

Rewterz Threat Alert – Dexphot Malware Hijacked 80K+ Windows Computers to Mine Cryptocurrency
November 29, 2019
Rewterz Threat Alert – CStealer Password Stealer Sends Stolen Data to a MongoDB Database
December 2, 2019
Rewterz Threat Alert – Dexphot Malware Hijacked 80K+ Windows Computers to Mine Cryptocurrency
November 29, 2019
Rewterz Threat Alert – CStealer Password Stealer Sends Stolen Data to a MongoDB Database
December 2, 2019Severity
Medium
Analysis Summary
Malware distributors are sending out holiday themed emails to distribute the Emotet Trojan and other malware. Thanksgiving Day greeting cards and office closing notices with last minute invoices embedded with malware are being pushed via malspam. Users who fall for the emails and open the attached word documents will be left with a Windows computer infected with a password-stealing Trojan and possibly other malware.
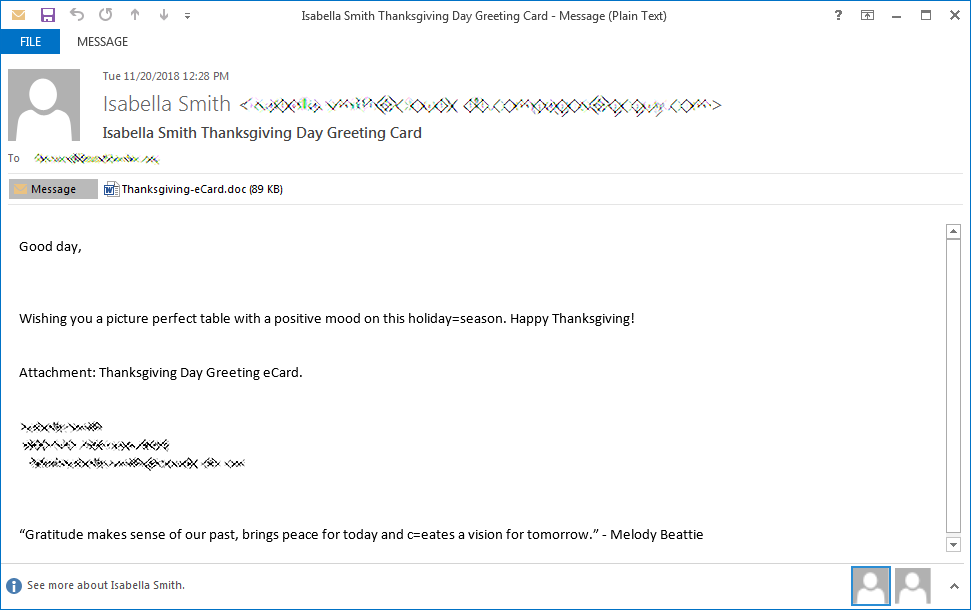
Another malspam campaign pretends to be responding to a previous query email and drops malware.
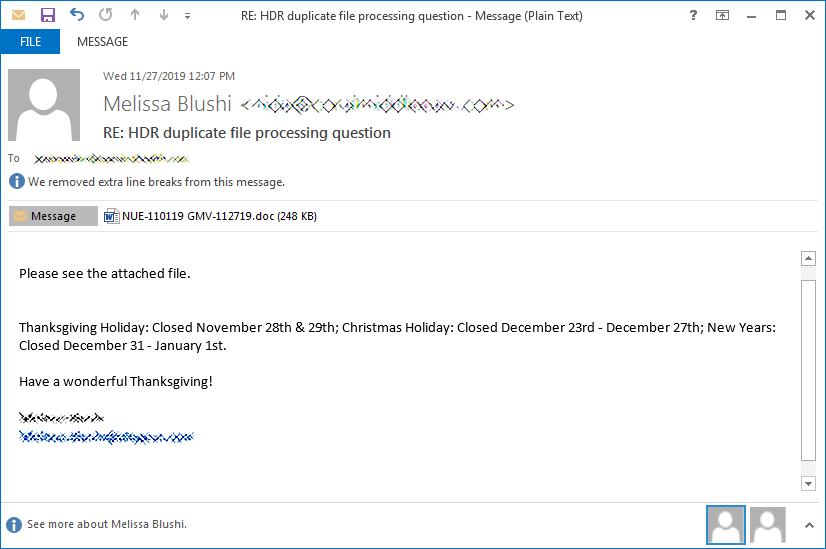
This email template also tells the user that they are closed for the Thanksgiving holiday and upcoming future holidays. This may be done to create a sense of urgency and to have the recipient open the email. Holiday themed lures coupled with the holiday business closures are likely to make users slip and open the attachments. These Word documents contain obfuscated macros and demand the users to click on ‘Enable macros”, “edit content” or “Enable content”. This will either download malware from a remote host or extract it from an embedded payload. For the Emotet malspam, the malware will be extracted to a folder under the %LocalAppData% folder and then executed.
Impact
- Credential Theft
- Unauthorized Remote Access
- Ransomware infection
Indicators of Compromise
Filename
Thanksgiving-eCard.doc
MD5
51f5030a078f61a092f6876bca6efc53
SHA-256
a422f8d486c0f16d7629674570d187c9bcedd262c607ccc77709f9ab431de179
SHA1
b4c2e1c721c4287014bcb5e02700afb667b998fd
Remediation
- Block the threat indicators at their respective controls.
- Do not respond to holiday lures.
- Do not download files coming in untrusted emails.
- Do not enable macros without validating the legitimacy of their source.








