

Rewterz Threat Advisory – CVE-2019-1579 – Palo Alto PAN-OS code execution vulnerability
July 23, 2019
Rewterz Threat Alert – AZORult Malware Stealing Credentials
July 23, 2019
Rewterz Threat Advisory – CVE-2019-1579 – Palo Alto PAN-OS code execution vulnerability
July 23, 2019
Rewterz Threat Alert – AZORult Malware Stealing Credentials
July 23, 2019Severity
Medium
Analysis Summary
Researchers uncovered the framework, which features three separate stages that ultimately install a malicious browser extension designed to perform fraudulent AdSense impressions, as well as generate likes on YouTube videos and watch hidden Twitch streams.
The framework is designed to pad statistics on social sites and ad impressions, creating revenue for its operators who are using a botnet to attack the content and advertising platforms by spreading the malware and targeting browsers including Google Chrome, Mozilla Firefox, and Yandex’s browser.
Stage-by-Stage
Once a browser is infected, the initial stage of the framework executes. The installer sets up take-based persistence, either sets up a new browser extension or downloads a module that does so, and checks in on whether the installation was successful.
The installer sets itself up as a task related to Windows Update by creating an XML file on the local disk and executing it as a scheduled task (schtasks).
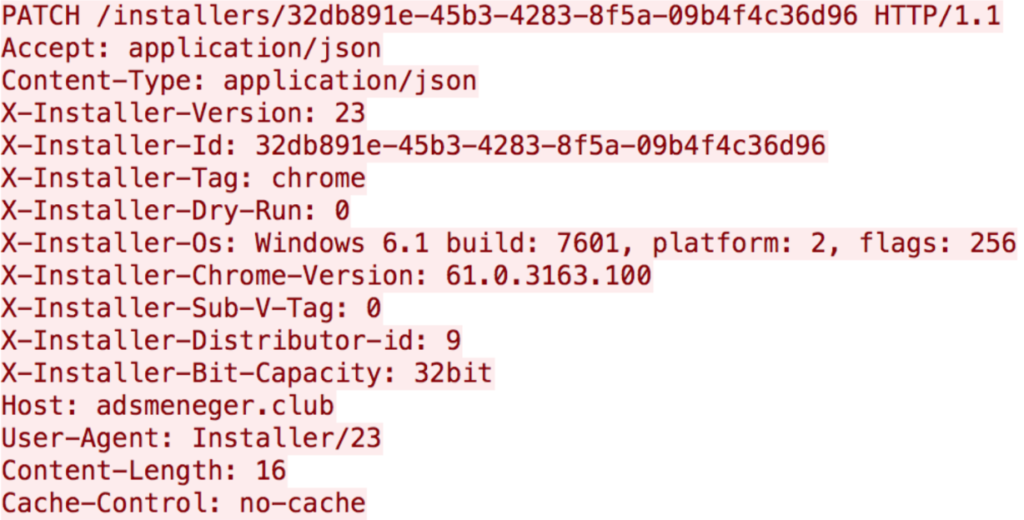
Once that is complete, the installer sets up the extension; an earlier version of the Chrome extension was not encoded, something that was changed in later versions.
Finder: The next component, dubbed Finder, is a module designed to steal browser logins and cookies, package them in .zip files, and send them to the attacker’s command-and-control infrastructure.
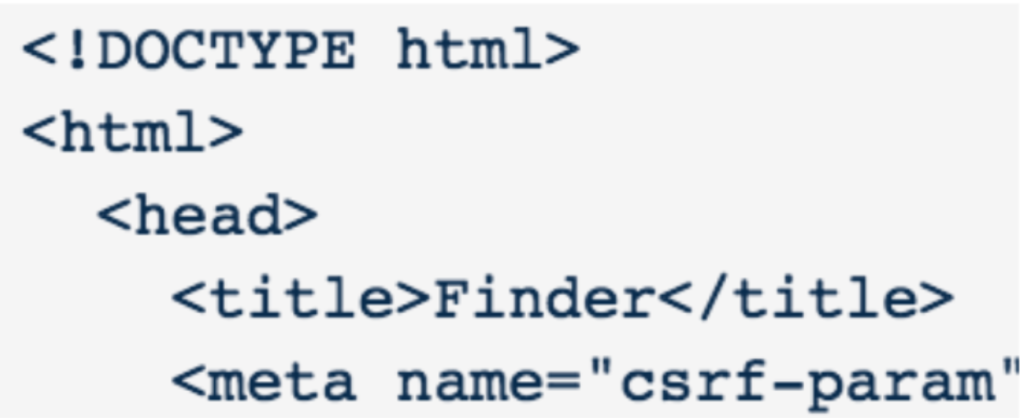
It also talks to a separate C2 panel where it retrieves update binaries instructing it how frequently to check in with compromised bots and send back stolen credentials and cookie data. That data that is posted is in JSON, as is most of the malware’s command-and-control traffic.
