

Rewterz Threat Alert – Phishing Campaign Linked to Cobalt Group
December 12, 2019
Rewterz threat Advisory – CVE-2019-18257 – Advantech DiagAnywhere Server Remote Code Execution Vulnerability
December 13, 2019
Rewterz Threat Alert – Phishing Campaign Linked to Cobalt Group
December 12, 2019
Rewterz threat Advisory – CVE-2019-18257 – Advantech DiagAnywhere Server Remote Code Execution Vulnerability
December 13, 2019Severity
Medium
Analysis Summary
A new variant of the VegaLocker/Buran Ransomware called Zeppelin has been spotted infecting U.S. and European health and IT companies via targeted installs. This ransomware family was promoted as Ransomware-as-a-Service (RaaS) in May 2019 on Russian malware and hacker forums. Affiliates who joined the RaaS would earn 75% of the ransom payment, while the Buran operators would earn 25%.
In some of the attacks, the attackers targeted MSPs in order to further infect customers via management software. It is not known exactly how the Zeppelin ransomware is being distributed, but it is likely through Remote Desktop servers that are publicly exposed to the Internet.
The ransomware will first begin to terminate various processes including ones associated with database, backup, and mail servers. When encrypting files, the ransomware will not append an extension and the file name will remain the same. It will, though, include a file marker called Zeppelin that may be surrounded by different symbols depending on the hex editor and character format you are using.
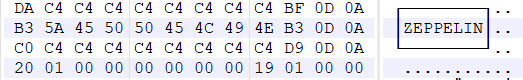
While encrypting files, it will create ransom notes named !!! ALL YOUR FILES ARE ENCRYPTED !!!.TXT that contain information regarding what has happened to the victim’s files. These notes will also contain email addresses that the victim can contact for payment instructions or to test decrypting one file for free. Below is the ransom note found on victim’s system.
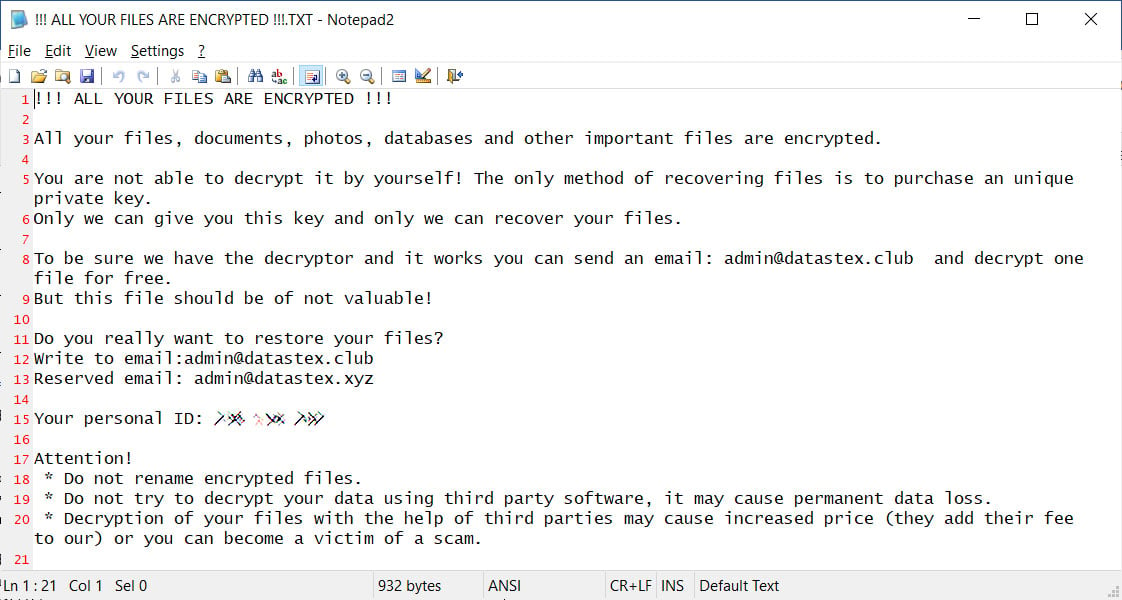
Impact
Files Encryption
Indicators of Compromise
Domain Name
- iplogger[.]org
- cock[.]li
- firemail[.]cc
- tutanota[.]com
SHA-256
- d61bd67b0150ad77ebfb19100dff890c48db680d089a96a28a630140b9868d86
- 1f94d1824783e8edac62942e13185ffd02edb129970ca04e0dd5b245dd3002bc
- e22b5062cb5b02987ac32941ebd71872578e9be2b8c6f8679c30e1a84764dba7
- 4894b1549a24e964403565c61faae5f8daf244c90b1fbbd5709ed1a8491d56bf
- 04628e5ec57c983185091f02fb16dfdac0252b2d253ffc4cd8d79f3c79de2722
- 39d8331b963751bbd5556ff71b0269db018ba1f425939c3e865b799cc770bfe4
URL
- http[:]//iplogger.org/1wF9i7.jpeg
- http[:]//iplogger.org/1syG87
- http[://iplogger.org/1Hpee7.jpeg
- http[:]//iplogger.org/1HVwe7.png
- http[:]//iplogger.org/1HCne7.jpeg
- http[:]//iplogger.org/1H7Yt7.jpg
Remediation
Block the threat indicators at their respective controls.








