

Rewterz Threat Alert – ATM Malware & Mobile Banking Malware – IoCs
March 4, 2020
Rewterz Threat Advisory – Cisco Prime Network Registrar Cross-Site Request Forgery Vulnerability
March 5, 2020
Rewterz Threat Alert – ATM Malware & Mobile Banking Malware – IoCs
March 4, 2020
Rewterz Threat Advisory – Cisco Prime Network Registrar Cross-Site Request Forgery Vulnerability
March 5, 2020Severity
High
Analysis Summary
The Mailto ransomware has a new technique for process injection. In their article on the topic, researchers discuss the ransomware at a high level along with this new technique. Like many malware payloads, this sample uses process code injection to hide their malicious code within a legitimate Windows process. However, most malware performs process hollowing by creating the target process in suspended mode. The Mailto ransomware, instead, creates the process in Debug mode. Then debug APIs are used to perform the steps necessary to have the legitimate process execute the malicious code. From that point, the ransomware deletes volume shadow copies, establishes persistence via Registry Run key, and performs encryption. Configuration of the encryption process and ransom note is found encrypted within the .rsrc section of the payload in JSON format. Encryption is performed using the SALSA20 algorithm and the extension appended to encrypted files includes the string “mailto,” an email address, and custom ID. The ransom note provides email addresses to which the victim can reach out in order to receive payment instructions for the decryption key.
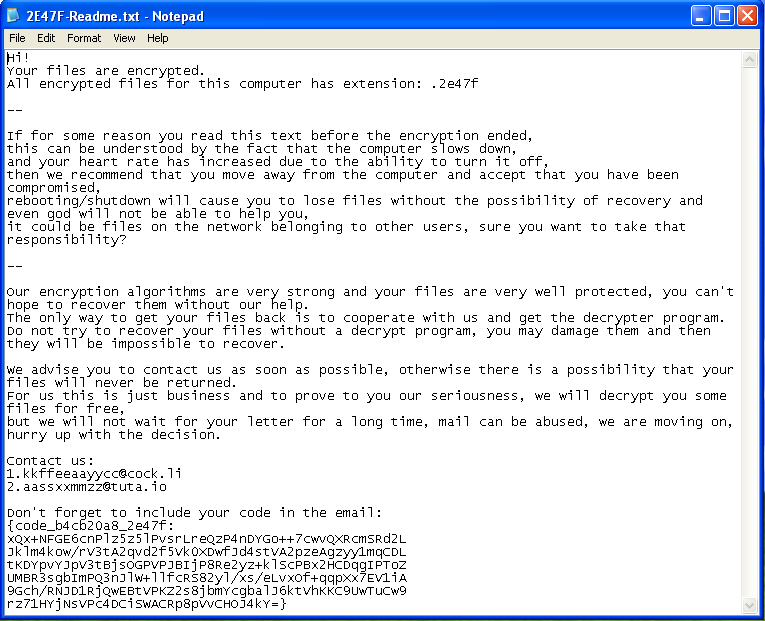
Impact
Files Encryption
Indicators of Compromise
MD5
- 207d2a5aa3a00b8c908b6cffcf6dded8
- 3d6203df53fcaa16d71add5f47bdd060
- 775f5027abc97c0ec8e9202a4ed4cc14
- b0008e752f488d7e97a8d2452411527e
- 73de5babf166f28dc81d6c2faa369379
- d7d7f3c95d03367c61bcfdfe4e7ab47a
Remediation
- Block all threat indicators at your respective controls.
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/attachments sent by unknown senders.