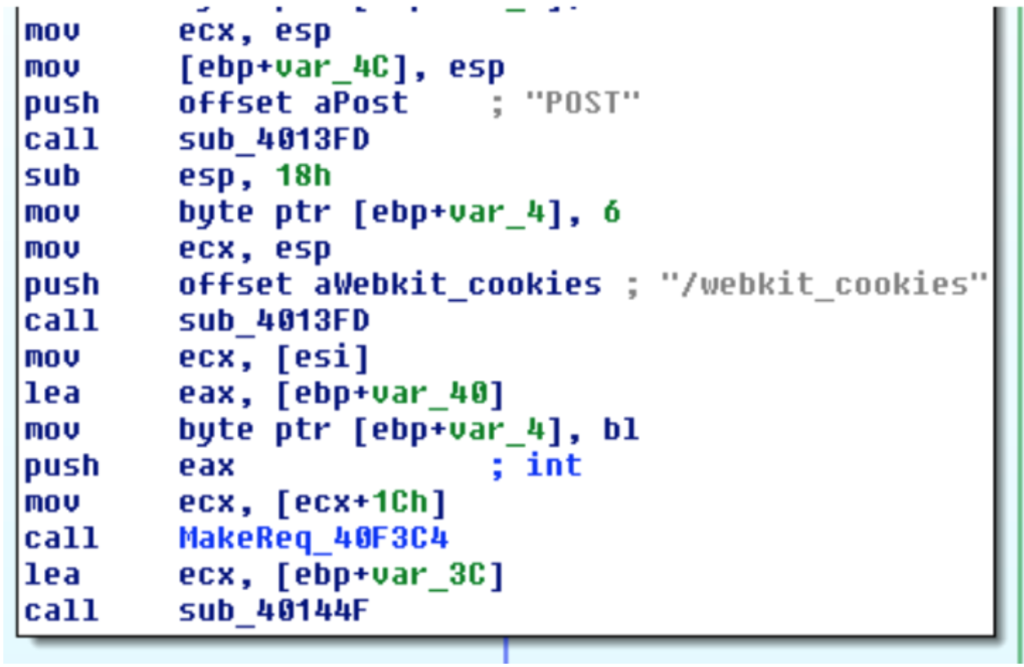
Impact
Credential theft
Indicators of Compromise
URLs
- http[:]//128[.]199[.]202[.]28/uploads/findz
- http[:]//128[.]199[.]202[.]28/uploads/sshd2
- http[:]//138[.]68[.]52[.]55/uploads/findz
- http[:]//138[.]68[.]52[.]55/uploads/so3
Malware Hash (MD5/SHA1/SH256)
- 0fd59d93f53d926a432c47a03374238a010e71a381d8af4d2fcacdabd1d26bbc
- 20f188aaea79a104d945908db570f07e586f2a074431c3bcd2492346837f1001
- 448e81b2149596966b574de5b588bcb30ab1f8dc858439d024f0c2fc7bcb55be
- 45ed59d5b27d22567d91a65623d3b7f11726f55b497c383bc2d8d330e5e17161
- 60bbffaf1a359224a26717b44f6050b3f983c716a294af7d8d5f707c72074ee6
- 7fe9d6d8b9390020862ca7dc9e69c1e2b676db5898e4bfad51d66250e9af3eaf
- c81e470cb3bf320ac1c235bf9799f33e20b6761f15bb9254e6655f8f284adcec
- ea72c36916f53509d42755dfbcb7a5bbdb5616a6ebde122ae242eaea2bb47454
Remediation
- Block all threat indicators at your respective controls.
- Always check the source before downloading any extension.
- Check reviews before installing any extension.
- Always check permissions before installing ant extension.








