

Rewterz Threat Advisory – ICS: Tridium Niagara Information Disclosure Vulnerabilities
September 20, 2019
Rewterz Threat Advisory – CVE-2019-16097 – Critical Bug In Harbor Container Registry Gives Admin Access
September 20, 2019
Rewterz Threat Advisory – ICS: Tridium Niagara Information Disclosure Vulnerabilities
September 20, 2019
Rewterz Threat Advisory – CVE-2019-16097 – Critical Bug In Harbor Container Registry Gives Admin Access
September 20, 2019Severity
High
Analysis Summary
Emotet is back and targeting different users around the world with the phishing campaign. The malicious emails are being sent by 3,362 different senders, whose credentials had been stolen. The count for the total number of unique domains reached 1,875, covering a little over 400 TLDs.
When the Emotet botnet came back to life again, it was using a malicious Word document template that asked you to “Accept the license agreement” by clicking on the “Enable Content” button. Doing so, would enable macros embedded in the document that would then install the Emotet Trojan on the recipient’s computer.

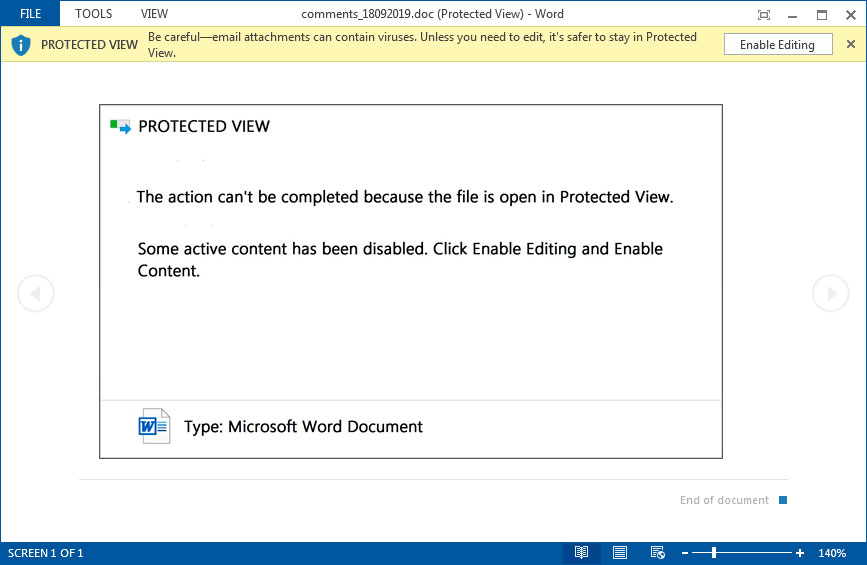
Emotet has changed its malicious document template to use a new “Protected View” lure. This lure tells the potential victims that the “action can’t be completed because the file is open in Protected View. Some active content has been disabled. Click Enable Editing and Enable Content.”
Impact
- Credential theft
- Exposure of sensitive information
Indicators of Compromise
URLs
- hxxps[:]//sarkargar[.]com/blogs/fNjYoum
- hxxp[:]//electroenchufe[.]com/wp-content/13c3yqv_eo4zsu9-416/
- hxxp[:]//www[.]foxrpas[.]com/wp-admin/vhvkpXHSH/
- hxxp[:]//www[.]syds588[.]cn/cgi-bin/FuevrLxGga/
- hxxps[:]//thongtindonganh[.]vn/wp-content/l5wmd_j25t5jm5-9/
- hxxps[:]//teccenter[.]xyz/cgi-bin/iSqyoMMzct/
- hxxps[:]//87creationsmedia[.]com/wp-includes/zz90f27/
- hxxps[:]//www[.]cityvisualization[.]com/wp-includes/88586/
- hxxps[:]//codenpic[.]com/wandervogel/70mja4/
- hxxps[:]//codenpic[.]com/wandervogel/70mja4
- hxxps[:]//ecampuskbds[.]com/vngp/v405/
- hxxp[:]//karencupp[.]com/vura1qw/s0li7q9
- hxxps[:]//www[.]rangreality[.]com/images/v7rr7/
- hxxp[:]//pinmova[.]xyz/wp-content/widsraq4685
- hxxps[:]//pronhubhd[.]com/cgi-bin/m0cux6
- hxxp[:]//minmin96[.]xyz/wp-includes/l5vaemt6/
- hxxp[:]//blog[.]medkad[.]com/wp-admin/e9684
- hxxp[:]//thefortunatenutrition[.]com/vuzp4o2vb/h3/
- hxxps[:]//blog[.]medkad[.]com/wp-admin/e9684
- hxxps[:]//87creationsmedia[.]com/wp-includes/zz90f27
- hxxp[:]//pinmova[.]xyz/wp-content/widsraq4685/
Malware Hash (MD5/SHA1/SH256)
- 06c8514f5077d75a19b3d79b3d16531faff38ec2e6dd7b25c8259cd4d78e91b9
- fae8dc60abbfb644583d97f10776d337
- 2402ef25acb4c2bae1e769b2a51e146e
Remediation
- Block all threat indicators at your respective controls.
- Always be suspicious about emails sent by unknown senders.
- Never click on the link/attachments sent by unknown senders.








