

Rewterz Threat Advisory – ICS: ABB Multiple System 800xA Products
June 4, 2020
Rewterz Threat Alert – New LNK Attack Tied to Higaisa APT
June 5, 2020
Rewterz Threat Advisory – ICS: ABB Multiple System 800xA Products
June 4, 2020
Rewterz Threat Alert – New LNK Attack Tied to Higaisa APT
June 5, 2020Severity
Medium
Analysis Summary
A PowerShell script (mailer script) has been seen propagating the distribution of Lemon Duck through weaponized COVID-19 themed emails by researchers. Like the long ago “I Love You” virus, these emails are delivered to all Microsoft Outlook contacts of the user of the compromised machine. The emails sent all contain malicious attachments and, should the receiver open and execute the attachments, Lemon Duck cyrptominer is installed. Currently, this script has been observed in China, Bangladesh, Hong Kong, Egypt, and Indonesia. Targeted industries include clothing, conglomerates, real estate, health, electronics, and shipping/logistics companies/finance. The malicious emails come from familiar sources, which could lead recipients to trust and open the emails, thus leading to infection. The emails contain differing subjects and contents as well as document names and types to include .ZIP and .DOC files. Analysis of the code reveals it creates a pipe and waits for input commands. Furthermore, it checks for administrator rights as well as compiling C# source code to load into memory. The only way to terminate the loaded code from memory is to restart PowerShell. The payload generates a JavaScript file and uses that file to send the infected emails to contacts. In a move to further obfuscate the nefarious activity, the script then deletes the sent emails to hide the evidence.
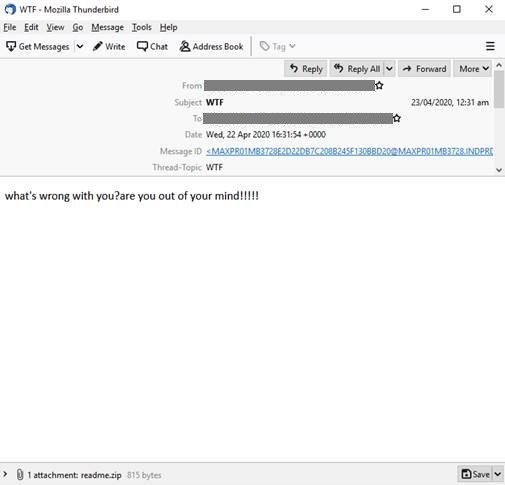
Impact
Cryptocurrency Miner
Indicators of Compromise
SHA-256
- 4ee96a4723b979fbe90683955889088e0e17d896860155dda9699d6892e1d857
- 81405472afd6aa222560a086546831df1564b4b8ccd2c5d630562a2807458738
- 9b2de10b861a26af5360d1bd4636b3fedca98910fb7511737bd84cd026b688e2
Remediation
Block all threat indicators at your respective controls.
Always be suspicious about emails sent by unknown senders.
Never click on the links/attachments sent by unknown senders.








