

5 Cyber Security Measures to Avoid Getting Hacked
October 3, 2019
Rewterz Threat Alert – FTCode PowerShell Ransomware Resurfaces in Spam Campaign
October 3, 2019
5 Cyber Security Measures to Avoid Getting Hacked
October 3, 2019
Rewterz Threat Alert – FTCode PowerShell Ransomware Resurfaces in Spam Campaign
October 3, 2019Severity
High
Analysis Summary
A malicious campaign targeting corporations from all over the world was observed while using a combination of pages hosted on Bit.ly, BlogSpot, and Pastebin to deliver Azorult and RevengeRAT malware.
The command-and-control (C2) storage infrastructure used by the campaign dubbed MasterMana by Prevailion researchers who spotted it allows the threat actors behind the attacks to conceal malicious traffic from security solutions.
Based upon exhibited tactics, techniques, and procedures (TTPs), we have associated it — with moderate confidence — to the ‘Gorgon Group’, a well known group active for numerous years and attributed with multiple ongoing malicious campaigns.
The group is known to have been behind various cyber-crime and cyber-espionage attacks, including but not limited to campaigns targeting government entities in the U.S., Europe, and Asia.
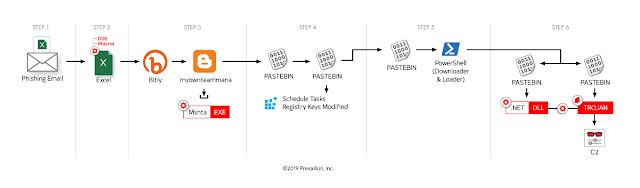
This operation, which began as early as December of 2018, appears financially motivated, given the seemingly indiscriminate targeting of business email addresses via phishing and the inclusion of specific functions to steal information associated with cryptocurrency wallets.
The malware is delivered onto the targets’ computers using a phishing campaign that uses emails bundling malicious Microsoft Excel document attachments which, once opened, would drop a VBS script payload.
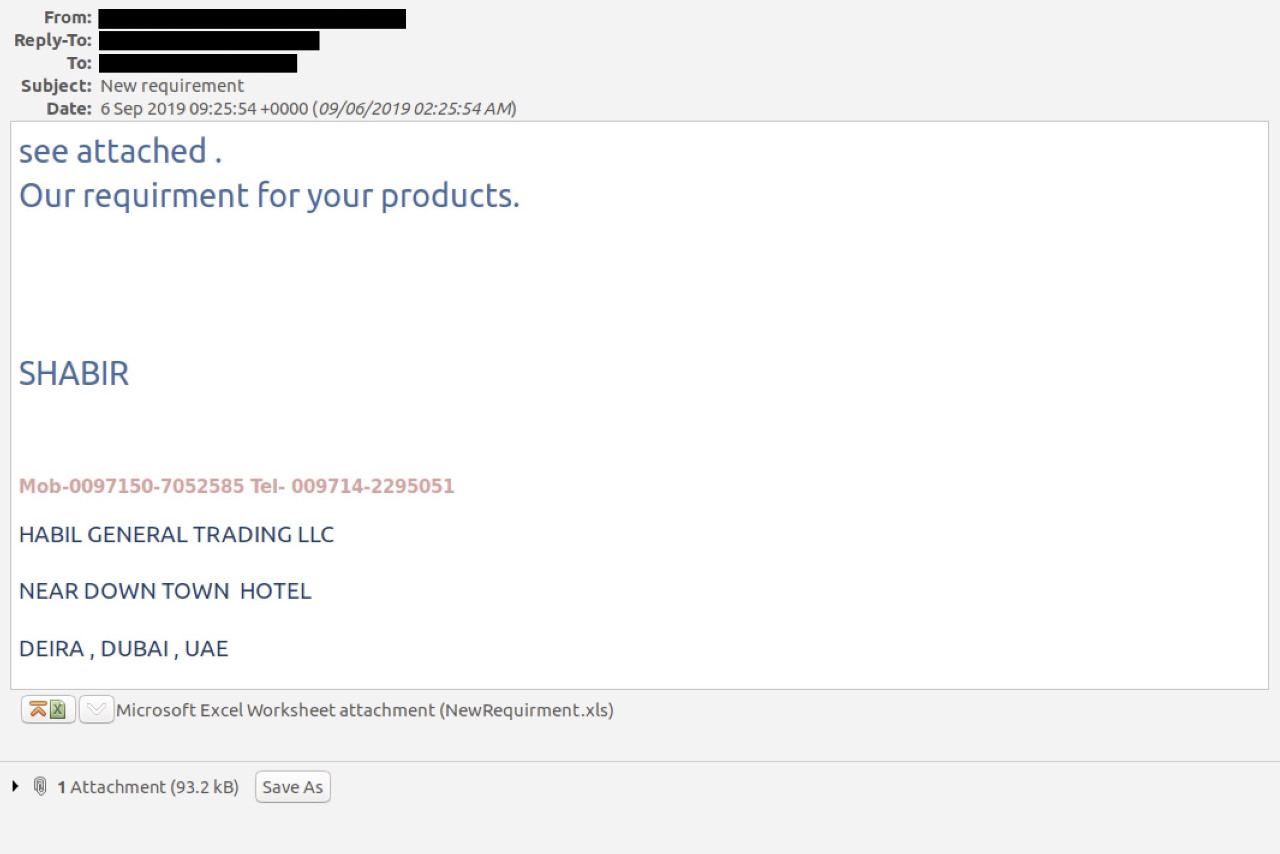
The script opens a BlogSpot site that launches the legitimate Mshta (Microsoft HTML Application Host) utility to open a second-stage payload hosted on Pastebin, and designed to kill any running Word, Excel, Powerpoint, and Publisher processes and to set up scheduled tasks and registry keys for persistence.
Impact
- Credentials theft
- Financial loss
Remediation
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/ attachments sent by unknown senders.








