

Rewterz Threat Alert – GoMiner spreads via public cloud storage providers
January 24, 2020
Rewterz Threat Advisory – CVE-2020-3142 – Cisco Webex Meetings Suite and Cisco Webex Meetings Online Unauthenticated Meeting Join
January 27, 2020
Rewterz Threat Alert – GoMiner spreads via public cloud storage providers
January 24, 2020
Rewterz Threat Advisory – CVE-2020-3142 – Cisco Webex Meetings Suite and Cisco Webex Meetings Online Unauthenticated Meeting Join
January 27, 2020Severity
High
Analysis Summary
A new module for the TrickBot trojan has been discovered that targets the Active Directory database stored on compromised Windows domain controllers.Once TrickBot is installed, it will harvest various information from a compromised computer and will then attempt to spread laterally throughout a network to gather more data.
TrickBot steals an Active Directory database to harvest login credentials, we first need to give a bit of background about a special file called ntds.dit.
Inside this folder is a file called ntds.dit, which is a database that contains all Active Directory services information such as users, passwords, groups, computers, etc.
As this information is sensitive, Windows encrypts the data using a BootKey stored in the System hive of the Registry. As the ntds.dit is always opened by the domain controller, it also not possible to access it normally using standard file operations.
To be able to work with the ntds.dit database while it is open, Windows domain controllers have a tool called ntdsutil that allows administrators to perform database maintenance.
Using ntdsutil, administrators can perform the “ifm” (Install from Media) command to create a dump of the Active Directory. This command is meant to be used to create installation media that can quickly set up new Domain controllers without having to wait for the Active Directory to replicate.
TrickBot steals the Active Directory
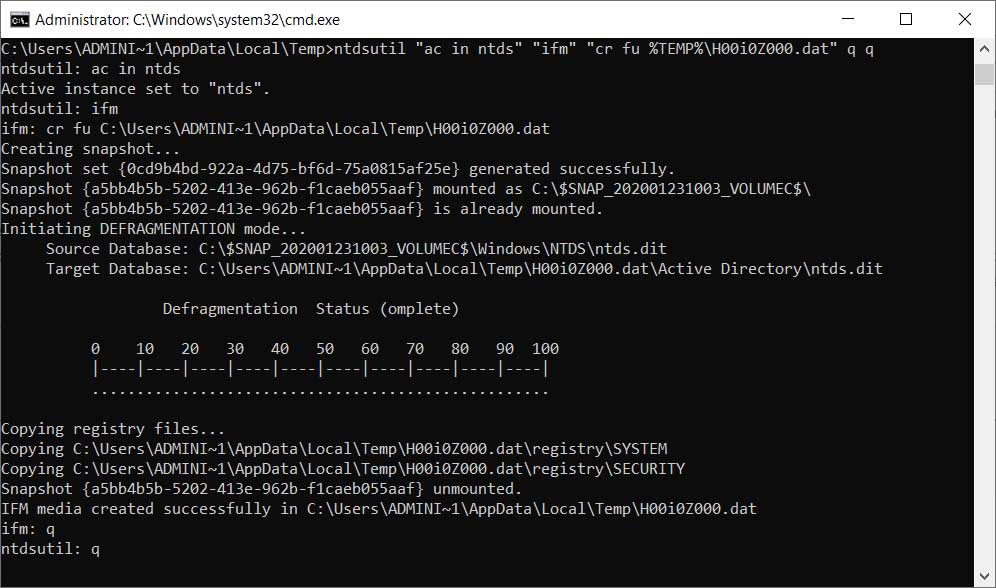
TrickBot’s new ADll module takes advantage of the “Install from Media” command to dump the Active Directory database and various Registry hives to the %Temp% folder. These files are then compressed and sent back to the attackers.
When executed, the commands will dump the Active Directory database as well as the SAM, Security, and SYSTEM hives.
When done, Nemes says the module will check if the files exist, compress them, and then exfiltrate the files back to the attacker’s servers.
Impact
- Credential theft
- Exposure of sensitive information
Remediation
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/attachments sent by unknown senders.








