

Rewterz Threat Alert – Mastercard Priceless Specials Members Data Shared Online
September 3, 2019
Rewterz Threat Alert – Fake BleachBit Website Distributes AZORult Info Stealer
September 3, 2019
Rewterz Threat Alert – Mastercard Priceless Specials Members Data Shared Online
September 3, 2019
Rewterz Threat Alert – Fake BleachBit Website Distributes AZORult Info Stealer
September 3, 2019Severity
High
Analysis Summary
A distributor for the Sodinokibi Ransomware is hacking into WordPress sites and injecting JavaScript that displays a fake Q & A forum post over the content of the original site. This fake post contains an “answer” from the site’s “admin” that contains a link to the ransomware installer.
As security software and people become more aware of the methods that are used to distribute ransomware and malware, affiliates need to come up with craftier methods to infect their victims.
Such is the case with a new distribution method that overlays a fake Questions and Answers forum on top of the content of a hacked site. This fake forum post will contain information related to the content of the page that the user is visiting, so it appears that the answer and link offered by the admin is legitimate.
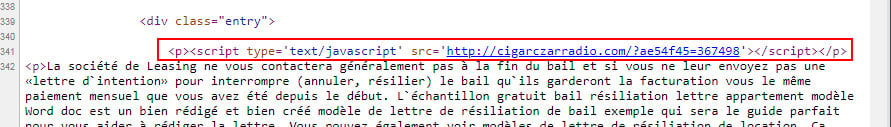
Similar to the older EITest Chrome HoeflerText Font Update attack, the affiliate is hacking into sites so that it injects a JavaScript script into the HTML as shown below. The injected URL will be active to all visitors, but will only contain data if the user is visiting for the first time or has not been to the site in a certain amount of time.
When someone visits the site for the first time, the script will cause a fake French Questions and Answers forum post to display over the content as shown below.
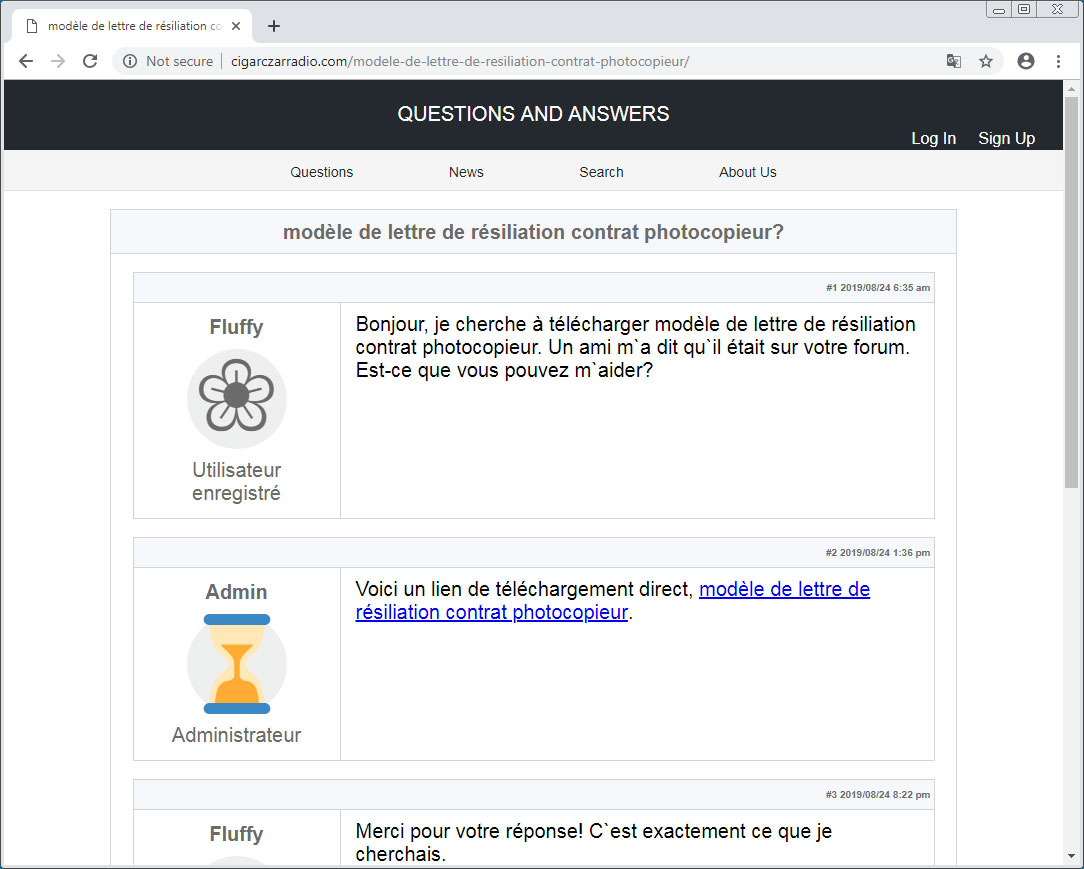
To the user, the above looks like the normal site as the content of the fake forum post is related to the content of the hacked page, but in reality is just an overlay created by the script.
If a user refreshes the page again, the script will not fire and the normal page will be shown as seen in the demonstration video at the end of the article.
If a user does not refresh the page, though, it will appear as if another visitor posted a question in French to the site about a “termination contract” for a photocopier model.
Impact
File encryption
Remediation
Always be suspicious about emails sent by unknown senders.
Do not respond to unexpected emails and do not click on links attached in unexpected emails.








