

Rewterz Threat Alert – Malspam Pushes the Information Stealer ‘Lampion’
December 30, 2019
Rewterz Threat Alert – BRONZE PRESIDENT Active in South and East Asia
December 31, 2019
Rewterz Threat Alert – Malspam Pushes the Information Stealer ‘Lampion’
December 30, 2019
Rewterz Threat Alert – BRONZE PRESIDENT Active in South and East Asia
December 31, 2019Severity
Medium
Analysis Summary
Zeppelin is the newest member of the Delphi-based Ransomware-as-a-Service (RaaS) family initially known as Vega or VegaLocker. Zeppelin appears to be highly configurable and can be deployed as an EXE, DLL, or wrapped in a PowerShell loader. The samples are spread via malspam and are hosted on water-holed websites and, in the case of PowerShell, on Pastebin. There are reasons to believe at least some of the attacks were conducted through MSSPs, which would bear similarities to another recent highly targeted campaign that used a ransomware called Sodinokibi.
There is a major shift in their targets from Russian-speaking to Western countries, as well as differences in victim selection and malware deployment methods. Earlier this month, the ransomware targeted healthcare and IT.
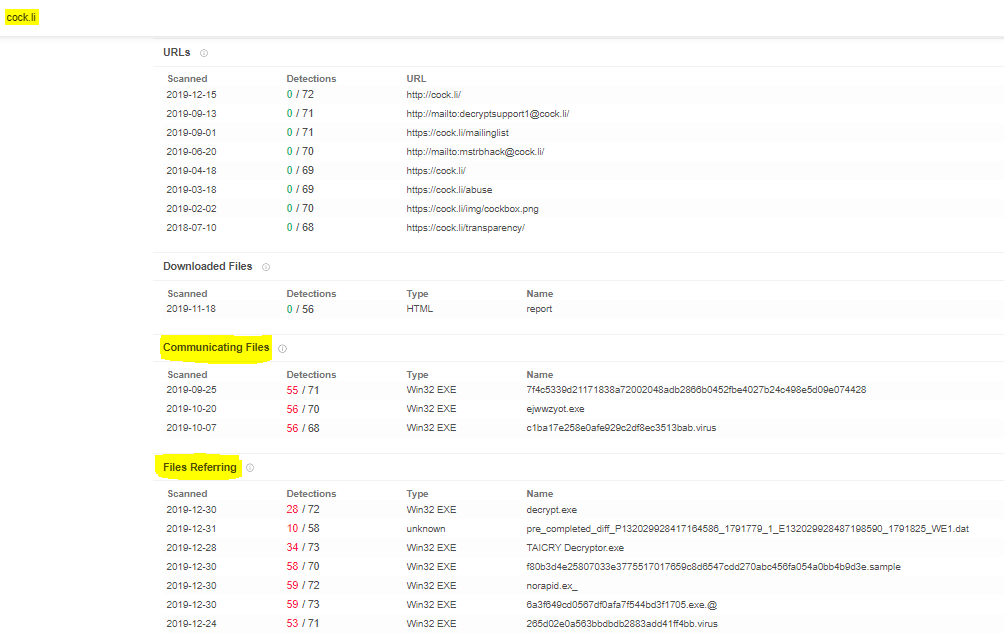
Indicators of compromise are given below. However, the URLs for this domain were found clean while the files communicating with it were found to be malicious.
Impact
Files encryption
Indicators of Compromise
Domain Name
- tutanota.com
- protonmail.com
- iplogger.ru
- iplogger.org
- firemail.cc
- yandex.direct
- ntdetect.com
- torbox3uiot6wchz.onion
- cock.li (see evidence above)
From Email
- bad_sysadmin@protonmail.com
- Vsbb@firemail.cc
- Vsbb@tutanota.com
- buratino@firemail.cc
- buratino2@tutanota.com
- ran-unlock@protonmail.com
- ranunlock@cock.li
- buratin@torbox3uiot6wchz.onion
MD5
- 1d6ce900a8b2bf19fc993cad4f145fa8
- 968503a249052f5d214d3d368fe49e0c
- 36ebf768b89bf5bf329b5e4d17ed99e1
- f8a5d94ebd48bd371cb4d751507319e9
- 386157f4cab9327d01a7210da9237ef0
- c0e88cbb811aa4a59f79c392120c559a
SHA-256
- e22b5062cb5b02987ac32941ebd71872578e9be2b8c6f8679c30e1a84764dba7
- 04628e5ec57c983185091f02fb16dfdac0252b2d253ffc4cd8d79f3c79de2722
- 4894b1549a24e964403565c61faae5f8daf244c90b1fbbd5709ed1a8491d56bf
- 39d8331b963751bbd5556ff71b0269db018ba1f425939c3e865b799cc770bfe4
- d61bd67b0150ad77ebfb19100dff890c48db680d089a96a28a630140b9868d86
- 1f94d1824783e8edac62942e13185ffd02edb129970ca04e0dd5b245dd3002bc
URL
- http://iplogger.org/1wF9i7.jpeg
- http://iplogger.org/1syG87
- http://iplogger.org/1Hpee7.jpeg
- http://iplogger.org/1HVwe7.png
- http://iplogger.org/1HCne7.jpeg
- http://iplogger.org/1H7Yt7.jpg
Remediation
Block the threat indicators at their respective controls.








