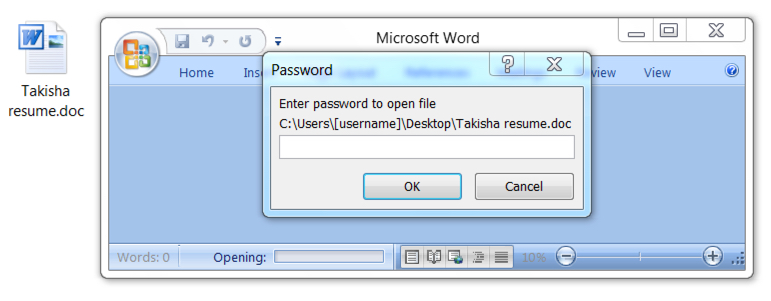
Once macros are enabled, an HTTP request was observed that returned a Windows executable file. In this case, the initial URL ended in .jpg. This was followed by post-infection traffic over TCP ports 2404 and 2405. The initial Windows executable (EXE) file was saved to the user’s AppData\Local\Temp directory. It generated an EXE that was slightly over 400 MB, which kept Remcos RAT persistent on the infected Windows host. This Remcos RAT sample also updated the Windows registry to stay persistent after a reboot. Detection rates on the attached Word documents are very low, since they are encrypted and use password protection.
Impact
- Unauthorized system access
- Key logging
- Code Execution
- Information Theft
Indicators of Compromise
IP(s) / Hostname(s)
- 37[.]19[.]193[.]217
- 104.244.74[.]243
- 209.141.40[.]183
URLs
- hxxp[:]//104[.]244[.]74[.]243/pine[.]jpg
- toptoptop3[.]online
- toptoptop3[.]site
Filename
resume.doc
Email Subject
- Regarding position
- Regarding Job
- Hiring
- Job Application
Malware Hash (MD5/SHA1/SH256)
- 37557e11d5cd33dcb38061c06d3cdc83
- 932505acc15faede0993285532ed6d5afb27ce1c591a0819653ea5813d11cd55
- fa9a94b32f7fa1e1e3eef63d3fb9003fda8d295e1f1a3e521691725e4c7da9f3
- c1bc60587353e61f9ed04b1269eb0afb
- c866c269cd1617ee739216e24ba7cd1b392684b441bcdf10a6c0fdba073fbc28
- 0f5dceeeec65fadb7695b8ade03f8707
Remediation
- Block the threat indicators at their respective controls.
- Do not download attachments from unexpected emails.
- Do not enable macros for untrusted files.
- Be very cautious while handling resume related emails.








