

Rewterz Threat Alert – APT group Kimsuky – Active IOCs
June 8, 2021
Rewterz Threat Alert – Gootkit Trojan Active- IOCs
June 8, 2021
Rewterz Threat Alert – APT group Kimsuky – Active IOCs
June 8, 2021
Rewterz Threat Alert – Gootkit Trojan Active- IOCs
June 8, 2021Severity
High
Analysis Summary
Confucius APT, a threat actor/group primarily targeting government sectors in South Asia is active again in the region and targeting Pakistani officials in their latest decoy campaign deploying their Warzone RAT. the threat actor is trying to circumvent attacks with decoys that deliver the next stage payload via the template injection technique and a short C2 TTL (Time to Live).
A Warzone RAT was sent via malicious emails in the attack kill chain of the decoy document which indicates the capabilities of the cruise missiles implications for the Indian AIrforce and army. This is a very well-planned activity that is well thought and the document was crafted by the attacker group to entice the victims or targets into opening a file related to the ongoing India China border tension.

The document used template injection to download the next stage RTF exploit that downloaded the final stage Warzone payload using a DLL embedded in the RTF exploit.
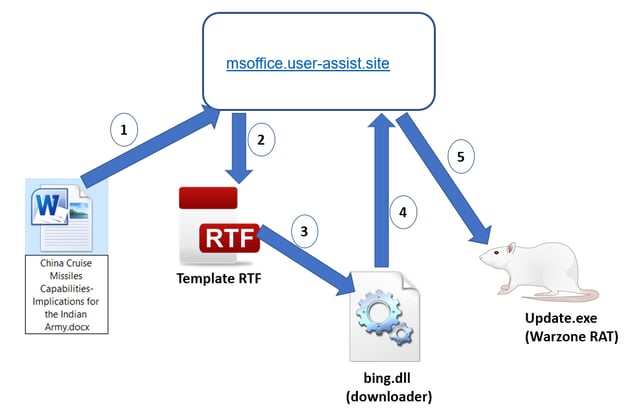
The various phases of the attack are as follows:
- Victim opens the Word document
- Document downloads template RTF
- Exploit in RTF is triggered and bing.dll is dropped and executed
- Bing.dll downloads Warzone RAT
The second decoy was observed in November 2020. Interestingly, this decoy had the same hash of the next stage RTF and the DLL payloads used in the first decoy document.

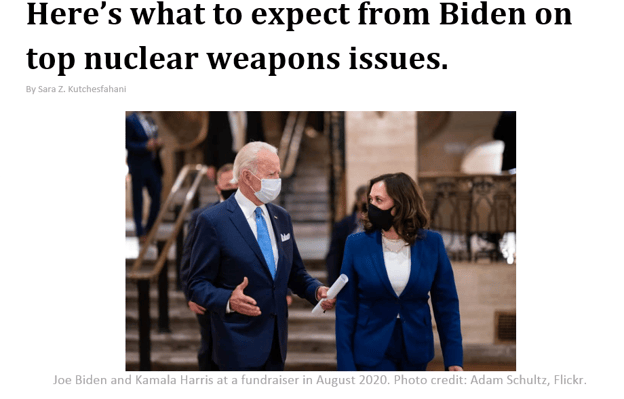
Another decoy document was found as an attachment which focuses on the Biden administration and what to expect from them in terms of nuclear weapon issues. The DLL file connected to the same C2 and contained the same PDB path in the above two documents.
Impact
- Information theft and espionage
Indicators of Compromise
Filename
- Testing[.]docx
- Suparco Vacancy Notification[.]docx
- China Cruise Missiles Capabilities-Implications for the Indian Army[.]docx
MD5
- c2528d0f946970e86e6ab9505a36d7b9
- 37f78dd80716d3ecefc6a098a6871070
- 9f54962d644966cfad560cb606aeade2
- 912141bb5b4020c2cc75a77c37928a3b
- 915f528202b036dc5d660f44c187f121
- c2528d0f946970e86e6ab9505a36d7b9
- dd37460956de36c0dabb72a603d5f86c
- 5554be4fea7ae659b067550228788bdf
- b56c98106376f4704d5c45ba8c427c1b
- 346dc04c2c3627d3726c65f86ff495d0
- deef1c2c9a63c76fa088bf4b2e62ce87
SHA-256
- a3cd781b14d75de94e5263ce37a572cdf5fe5013ec85ff8daeee3783ff95b073
- 59ccfff73bdb8567e7673a57b73f86fc082b0e4eeaa3faf7e92875c35bf4f62c
- b9b5a9fa0ad7f802899e82e103a6c2c699c09390b1a79ae2b357cacc68f1ca8e
- 2f5fc653550b0b5d093427263b26892e3468e125686eb41206319c7060212c40
- 07277c9f33d0ae873c2be3742669594acc18c7aa93ecadb8b2ce9b870baceb2f
- a3cd781b14d75de94e5263ce37a572cdf5fe5013ec85ff8daeee3783ff95b073
- 686847b331ace1b93b48528ba50507cbf0f9b59aef5b5f539a7d6f2246135424
- 1c41a03c65108e0d965b250dc9b3388a267909df9f36c3fefffbd26d512a2126
- 59cd62ad204e536b178db3e2ea10b36c782be4aa4849c10eef8484433a524297
- 3ce48f371129a086935b031333387ea73282bda5f22ff78c85ee7f0f5e4625fe
- ea52d6358d53fc79e1ab61f64cb77bb47f773f0aa29223b115811e2f339e85f5
SHA1
- 0128cc716adf8387563c146dd6be501824d1d527
- 6b0d33cdca77154ce11a5647e2ffdcc77b210ff7
- f44d327b2d8109f9b2b5cfcf7fdc725f37dee803
- 8c30786f4f2de4fb3d9ca8ad8a542a078d3e3ff7
- bcbf14769495126763ca3b73c486b38e0a87116a
- 0128cc716adf8387563c146dd6be501824d1d527
- 78d1f25c0bbdd58be218532b5af95c4af218b271
- bc874ccd8760f4de56cd767987977d70f3bdf759
- b205b08b47ce6bd15a20fd91a5936fa7dd8804dc
- 026cf3b25e3efc5169ca0ccd916b112cd4873bf3
- 38260c47f8ae19f91e15c1c9a5e654423a9234a2
Remediation
- Block all threat indicators at your respective controls.
- Search for IOCs in your environment.








