

Rewterz Threat Alert – Targeting NATO-Aligned Nations: Russian Threat Actors Focus on Ministries of Foreign Affairs – Active IOCs
August 18, 2023
Rewterz Threat Alert – STOP (DJVU) Ransomware – Active IOCs
August 21, 2023
Rewterz Threat Alert – Targeting NATO-Aligned Nations: Russian Threat Actors Focus on Ministries of Foreign Affairs – Active IOCs
August 18, 2023
Rewterz Threat Alert – STOP (DJVU) Ransomware – Active IOCs
August 21, 2023Severity
High
Analysis Summary
Since April 2023, an ongoing phishing campaign has been actively targeting Zimbra Collaboration email servers globally, as reported by researchers. The campaign operates by sending phishing emails to various organizations worldwide, with no specific sector or entity being singled out. The identity of the threat actor responsible for this campaign remains undisclosed at present.
The attack methodology involves sending phishing emails to potential victims, impersonating administrators from organizations. These emails notify recipients of an impending email server update that will lead to temporary account deactivation. Recipients are instructed to open an attached HTML file to receive details about the server upgrade and instructions on how to prevent account deactivation.
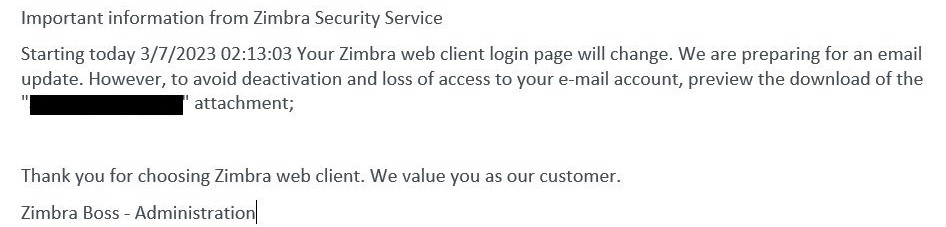
phishing email
Upon opening the HTML attachment, a counterfeit Zimbra login page is presented. This fake page is meticulously designed to feature the logo and branding of the targeted company, adding an air of authenticity. Additionally, the username field in the login form will be prefilled, further convincing the targets of its legitimacy.
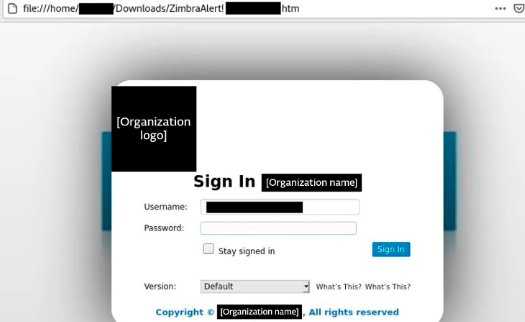
phishing page
Passwords entered in the phishing form are transmitted to the threat actor’s server via an HTTPS POST request. In certain cases, compromised administrator accounts are exploited to establish new mailboxes, which are then used to disseminate phishing emails to other members of the organization.
“One explanation is that the adversary relies on password reuse by the administrator targeted through phishing – i.e., using the same credentials for both email and administration. From available data we are not able to confirm this hypothesis.”
Despite the campaign’s lack of sophisticated tactics, its reach and success are noteworthy. Researchers emphasize that users of Zimbra Collaboration should be cautious of this threat. Zimbra Collaboration email servers are commonly targeted by hackers for activities like cyber espionage, which involves collecting internal communications, or as an initial entry point to infiltrate the target organization’s network.
Earlier in the year, another analysis revealed the ‘Winter Vivern’ hacking group’s exploitation of a Zimbra Collaboration vulnerability (CVE-2022-27926) to gain access to webmail portals of NATO-aligned organizations, governments, diplomats, and military personnel. In a previous instance, a threat actor named ‘TEMP_Heretic’ utilized a zero-day flaw (CVE-2022-23682) in the Zimbra Collaboration product for mailbox access and lateral phishing attacks.
“The popularity of Zimbra Collaboration among organizations expected to have lower IT budgets ensures that it stays an attractive target for adversaries”
In conclusion, the attractiveness of Zimbra Collaboration among organizations with constrained IT budgets continues to make it a sought-after target for adversaries, underscoring the importance of heightened awareness and proactive defense against such phishing campaigns.
Impact
- Credential Theft
- Reputational Damage
Indicators of Compromise
Domain Name
- fmaildd.000webhostapp.com
- nmailddt.000webhostapp.com
- tmaxd.000webhostapp.com
- posderd.000webhostapp.com
- ridddtd.000webhostapp.com
- mtatdd.000webhostapp.com
- zimbra.y2kportfolio.com
IP
- 145.14.144.174
- 145.14.145.248
- 145.14.145.122
- 145.14.144.58
- 145.14.145.36
- 173.44.236.125
URL
- https://fmaildd.000webhostapp.com/wp-admin/ZimbraNew.php
- https://mtatdd.000webhostapp.com/wp-admin/ZimbraNew.php
- https://nmailddt.000webhostapp.com/wp-admin/ZimbraNew.php
- https://posderd.000webhostapp.com/wp-admin/ZimbraNew.php
- https://ridddtd.000webhostapp.com/wp-admin/ZimbraNew.php
- https://tmaxd.000webhostapp.com/wp-admin/ZimbraNew.php
- https://zimbra.y2kportfolio.com/wp/wp-admin/ZimbraNew.php
Remediation
- Patch and upgrade any platforms and software timely and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Upgrade to the latest version of Zimbra Collaboration, available from the Zimbra Website: ZImbra Website
- Deploy advanced email filtering and anti-phishing solutions that can identify and block malicious emails before they reach users’ inboxes.
- Conduct regular cybersecurity awareness training for employees to educate them about phishing threats, including how to identify suspicious emails and verify sender authenticity.
- Enforce MFA for all user accounts, requiring an additional layer of verification beyond passwords to access sensitive systems.
- Ensure that the Zimbra Collaboration software and other systems are up-to-date with the latest security patches to mitigate known vulnerabilities.
- Implement web content filtering solutions to prevent users from accessing known malicious websites linked in phishing emails.
- Train users to recognize common phishing tactics, such as urgency, unusual sender addresses, and requests for sensitive information.
- Implement email authentication protocols to verify the authenticity of emails and prevent email spoofing.
- Develop a comprehensive incident response plan that outlines steps to take in case of a successful phishing attack. Test and update the plan regularly.
- Utilize advanced threat detection solutions to identify unusual or suspicious activities within email systems and networks.
- Implement network segmentation to limit lateral movement within the network in case of a successful compromise.
- Implement behavioral analytics solutions to detect unusual patterns of behavior, especially when it comes to user login and access activities.
- Conduct regular security audits and assessments to identify vulnerabilities and weaknesses in the organization’s email and network infrastructure.
- Assess the security practices of third-party vendors that have access to your systems to prevent potential compromise through supply chain attacks.
- Establish a clear and easy reporting mechanism for employees to report suspicious emails or activities, encouraging prompt action.
- Implement encryption for sensitive data stored within email servers to prevent unauthorized access in case of a breach.
- Regularly back up critical data and systems, storing backups in offline and secure locations.








