

Rewterz Threat Alert – OilRig Targets Middle Eastern Telecommunications Organization
July 23, 2020
Rewterz Threat Alert – Cybersecurity Vendors Impersonated in Malicious Activities
July 23, 2020
Rewterz Threat Alert – OilRig Targets Middle Eastern Telecommunications Organization
July 23, 2020
Rewterz Threat Alert – Cybersecurity Vendors Impersonated in Malicious Activities
July 23, 2020Severity
High
Analysis Summary
A recently discovered malware framework known as MATA linked to the North Korean-backed hacking group Lazarus was used in attacks targeting corporate entities from multiple countries since April 2018 for ransomware deployment and data theft.
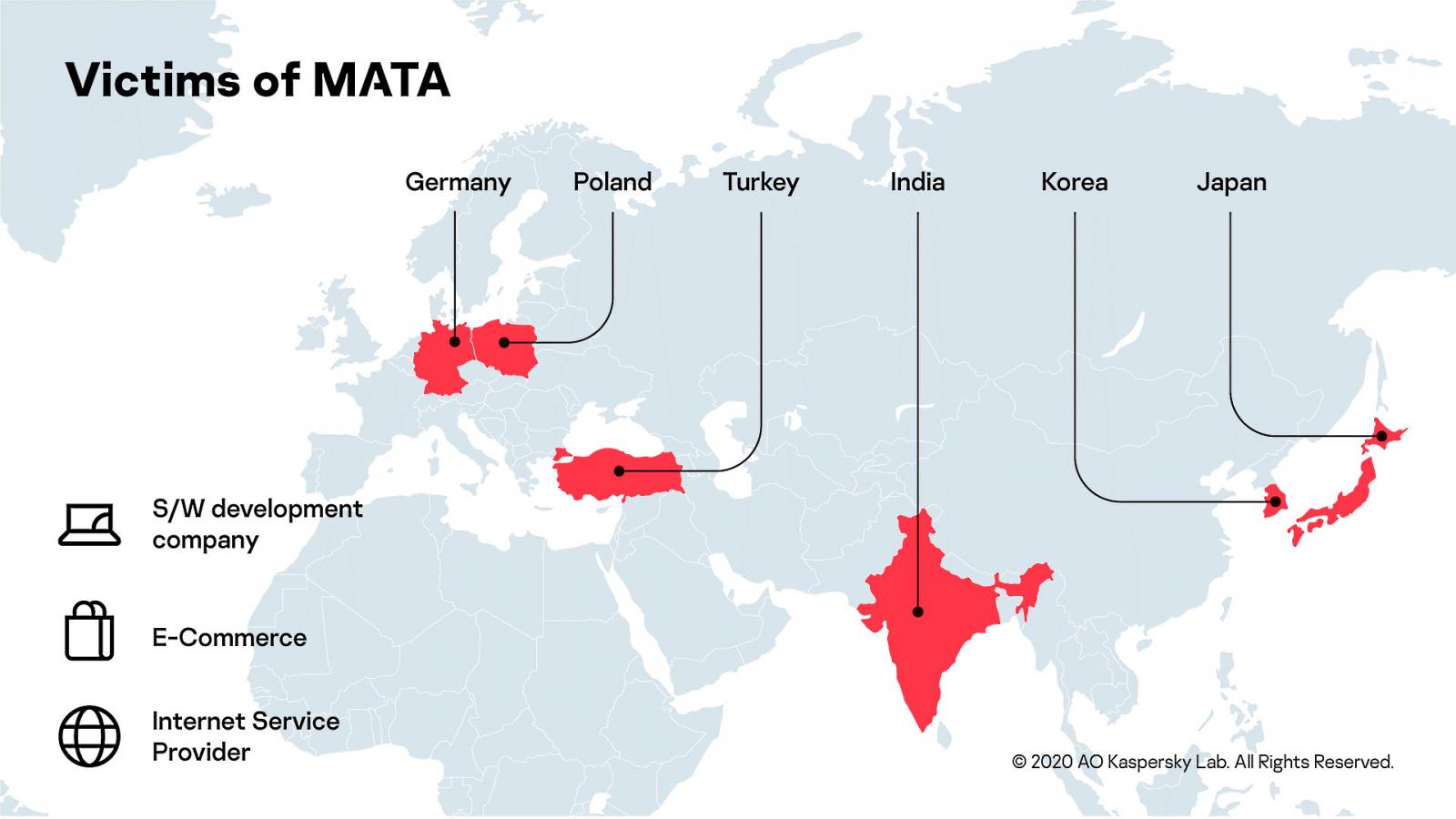
MATA is a modular framework with several components including a loader, orchestrator, and multiple plugins, and it can be used to infect Windows, Linux, and macOS systems.
