

Rewterz Threat Advisory – CVE-2023-32437 – Apple iOS and iPadOS Vulnerability
July 25, 2023
Rewterz Threat Alert – An Emerging Ducktail Infostealer – Active IOCs
July 25, 2023
Rewterz Threat Advisory – CVE-2023-32437 – Apple iOS and iPadOS Vulnerability
July 25, 2023
Rewterz Threat Alert – An Emerging Ducktail Infostealer – Active IOCs
July 25, 2023Severity
High
Analysis Summary
Ransomware attacks are on the rise, posing significant challenges for organizations worldwide. A recent investigation by the Incident Response team into the BlackByte 2.0 ransomware attacks exposed the speed and impact of these cyber attacks. The threat actor progressed through the entire attack chain, from initial access to causing disruption, in just five days, severely impacting the victim organization’s operations.
The finding indicates that the threat actor utilized various tools and techniques, ultimately deploying the BlackByte 2.0 ransomware. The techniques involved exploiting unpatched Microsoft Exchange Servers exposed on the internet, deploying web shells for remote access, using living-off-the-land tools for persistence and reconnaissance, employing Cobalt Strike beacons for command and control, process hollowing, and utilizing custom-developed backdoors and data collection tools for persistence and exfiltration.
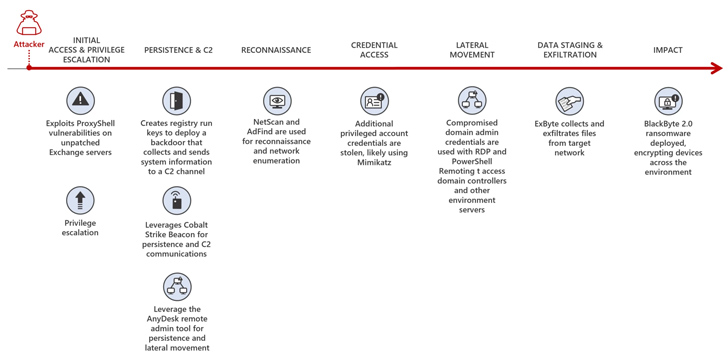
The forensic analysis revealed the attacker’s approach at each stage of the attack chain. They gained initial access by exploiting ProxyShell vulnerabilities in unpatched Exchange Servers, eventually obtaining system-level privileges and creating web shells for control. They maintained persistence through backdoor registry run keys and utilized the AnyDesk remote administration tool to blend into the network.
The threat actor engaged in reconnaissance using tools like NetScan and AdFind to enumerate the network and collect credentials via likely usage of Mimikatz. After lateral movement through RDP and PowerShell remoting, they staged and exfiltrated data using a custom tool called ExByte. The ransomware itself, BlackByte 2.0, exhibited capabilities such as antivirus bypass, process hollowing, modification of Windows Firewall, and destruction of volume shadow copies.
The increasing surge in ransomware attacks calls for immediate action from organizations worldwide. In response to the investigation’s findings, Microsoft offers practical recommendations. Organizations are urged to implement robust patch management procedures, ensuring critical security updates are applied promptly. Enabling tamper protection is also essential as it strengthens security solutions against malicious attempts to disable or bypass them.
By taking these measures, organizations can bolster their defenses and mitigate the risks posed by ransomware attacks, helping protect their valuable data and systems from these cyber threats.
Impact
- File Encryption
- System Infiltration
- Remote Access
- Financial Loss
Indicators of Compromise
MD5
- 1eee62ae28e6b20f4100ce4a02fedd94
- a62d5c8ef4d626febfcd2c00898c6c27
- 2d8e4f38b36c334d0a32a7324832501d
- 23c893984e388278e7996b70f220aa28
- 5483da573c6a239f9a5d6e6552b307b0
SHA-256
- 4a066569113a569a6feb8f44257ac8764ee8f2011765009fdfd82fe3f4b92d3e
- 5f37b85687780c089607670040dbb3da2749b91b8adc0aa411fd6280b5fa7103
- 01aa278b07b58dc46c84bd0b1b5c8e9ee4e62ea0bf7a695862444af32e87f1fd
- 1b9badb1c646a19cdf101ac4f6fdd23bc61eaab8c9f925eb41848cea9fd0738e
- f157090fd3ccd4220298c06ce8734361b724d80459592b10ac632acc624f455e
SHA-1
- ff1b176f0885c730516e798aaa14cff694f34a3b
- 854e020efefbf393e04d897b6b0b83ef92fd2db8
- f6f11ad2cd2b0cf95ed42324876bee1d83e01775
- 13c6c472a1dfcb2cc03bd65a3f122e8230255821
- c2eaca8799d335954ef3d9a1867ec1b629ca4f1a
URL
- https://myvisit.alteksecurity.org/t
- https://temp.sh/szAyn/sys.exe
Remediation
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls
- Refer to the Microsoft security update CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207 for patch, upgrade or suggested workaround information.
- Implement a robust patch management process to ensure timely application of security updates. Prioritize patching for internet-exposed devices to address known vulnerabilities that attackers may exploit.
- Utilize advanced vulnerability and configuration assessment tools for Vulnerability Management to understand and assess your organization’s cyber exposure.
- Deploy an endpoint detection and response solution to gain real-time visibility into malicious activities across your network. This helps detect and respond to potential threats promptly.
- Keep antivirus protections up to date by enabling cloud-based protection and ensuring your antivirus solution is configured to block emerging threats effectively.
- Block inbound traffic from TOR exit nodes and unauthorized public VPN services that might be used for malicious activities.
- Limit administrative privileges to authorized personnel only. This prevents unauthorized changes and helps reduce the risk of attackers gaining elevated access to critical systems.








