

Rewterz Threat Alert – Lokibot – Active IoCs
December 21, 2020
Rewterz Threat Advisory – CVE-2020-27338 – Treck TCP/IP Stack Vulnerability
December 21, 2020
Rewterz Threat Alert – Lokibot – Active IoCs
December 21, 2020
Rewterz Threat Advisory – CVE-2020-27338 – Treck TCP/IP Stack Vulnerability
December 21, 2020Severity
High
Analysis Summary
Researchers discovered a campaign that distributed a credential stealer. Researchers also learned that the main code components of this campaign is written in AHK. By tracking the campaign components, it is found out that its activity has been occurring since early 2020. The malware infection consists of multiple stages that start with a malicious Excel file. In turn, this file contains an AHK script compiler executable, a malicious AHK script file, and a Visual Basic for Applications (VBA) AutoOpen macro.
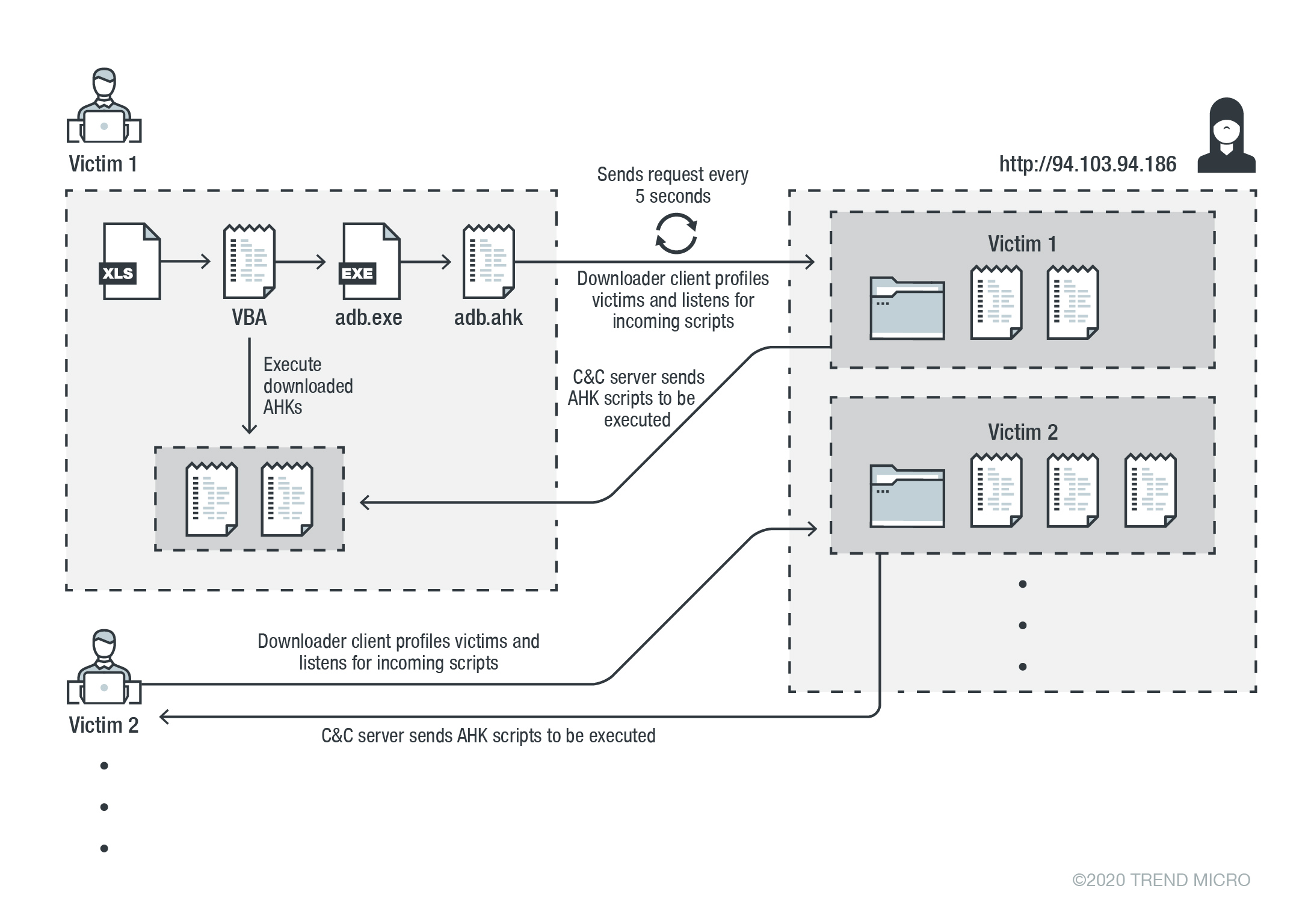
Among the downloaded components by the downloader client, researchers observed a stealer written in AHK. This script is responsible for harvesting credentials from various browsers and exfiltrating them to the attacker.
Impact
- Credential theft
- Exposure of sensitive data
Indicators of Compromise
MD5
- 41190583bbbb2fd7f355c2e42b2d70a3
SHA-256
- dd3087a377ee3d1959f6c17b1b13e5972d1783dfd708bd084150e44c30e3af6e
- d8483908dc0a18c4b51bfe962279816c910fedbad1961e5c5ed081c250cc5f76
- bed925d7c0af493c9ccd2828d6fdefe6f4255bada51f645a8fffdd67e24b87fd
- a1f2606102e59bbc1a6de8912378821e83c32f31f6a402e8f3993ef966746b07
- 27d9eb869eea6c713c6f109eca867844e2feceb0783bda2b78f7a92dffc833f6
- 1994f37501d7fc3038129db09babc5ef67d5ab4c93a95b3b59bf2b5ffa1592ff
- 0078c476753613a78ff9e8f621fd28c1279c0981d519c44212b9d02e5fb4c81c
- bed925d7c0af493c9ccd2828d6fdefe6f4255bada51f645a8fffdd67e24b87fd
SHA1
- 9c9ebef0dc57e363dd3ce03bf2f29d2e6146a2d5
Remediation
- Block all threat indicators at your respective controls.
- Always be suspicious about emails sent by unknown senders.
- Never click on links/attachments sent by unknown senders.