During their attacks, the hackers can use MATA to load several plugins into the infected system’s memory running commands, manipulating files and processes, injecting DLLs, creating HTTP proxies and tunnels on Windows devices.
MATA plugins also allow the hackers to scan for new targets on macOS and Linux-based machines (routers, firewalls, or IoT devices). On the macOS platform, MATA can also load a plugin_socks module that can be used to configure proxy servers.
Some of the retrieved IoCs are linked to the recent Brazilian Tetrade malware infection chain.
Impact
- Data Manipulation
- Unauthorized command execution
- Data theft
Indicators of Compromise
Domain Name
- paiuew[.]bnorp[.]ml
- 2va6v[.]6pnc3461[.]ink
- 01autogestor[.]ga
- evokgtis[.]gq
- 6zs1njbw[.]ml
- 64pgrpyxpueoj[.]ga
- k8cf0j5u[.]cf
- xvbe[.]monster
- 04autogestor[.]ml
- gurulea8[.]ml
- 84m4bl423[.]space
- kfgkqnf5[.]cf
- ghcco980m1zy9[.]org
- nfiru[.]xyz
- 0ff2mft71jarf[.]gq
- kaligodfrey[.]casa
- 7wpinibw[.]ml
- vuryza[.]ga
- venumxmasz[.]club
- xufa8hy15[.]online
- peolplefortalce[.]gq
- osieofcorizon[.]fun
MD5
- 91b271e7bfe64566de562a8dd2145ac6
- 1b50b1e375244ce5d4e690cf0dbc96d8
- 4194162fe30a3dca6d8568e72c71ed2d
- aeaf7355604685d4d753d21902ff1c1c
- 5ce1eb8065acad5b59288b5662936f5d
- 0219ef20ab2df29b9b29f8407cf74f1c
- c63b4eb3067d8cb5f2d576bc0777e87d
- 071d3d6404826c24188dc37872224b3d
- 0931a26d44f0e7d70fda9ef86ee203f4
SHA-256
- 4eb22da818d15108ceebe699116459a79046716ca695ebc81668c042b7557e2e
- a739b03a7192828b0da31d077609981bf67912a74470bc19cd7e28c9b44761eb
- 86cd8139c074964554c3f674b6f12ec2fe8d8c0765aa7d77117dc099ccf884d8
- ed9277870a1da0080b7b35f2d6a6b9da931161a9e0e362f2bdbf7456c2f23232
- 49190fbebc01eaab9551957ff90c5151fe9104e8fc31ac4cf6038dcdaad01f25
- 4457ba582eca79b16186855ff3dd53ae197c886167c7ffd370b9fe9daff656b3
- 6d27525b615b4bfd10284fda160a454b131ed305d39da4fa640d297316a1225d
SHA1
- 25038daa9f2bd4c0da85ca0a491a0e8ee33649f2
- 6385cf85ba16376a6d22f019ae97194c5eca00a7
- 8db0f9e9258f7f00861b696c25fa7f7054192eb3
- b35ee8162ca3666ae14d60634ac3f1a438d2d3b5
- c24d8e6e8384f6623ebae9cf35bb6bfeee8cc900
- 6ebc6d5f99aafd855ada683ff208eaaedffa1b93
- 2b420bf1a31712098028dcd3651fbef2c66ce802
Remediation
Block the threat indicators at their respective controls.








