

Rewterz Threat Advisory – ICS: Moxa MB3xxx Series Protocol Gateways
February 26, 2020
Rewterz Threat Alert – Trickbot Targets Windows 10 Users by Abusing ActiveX Control
March 2, 2020
Rewterz Threat Advisory – ICS: Moxa MB3xxx Series Protocol Gateways
February 26, 2020
Rewterz Threat Alert – Trickbot Targets Windows 10 Users by Abusing ActiveX Control
March 2, 2020Severity
High
Analysis Summary
A new “Pxj” ransomware. Also known as the “XVFXGW” ransomware, it performs functions common to most ransomware. First, the Recycle Bin is emptied using the SHEmptyRecycleBinW function. Next, a series of commands are executed to prevent recovery of data after encryption, specifically the deletion of volume shadow copies and disabling of the Windows Error Recovery service. These are the commands executed by the ransomware.
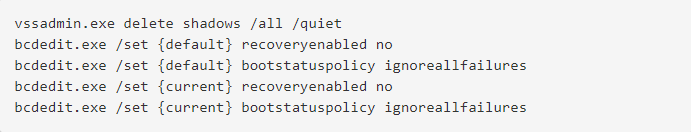
After these tasks are complete, the encryption process begins. AES and RSA are used in combination for encryption. The name “Pxj” is derived from the extension that is appended to encrypted files. The alternative name, “XVFXGW,” is based off of both the mutex that is created, “XVFXGW DOUBLE SET,” and the email addresses listed in the ransom note, “xvfxgw3929@protonmail.com” and “xvfxgw213@decoymail.com”. With encryption complete, the ransom note is dropped as a file named “LOOK.txt” and requests the user contact the operator via email to pay the ransom in exchange for the decryption key.
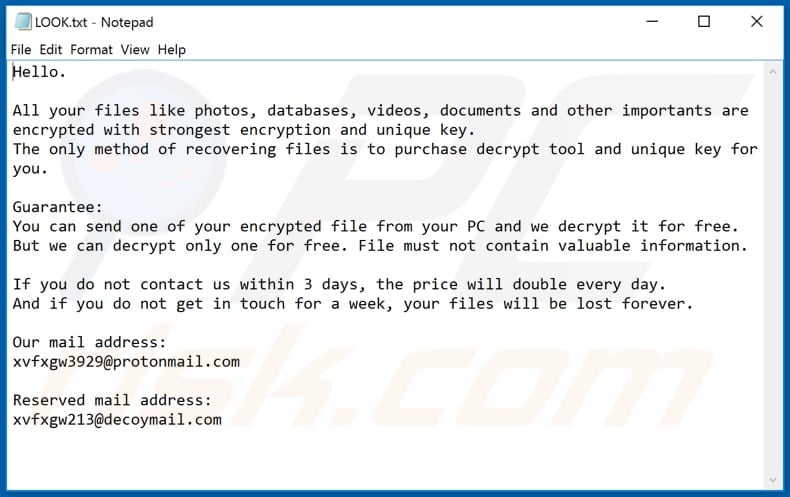
Impact
Files Encryption
Indicators of Compromise
- xvfxgw3929@protonmail[.]com
- xvfxgw213@decoymail[.]com
SHA-256
- 9a4e4211f7e690ee4a520c491ef7766dcf1cc9859afa991e15538e92b435f3a1
- 58673f5c9344f510703ffda908c7e7830f36905015529ab629479c6bf44236e9
Remediation
- Block all threat indicators at your respective controls.
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/attachments sent by unknown senders.








