

Rewterz Threat Alert – Threat Actors Using SUBMARINE Backdoor In Attacks On Barracuda ESG Appliances – Active IOCs
August 1, 2023
Rewterz Threat Advisory – CVE-2023-26139 – Node.js underscore-keypath Module Vulnerability
August 2, 2023
Rewterz Threat Alert – Threat Actors Using SUBMARINE Backdoor In Attacks On Barracuda ESG Appliances – Active IOCs
August 1, 2023
Rewterz Threat Advisory – CVE-2023-26139 – Node.js underscore-keypath Module Vulnerability
August 2, 2023Severity
High
Analysis Summary
The Russia-linked threat-state actor BlueBravo, also known as APT29, Cloaked Ursa, Midnight Blizzard, and Nobelium, has been detected targeting diplomatic entities in Eastern Europe through a spear-phishing campaign. The group’s objective is to infect recipients with a newly identified backdoor called GraphicalProton. This campaign was observed between March and May 2023.
To obfuscate their command-and-control (C2) communications, the threat actors are abusing legitimate internet services (LIS), expanding the range of services misused for this purpose. In January 2023, BlueBravo was observed using a themed lure to deliver another type of malware called GraphicalNeutrino. However, GraphicalProton differs from GraphicalNeutrino in terms of C2 communication, as it now uses Microsoft’s OneDrive or Dropbox for this purpose instead of Notion.
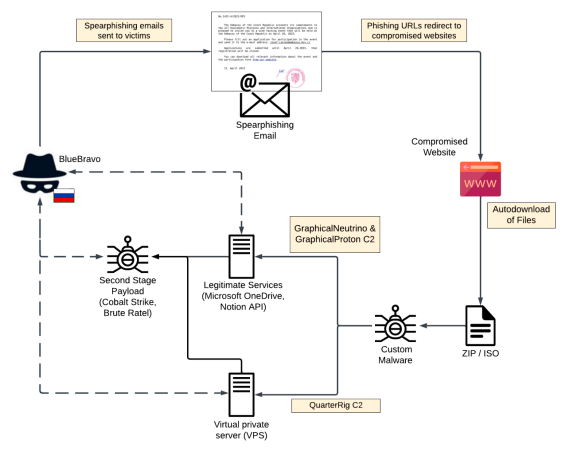
Both GraphicalNeutrino and GraphicalProton serve as loaders, with the latter being staged within ISO or ZIP files delivered via phishing emails. The attackers distribute ISO files containing .LNK files disguised as .PNG images of a BMW car supposedly for sale. When clicked, the .LNK file triggers the GraphicalProton infection chain. The attackers utilize Microsoft OneDrive as their C2 server and periodically poll a folder in the storage service to fetch additional payloads.
The analysis by researchers suggests that BlueBravo prioritizes cyber-espionage efforts against European government sector entities, potentially due to the Russian government’s interest in strategic data during and after the war in Ukraine. Given the ongoing conflict in Ukraine, it is expected that BlueBravo will continue to view government and diplomatic institutions as high-value targets in the foreseeable future. These organizations may provide valuable insights into the decision-making processes of governments allied with Ukraine, which makes them attractive targets for BlueBravo and its Russian intelligence consumers.
Impact
- Information Theft and Espionage
- Exposure of Sensitive Data
- Cyber Espionage
Indicators of Compromise
Domain Name
- te-as.no
- easym6.com
- remcolours.com
- simplesalsamix.com
- sylvio.com.br
- reidao.com
- mightystake.com
- sharpledge.com
- fondoftravel.com
MD5
- 1b371d33e9b5acfa78a478d289b62988
- 0e4e30fe797e02f3f18892b24a6b3087
- 71d92d610cc7d43aabe67cc9c95e9673
- 237e0b3d73022a5bbef796e04943c7c8
- 57770c738da83088a809887396a3871c
- 6852a33758758e9f472ff56531eceb4d
- 138504507a362e6fce66926748c307c9
- e306333093eaf198f4d416d25a40784a
- 4c00d883444c78f19c3a1af191614491
- 68cc826c2c58cb74abe3e5ef2123102c
- 9685dae9ed8d2bf13b66593c1d7cd2eb
- dd2e5debb0ae8b8bccac5c1fbef6bb5a
- 5bcf04c0fb0f62fc5f4b83789477a699
SHA-256
- 9da5339a5a7519b8b639418ea34c9a95f11892732036278b14dbbf4810fec7a3
- 22b037f0a42579b45530bed196dd2b47fd4d4dffb8daa2738581287932794954
- b84d6a12bb1756b69791e725b0e3d7a962888b31a8188de225805717c299c086
- aff3d7f9ebfdbe69c65b8441a911b539b344f2708e5cef498f10e13290e90c91
- c71ec48a59631bfa3f33383c1f25719e95e5a80936d913ab3bfe2feb172c1c5e
- 385973e7777081c81cfe236fcc8b3ebf5e4ae04f16030d525535f6cfe38cae7b
- becbd20a19bab555b92d471b30b8159dfa709e9bc417e5d42d72c94546d9e61c
- 79a1402bc77aa2702dc5dca660ca0d1bf08a2923e0a1018da70e7d7c31d9417f
- 640a08b52623cd8702de066f1f9a6923b18283fc2656137cd9c584da1e07775c
- 6f37579d445639c7dfebb4927fe7f6ea70d25d1127f9d9b5078f8ccd4da36127
- 0e22e6a1dc529008d62287cfddaed53c7f4cc698feec144f00c92594dc76d036
- 02ce47bd766f7489c6326c30351eb9b365f9997de1b2f92924d130fa07e0d82c
- c5209127e65b0465c8a707ca127b067aa8756c1138bd0d3636f71bfbe8fd9bda
SHA-1
- a68d5ff30a25cf033061a74e8c8a34721bcc65a0
- e4846460539e51e3e0f9398b8c215d5bc39e70fe
- f2b87d3a692b7597bdcee8151e5960fc5959dc7b
- e6e37fb4aaa2c45bb6cbc2ebc89a5fd722176f0a
- f38fd42c2646301053618a2cf87fd52c41ff2ed7
- 6d1a3abcb1d27ea40b046701e02351b1c4841e26
- 28891e267e320d38b570437ff283abce6cc19d55
- fd45d69af00fdff334515523aad22bbd15b4981d
- a88cb3524246ff1a0c7e6a2afa1d28989b5cfc7f
- cd1558626e38b1d12332de4e12104c7e57466e55
- fbcc038644cd9a564902e8ff681063cb1a80538c
- 28a5dbdf03612d0725ab6756e0f2e9a6cad8e889
- dcf27c3002f343ef6cafb732c2f779ea1aaa0ce5
Remediation
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls
- Emails from unknown senders should always be treated with caution. Never trust or open links and attachments received from unknown sources/senders.
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Conduct regular cybersecurity awareness training for all employees, especially those handling sensitive information. Educate them on recognizing phishing emails and suspicious attachments to prevent initial infection.
- Deploy robust email filtering solutions to detect and block phishing attempts and malicious attachments, reducing the chances of the malware reaching the end-users.
- Implement network traffic monitoring and intrusion detection systems (IDS) to identify suspicious activity and unusual connections indicative of a potential intrusion.
- Limit access to administrative accounts and portals to only relevant personnel and make sure they are not publicly accessible.
- Enable MFA for all accounts, especially for remote access and critical systems.
- Maintain daily backups of all computer networks and servers.
- Deploy continuous monitoring solutions that provide real-time visibility into network activities and behaviors, enabling swift detection and response to potential threats.








