

Rewterz Threat Advisory –CVE-2021-33514 – NETGEAR Command Injection Vulnerability
August 5, 2021
Rewterz Threat Advisory –CVE-2021-1572 – Cisco Network Services Orchestrator Security Vulnerability
August 5, 2021
Rewterz Threat Advisory –CVE-2021-33514 – NETGEAR Command Injection Vulnerability
August 5, 2021
Rewterz Threat Advisory –CVE-2021-1572 – Cisco Network Services Orchestrator Security Vulnerability
August 5, 2021Severity
Medium
Analysis Summary
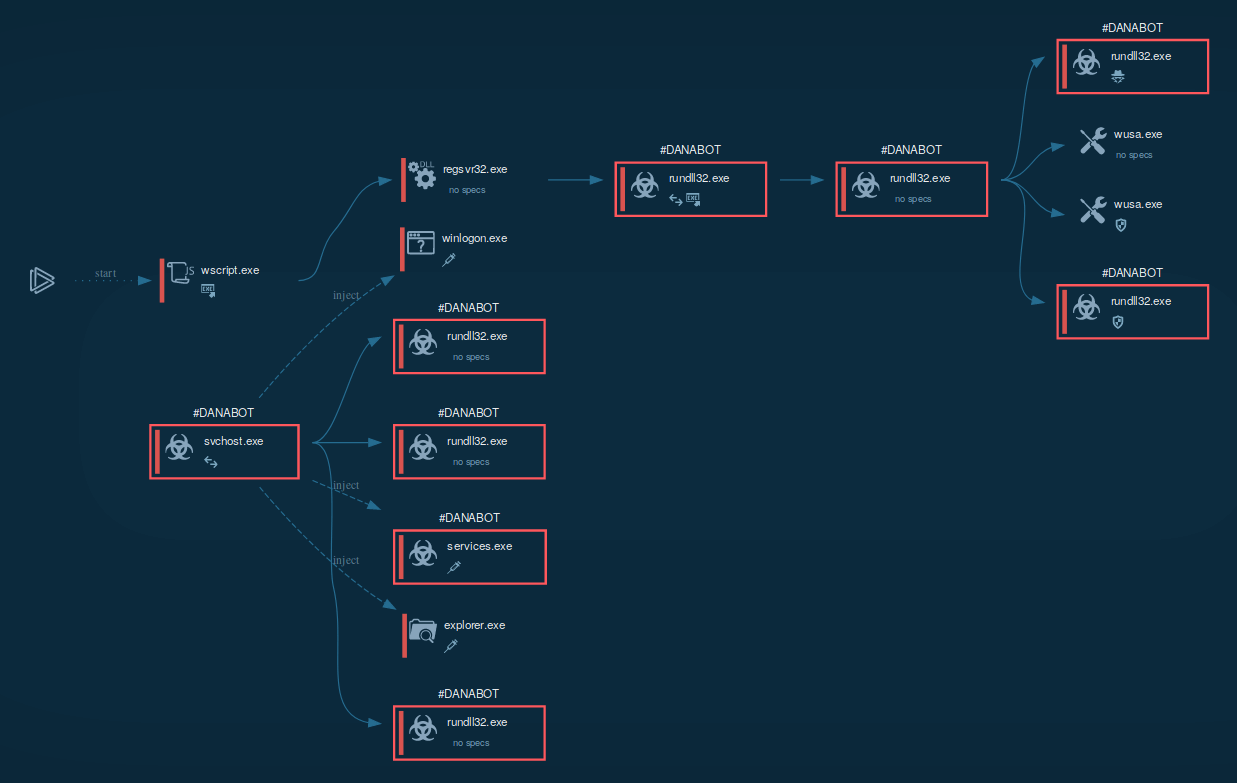
New fourth version of the DanaBot banking trojan has surfaced after months of inactivity. This most recent variant comes packed mostly with the same deadly arsenal of tools that have come before. Main features include a ToR component to anonymize communications between the bad-guys and an infected hardware. As previously reported in DanaBot control panel, DanaBot is set up as a ‘malware as a service’ in which one threat actor controls a global command and control (C&C) panel and infrastructure then sells access to other threat actors known as affiliates,”.
DanaBot’s multi-stage infection chain starts with a dropper that triggers a cascading evolution of hacks. These include stealing network requests, siphoning off application and service credentials, data exfiltration of sensitive information, ransomware infection, desktop screenshot spying and the dropping of a cryptominer to turn targeted PCs into cryptocurrency worker bees. At least one of the DanaBot distribution methods is identified as misuse of various software warez and cracks websites that supposedly offer software keys and cracks for a free download, including anti-virus programs, VPNs, graphics editors, document editors, and games. However, the files distributed by these sites are a bundle of several different malware, including DanaBot. Earlier Campaign also distributed Danabot with new features.
Impact
- Data Exfiltration
- Information Theft
Indicators of Compromise
MD5
- e0b47c716f0d29997212ccb7c30686a3
- b0f1fad905f5b31d70389bedcfc39caf
- 4fb9499676799097257c5fd4e148b34e
SHA-256
- e83e6702c3b59f275981161db3eabdb589051a4d36ad2d74c34a8fc45cb31a30
- 58dd074be5e51ca44f0c67ed712b3bb7a1afe1723adccdf3491636fef7cf1a2d
- a04cd9695517c7281ffa730523fc49c272dc3d5171745d46e5dd14481a9dcd4c
SHA-1
- 769ec389ea80ee13b114ce974fbf82174f56de2b
- e5c9649d885178e8a313b63a6884b8cac99e6402
- a2f75a5424947dd4da9584e8c5f3be00644ba1ca
Remediation
- Block the threat indicators at their respective controls.
- Search for IOCs in your environment.








